Doctor Web: June virus activity review
Virus reviews | Hot news | All the news | Virus alerts
July 2, 2013
Viruses
According to statistics collected by Dr.Web CureIt!, Trojan.Mods.2 was one of the most common threats in June 2013. It accounted for 3.97% of the infection incidents in the past month. This malware redirects users to criminal-owned web pages on which visitors are prompted to enter their phone number and a verification code into the appropriate boxes. By doing so, the victim is subscribed to a certain "information service" for which a regular payment is debited from their account.
The previous modification in the family, namely Trojan.Mods.1, is not far behind. It occupies fourth place at 1.45%, while Trojan.Hosts.6815 (2,94%) and Trojan.DownLoader9.19157 (1,92%) close out the top three. The ten most common threats detected by the curing utility Dr.Web CureIt! on users' computers in June 2013 are listed in the table below:
| Name | % |
| Trojan.Mods.2 | 3.97 |
| Trojan.Hosts.6815 | 2.94 |
| Trojan.DownLoader9.19157 | 1.92 |
| Trojan.Mods.1 | 1.45 |
| Trojan.Hosts.6838 | 1.44 |
| Trojan.Zekos | 1.22 |
| BackDoor.IRC.NgrBot.42 | 1.18 |
| Trojan.MulDrop4.25343 | 0.80 |
| Trojan.MayachokMEM.7 | 0.76 |
| Trojan.Packed.24079 | 0.75 |
Botnets
A new version of the bot Linux.Sshdkit, on which Doctor Web first reported in February 2013, was discovered in June 2013. As of June 27, the botnet created using a previously known version of the Trojan included as few as 42 active bots, with only eight infection incidents involving Linux servers during the last month.
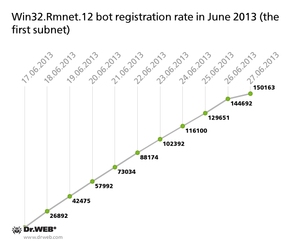
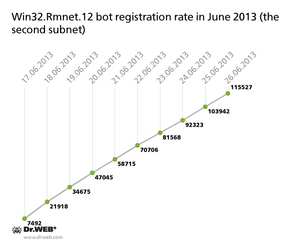
At the same time, infections with the file infector Win32.Rmnet.12 are growing in number. The first viral sub-net, whose command and control server is monitored by Doctor Web's analysts, currently comprises 459,192 bots, while the second includes 613,135 nodes. A graph indicating how newly infected hosts connected to the network in June 2013 is displayed below:
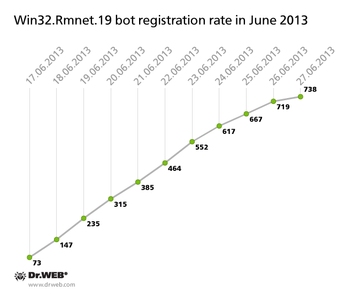
The botnet Win32.Rmnet.16 currently has 4,674 active bots (last month it had 5,220), while only 239 infected computers joined the zombie network in June. The number of desktops, on which malicious modules of Trojan.Rmnet.19 (as dubbed by Dr.Web) were discovered, decreased slightly too. In May the botnet included 20,235 infected PCs, but as of June 27 the number dropped to 15,611. The botnet's growth slowed as well, and can be traced in the diagram below. While 8,447 new joiners registered on the C&C server in May, only 738 infection incidents occurred from June 17-27.
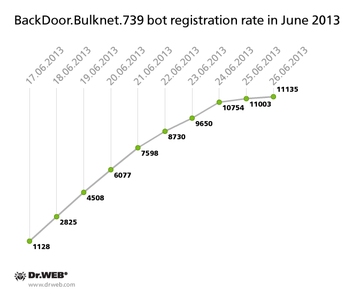
The botnet created with BackDoor.Bulknet.739 grew smaller, too. The hijacking of its C&C server was reported by Doctor Web earlier. If, in May, the network consisted of 17,242 infected computers, in late June, the number of active bots decreased to 16,024. Use the graph below to trace how newcomers registered on the C&C server through June:
The school of Macs infected with a Trojan for Mac OS X BackDoor.Flashback.39 also shrank insignificantly, but this process is not moving as fast as we would like. On June 27 the botnet BackDoor.Flashback.39 had 62,069 infected Macs —3,918 fewer nodes than in May.
