February 2014 virus activity review from Doctor Web
Virus reviews | Hot news | All the news | Virus alerts
February 28, 2014
Viruses
According to statistics collected in February 2014 by Dr.Web CureIt!, Trojan.Packed.24524, which spreads in the guise of legitimate software, was the top threat identified. The advertising malware Trojan.LoadMoney.1 ranked second. It was followed by another malicious program designed to display annoying ads and fake web content— Trojan.Triosir.1. This Trojan horse utilizes the Amonitize installer (amonetize.com), while its main modules are implemented as browser extensions. The top twenty most common Trojans detected on computers by Dr.Web CureIt! in February are listed in the table below.
| Name | Quantity | % |
|---|---|---|
| Trojan.Packed.24524 | 64559 | 6.39 |
| Trojan.LoadMoney.1 | 20624 | 2.04 |
| Trojan.Triosir.1 | 16492 | 1.63 |
| Trojan.Siggen5.64541 | 15476 | 1.53 |
| Trojan.LoadMoney.15 | 15082 | 1.49 |
| Trojan.InstallMonster.51 | 14832 | 1.47 |
| Trojan.BPlug.9 | 13494 | 1.33 |
| Trojan.Packed.24814 | 13135 | 1.30 |
| Trojan.DownLoad3.27814 | 11990 | 1.19 |
| Trojan.InstallMonster.38 | 10119 | 1.00 |
| BackDoor.IRC.NgrBot.42 | 8614 | 0.85 |
| BackDoor.Maxplus.24 | 8320 | 0.82 |
| Trojan.Hosts.6815 | 7831 | 0.77 |
| Trojan.InstallMonster.47 | 7384 | 0.73 |
| Trojan.Triosir.2 | 7305 | 0.72 |
| Trojan.Fraudster.524 | 6839 | 0.68 |
| Trojan.InstallMonster.28 | 6054 | 0.60 |
| Trojan.LoadMoney.76 | 6050 | 0.60 |
| Win32.HLLP.Neshta | 5681 | 0.56 |
| Trojan.StartPage.59964 | 5644 | 0.56 |
Botnets
Doctor Web's analysts continue to monitor the growth of the botnet consisting of Windows PCs that have been compromised by the file infector Win32.Rmnet.12, You may recall that this virus can spread without user intervention; it exhibits backdoor behaviour in infected systems and steals confidential information. The growth rate of the first Win32.Rmnet.12 subnet decreased somewhat, with an average of 14,000 newly infected hosts connecting to the network daily versus the 18,000 that were being registered in January. The growth is clearly illustrated in the diagram below.
Win32.Rmnet.12 botnet growth in February 2014
(1st subnet)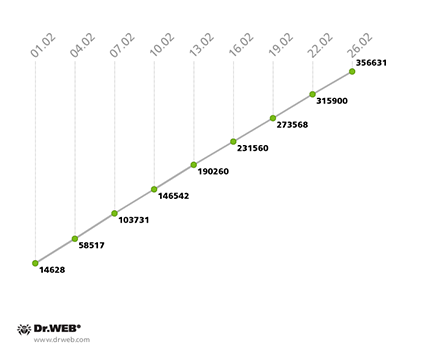
The second Win32.Rmnet.12 subnet also saw its growth rate decline: at the end of January, it was gaining 12,000 new joiners daily, but by the end of February, that figure dropped to 10,000. The second Win32.Rmnet.12 subnet’s growth can be traced in the following diagram.
Win32.Rmnet.12 botnet growth in February 2014
(2nd subnet)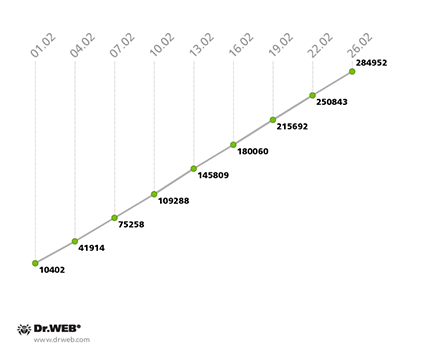
The number of machines on which Dr.Web software has been detecting the malignant module Trojan.Rmnet.19 has remained virtually unchanged. By the end of January, the number was 2,633, and a month later it was almost the same—2,523.
The number of computers infected with the Trojan for MAC OS X, known as BackDoor.Flashback.39, slightly declined: at the end of January the corresponding botnet consisted of 28,160 compromised Macs, but as of February 25, that figure had decreased to 22,773. As before, the USA and Canada remain the leaders in terms of number of infections.
The botnet comprised of devices infected with the first known Android bootkit, dubbed Android.Oldboot.1.origin, is still growing. Doctor Web previously warned users about this threat in one of the news bulletins published on its site. If you recall, this malignant program places one of its components into the protected memory area, so that the malicious code is executed while the operating system is booting up. Thus, part of the Trojan Android.Oldboot is installed as a typical application which further functions as a system service. It connects to a remote server and receives various commands, most notably, to download, install or remove certain applications. Reflashing a device with modified firmware that contains the routines required for the Trojan’s operation is the most likely way this threat is introduced. It should be noted that removing the malware is usually ineffective since the script residing in the protected memory area reinstalls it upon the device’s next reboot.
