New Trojan modification targets Linux servers
Real-time threat news | Hot news | All the news | Virus alerts
June 10, 2013
Doctor Web reported on initial versions of Linux.Sshdkit in February 2012. The Trojan is a library file available for 32- and 64-bit versions of Linux distributions. After its successful installation, the Trojan injects its code into the sshd process and uses this process’s authorization routines. Once a session is started and a user enters their login and password, the Trojan directs them to a remote server.
Doctor Web's analysts hijacked several Linux.Sshdkit command and control (C&C) servers to which earlier versions of the Trojan had connected. In addition, they not only managed to collect statistics regarding the number of infected machines but also determined their IP addresses. In May 2013, the Trojan sent access data for 562 infected Linux servers to the C&C server controlled by Doctor Web. Some of these servers belong to major hosting providers.
The new Trojan version, discovered by Doctor Web, has been dubbed Linux.Sshdkit.6. It is also a dynamic library designed for 64-bit versions of Linux. In this implementation of Linux.Sshdkit, attackers made a number of changes in order to make it difficult for virus analysts to intercept stolen passwords. In particular, they changed the routines used by malware to determine addresses of servers to which the malware has to transmit stolen information. Now to calculate the target address, the Trojan uses a text string encrypted with a 128-bit RSA encryption key. The flowchart below illustrates how a C&C server address is generated.
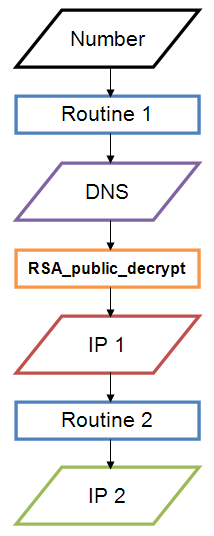
Also changed was the command receipt routine: a special string for which a checksum is verified precedes any command.
Since Linux.Sshdkit Trojans allow criminals to acquire information to gain unauthorised server access, they pose a severe threat to severs running under Linux. Doctor Web recommends that all administrators of Linux servers perform a system check for this threat.