The threat of the month
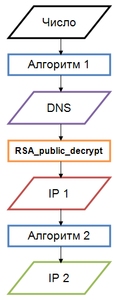
In June, a new Linux.Sshdkit modification joined the family of malicious programs for Linux. Like its predecessor, the updated version is also designed to steal login and passwords from Linux servers. It has been named Linux.Sshdkit.6. In this version of Linux.Sshdkit, attackers made a number of changes in order to make it difficult for virus analysts to intercept stolen passwords. In particular, they changed the routines used by the malware to determine the addresses of the servers to which the malware is to transmit stolen information. Now to calculate the target address, the Trojan uses a text string encrypted with a 128-bit RSA encryption key. The flowchart below illustrates how a C&C server address is generated.
Also changed was the command receipt routine: a special string for which a checksum is verified precedes any command. A more detailed description of this threat can be found in a corresponding review published by Doctor Web.
Another upsurge of encoders
Trojan coders become a scourge for personal computers: Doctor Web's anti-virus laboratory received about 2,800 complaints in connection with these malicious programs over the last three months, and in June the total number of requests exceeded 700. Trojan.Encoder.94 and Trojan.Encoder.225 became the most common encoder versions in the first summer month of 2013. They are distributed primarily by email, so Trojan.Encoder.225 can get into the operating system with a message that has an RTF document attached to it (with the extension .doc); this document exploits a Microsoft Office vulnerability. And, Trojan.Encoder.94 is often downloaded on computers by the malware BackDoor.Poison, which, in turn, is massively distributed in emails with attached files.
Because the workload of Doctor Web's virus laboratory has increased significantly of late, effective June 19, 2013, Doctor Web is helping only registered users of its products to decrypt files compromised by the malware.
Mobile threats
The first summer month showed that the theft of personal information, such as logins and passwords, short messages and call history, remains one of the most severe threats to owners of mobile devices. To accomplish these thefts, criminals employ Trojans as well as commercial spyware.
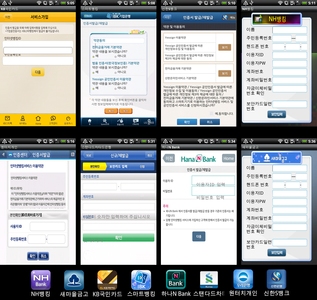
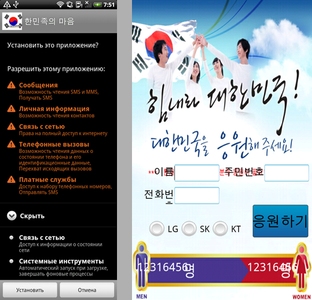
In early summer, the Trojan Android.Tempur.1.origin, designed to steal confidential information from South Korean Android users, was the most prominent mobile threat of this kind. Stolen data includes bank account details, and information about incoming SMS messages and outbound phone calls. The malware was distributed by cybercriminals as part of another program detected by Dr.Web as Android.MulDrop.8.origin, and as a separate apk package. The Trojan Android.Tempur.1.origin is a rather unusual malicious species because, when installed on a mobile device, it imitates the operation of legitimate banking applications and prompts the user to enter their personal information, which is then forwarded to a remote server along with intercepted text messages and information about phone calls.
More information about this threat can be found in a relevant publication on Doctor Web's site.