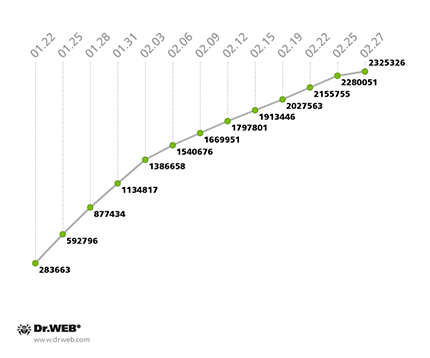
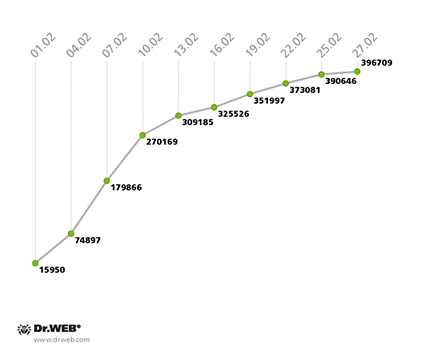
Currently, the botnet consists of approximately 400,000 infected devices whose IMEIs were registered by security researchers from February 1-27. In the past, researchers assessed the number of bots by the number of IP addresses being used to connect to the command and control server. The botnet’s growth, assessed by taking into account the number of IP addresses involved between January 22 and February 27, 2014, is illustrated in the graph below.
In addition to the information about IP addresses, Doctor Web's analysts have now managed to collect statistics concerning the IMEIs of the infected devices. Android.Oldboot's growth rate in February (IMEI statistics) is shown in the diagram below:
Adware Trojan invasion
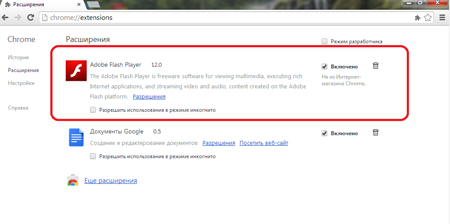
February saw an extremely large number of malignant programs that are designed to replace advertisements on web pages and display annoying ads in browser windows. At the beginning of the month, Doctor Web's security researchers added the signature of the Trojan dubbed Trojan.Admess.1 to the virus databases. This program was disguised as an Adobe Flash player extension for Internet Explorer, Mozilla Firefox, Google Chrome and Opera. The Trojan’s main objective is to replace existing ads with new ones when users are viewing various web pages. A more detailed description of the Trojan can be found in the corresponding publication on Doctor Web's site.
Shortly thereafter, the security researchers discovered another similar program which was dubbed Trojan.Triosir.1. Shortly thereafter, the security researchers discovered another similar program which was dubbed Trojan.Admess.1, Trojan.Triosir.1, and Trojan.Zadved.1 consistently appear at the top of the list of malicious programs detected on computers.
Other February threats
Machines manufactured by Apple didn't escape the attention of cybercriminals either. In February, an entry for the program Trojan.CoinThief was added to the Dr.Web virus databases. This malware is designed to steal electronic currency on machines running Mac OS X. The program monitors traffic to steal personal information processed by Bitcoin and Litecoin mining applications. Also, if Bitcoin-Qt is installed on an infected computer, Trojan.CoinThief modifies this program and steals the private data stored by the application. A small review, devoted to Trojan.CoinThief was published by Doctor Web in the news section of its site.
Another threat, dubbed Trojan.PWS.OSMP.21, was specifically designed to attack the payment terminals of one of Russia’s most popular payment systems. Trojan.PWS.OSMP.21 is distributed as a dynamic link library, which penetrates terminals from infected flash drives.
Trojan.PWS.Papras.4 is another Trojan belonging to the Remote Administration Tool category. This Trojan ensures the operation of several modules on an infected computer: one of them functions as a VNC server, and the other as a Socks Proxy. Another module enables the program to make web injections. An additional module (a grabber) is designed to transmit data entered by users in web forms via popular web browsers. Trojan.PWS.Papras.4 can also execute ten commands which can be issued by criminals from a remote server. More information about this Trojan’s malignant features can be found in a past review published on Doctor Web's site.
Threats to Android
As far as information security is concerned, February turned out to be rather eventful. At the beginning of the month, Doctor Web discovered several dangerous applications, designed to covertly send short messages, embedded in Android firmware. In particular, one of them worked as an audio player that sent out SMS messages containing IMSI identifiers to try to automatically subscribe users to a Chinese online music site. The program, which incorporated an undocumented feature, failed to control the number of sent messages, sending a message whenever it was launched. Thus, users were charged by their mobile operator accordingly.
