New Trojan compromises blog sites in Russia and other countries
Real-time threat news | Hot news | All the news | Virus alerts
August 6, 2013
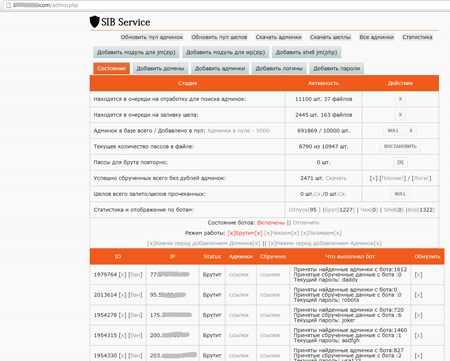
Once on an infected computer, Trojan.WPCracker.1 copies itself to one of the system folders and modifies the registry branch which is responsible for launching applications automatically at system startup. Then the Trojan connects to a remote server controlled by criminals.
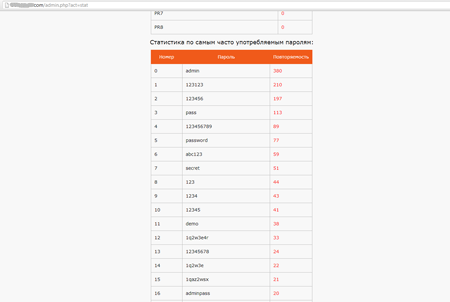
Attackers send a list of blogs and sites administered with popular CMSs, including Wordpress and Joomla, to the Trojan and then the Trojan starts cracking their access passwords. If successful, the Trojan sends the acquired information to the server.
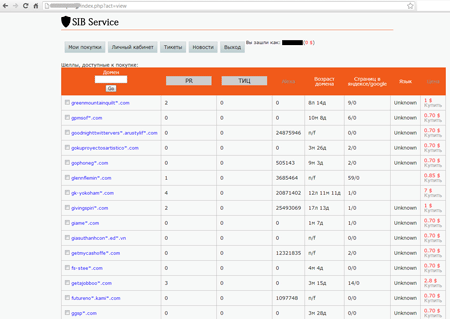
After that, the authors of Trojan.WPCracker.1 sell the access data to a third party (usually, to other criminals).
What is the danger of Trojan.WPCracker.1? Criminals can use it to change the content of the compromised blog or embed malicious code into the site, to infect the systems of visitors. This Trojan may be behind the increase in brute-force attacks on websites—a phenomenon registered by many security experts.
The signature of the threat has been added to the Dr.Web virus database, so it does not pose a serious danger to systems protected by Dr.Web software.