As for commercial spyware applications, noteworthy species among such programs detected in June include modifications of known Android spyware such as Android.MobileSpy and Android.SpyBubble, a new family Program.Highster, as well as the applications Program.Stealthgenie and Program.Ownspy, which are designed for BlackBerry and iOS, respectively. It is worth noting that Program.Ownspy and similar applications only run on devices where the operation ‘jailbreak’ has been performed (i.e., on devices that can access the file system), so the bulk of mobile Apple product owners are in no danger. Yet the number of people who are using hacked iOS devices is significant, so the spyware can represent a severe threat.
Android.SmsSend programs, which send short messages to premium numbers and sign up subscribers to various chargeable services, are still causing a headache to many Android device users. Signatures for several new modifications of these malicious programs were added to the Dr.Web virus database during the month, and in the second half of June, the company's analysts discovered that the malware Android.SmsSend.465.origin was being distributed by means of advertising messages displayed on a popular news portal.
When users load the site's page on an Android device, they are shown a special banner that prompts them to install a popular game, which is actually a malicious program in disguise. You can read more about this incident in news material published on Doctor Web's site.
Malicious files detected in mail traffic in June
| 01.06.2013 00:00 - 28.06.2013 11:00 | ||
| 1 | Trojan.Packed.196 | 0.77% |
| 2 | Win32.HLLM.MyDoom.54464 | 0.70% |
| 3 | Win32.HLLM.MyDoom.33808 | 0.62% |
| 4 | Trojan.PWS.Panda.655 | 0.57% |
| 5 | Exploit.CVE2012-0158.27 | 0.55% |
| 6 | Trojan.Siggen5.30475 | 0.55% |
| 7 | Trojan.PWS.Stealer.3128 | 0.46% |
| 8 | SCRIPT.Virus | 0.40% |
| 9 | VBS.Rmnet.2 | 0.40% |
| 10 | Win32.HLLM.Beagle | 0.40% |
| 11 | Trojan.PWS.Stealer.2877 | 0.40% |
| 12 | Trojan.MulDrop4.35808 | 0.35% |
| 13 | Trojan.Siggen5.24066 | 0.33% |
| 14 | Trojan.PWS.Multi.911 | 0.33% |
| 15 | Trojan.PWS.Panda.547 | 0.33% |
| 16 | Trojan.Inor | 0.31% |
| 17 | BackDoor.Comet.152 | 0.31% |
| 18 | BackDoor.Tishop.25 | 0.29% |
| 19 | Win32.HLLM.Graz | 0.29% |
| 20 | Trojan.PWS.Stealer.2832 | 0.26% |
Malicious files detected on user computers in June
| 01.06.2013 00:00 - 28.06.2013 11:00 | ||
| 1 | SCRIPT.Virus | 0.97% |
| 2 | Adware.Downware.915 | 0.75% |
| 3 | Tool.Unwanted.JS.SMSFraud.26 | 0.65% |
| 4 | JS.Packed.5 | 0.60% |
| 5 | Adware.InstallCore.114 | 0.52% |
| 6 | Adware.InstallCore.115 | 0.45% |
| 7 | Adware.InstallCore.101 | 0.44% |
| 8 | Adware.Downware.179 | 0.43% |
| 9 | Adware.Downware.1132 | 0.41% |
| 10 | Adware.Toolbar.202 | 0.39% |
| 11 | Tool.Unwanted.JS.SMSFraud.10 | 0.34% |
| 12 | Tool.Unwanted.JS.SMSFraud.29 | 0.33% |
| 13 | Trojan.Hosts.6838 | 0.33% |
| 14 | Adware.Downware.1157 | 0.33% |
| 15 | JS.IFrame.432 | 0.32% |
| 16 | Tool.Skymonk.11 | 0.32% |
| 17 | Win32.HLLW.Autoruner.59834 | 0.32% |
| 18 | Win32.HLLW.Shadow | 0.31% |
| 19 | Adware.Webalta.11 | 0.31% |
| 20 | Tool.Skymonk.13 | 0.30% |