Another similarly functioning Trojan was embedded in a system utility and also covertly sent out short messages containing device IMEIs. Both threats were classified as SMS Trojans and entered the virus database as Android.SmsSend.1081.origin and Android.SmsSend.1067.origin, respectively.
The Flappy Bird incident didn't go unnoticed by criminals either: shortly after the program was removed from Google Play and the App Store, a number of analogous imitators appeared on the Internet in addition to malicious programs created by enterprising fraudsters claiming that their master works were actually the original, now discontinued, game. In truth, users were offered Android.SmsSend programs that send short messages to premium numbers.
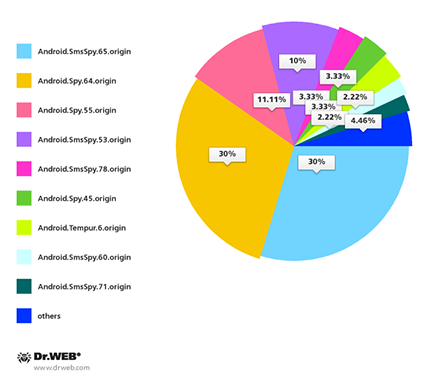
Meanwhile, as far as South Korean users are concerned, the security situation improved somewhat: Doctor Web's security researchers registered 90 incidents involving malware being distributed via SMS spam, a 36.6% drop from the January figure. It should be noted that most Trojans were uploaded by criminals via file hosting services such as Google Drive and Dropbox, a departure from earlier criminals who normally used their own sites.
South Korean users most frequently had to deal with Android.SmsSpy.65.origin and Android.Spy.64.origin (27 incidents occurred involving unwanted SMS containing malware download links) and also with Android.Spy.55.origin (10 incidents) and Android.SmsSpy.53.origin (9 incidents).
The definitions for several commercial spyware programs that apparently are still rather popular on the mobile market were also added to the Dr.Web virus databases during the last full month of winter.
Malicious files detected in mail traffic in February
| 01.02.2014 00:00 - 28.02.2014 17:00 | ||
| 1 | Trojan.Inject2.23 | 0.81% |
| 2 | Trojan.DownLoader9.19947 | 0.68% |
| 3 | Trojan.Oficla.zip | 0.61% |
| 4 | Trojan.DownLoad3.28161 | 0.59% |
| 5 | Trojan.PWS.Panda.4795 | 0.55% |
| 6 | Tool.MailPassView.225 | 0.52% |
| 7 | Trojan.DownLoader9.19850 | 0.52% |
| 8 | Trojan.PWS.Panda.2401 | 0.52% |
| 9 | Exploit.Rtf.35 | 0.50% |
| 10 | Trojan.PWS.Panda.6222 | 0.39% |
| 11 | Trojan.DownLoader9.19834 | 0.37% |
| 12 | Trojan.PWS.Panda.655 | 0.37% |
| 13 | Trojan.PWS.Panda.547 | 0.36% |
| 14 | Trojan.Fraudster.778 | 0.36% |
| 15 | Trojan.PWS.Panda.5676 | 0.36% |
| 16 | BackDoor.Comet.884 | 0.32% |
| 17 | Exploit.Rtf.38 | 0.32% |
| 18 | BackDoor.Andromeda.267 | 0.32% |
| 19 | Trojan.Inject1.37106 | 0.29% |
| 20 | Trojan.Inject1.37071 | 0.28% |
Malicious files detected on user computers in February
| 01.02.2014 00:00 - 28.02.2014 17:00 | ||
| 1 | Trojan.InstallMonster.51 | 0.59% |
| 2 | Trojan.Packed.24524 | 0.56% |
| 3 | Trojan.LoadMoney.15 | 0.54% |
| 4 | Trojan.Fraudster.524 | 0.47% |
| 5 | Trojan.Hosts.28188 | 0.42% |
| 6 | Trojan.LoadMoney.1 | 0.39% |
| 7 | Trojan.InstallMonster.47 | 0.34% |
| 8 | JS.Redirector.209 | 0.33% |
| 9 | BackDoor.IRC.NgrBot.42 | 0.32% |
| 10 | Trojan.StartPage.59964 | 0.29% |
| 11 | Trojan.Packed.24814 | 0.28% |
| 12 | BackDoor.PHP.Shell.6 | 0.28% |
| 13 | Win32.HLLW.Shadow | 0.26% |
| 14 | Trojan.MulDrop4.25343 | 0.21% |
| 15 | Trojan.Triosir.1 | 0.20% |
| 16 | Win32.HLLW.Autoruner.59834 | 0.20% |
| 17 | Trojan.Fraudster.502 | 0.19% |
| 18 | Trojan.Spambot.11176 | 0.18% |
| 19 | Win32.HLLW.Shadow.based | 0.17% |
| 20 | Trojan.LoadMoney.227 | 0.17% |
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live