April 2013 virus activity review from Doctor Web
Virus reviews | Hot news | All the news | Virus alerts
May 13, 2013
Viruses
According to statistics collected by Dr.Web CureIt!, the number of machines infected with Trojan.Hosts malware declined in the past month. The programs in question modify the hosts file which contains DNS server addresses. However, infections with Trojan.Hosts constituted more than 4.78% of the total infections which amounts to 40,000 detected malicious samples. The most common Trojan.Hosts modifications are listed in the table below.
| Trojan.Hosts modifications | % |
|---|---|
| Trojan.Hosts.6815 | 1,84 |
| Trojan.Hosts.6838 | 0,99 |
| Trojan.Hosts.6708 | 0,42 |
| Trojan.Hosts.6814 | 0,19 |
| Trojan.Hosts.6897 | 0,18 |
| Trojan.Hosts.6613 | 0,16 |
| Trojan.Hosts.6809 | 0,15 |
| Trojan.Hosts.5587 | 0,14 |
| Trojan.Hosts.5268 | 0,14 |
| Trojan.Hosts.6722 | 0,14 |
| Trojan.Hosts.7154 | 0,13 |
| Trojan.Hosts.6466 | 0,11 |
| Trojan.Hosts.6294 | 0.10 |
| Trojan.Hosts.7703 | 0.09 |
Doctor Web attributes such a large number of infections to multiple incidents of websites being compromised—the company published a report on this in March.
According to data gathered by Dr.Web CureIt!, Trojan.Mods.1 (earlier known as Trojan.Redirect.140), became one of the most common Trojans in April 2013. This program redirects browsers to bogus web pages. BackDoor.IRC.NgrBot.42 and Trojan.Zekos were also found in large numbers. Available for 32- and 64-bit versions of Windows, the latter can intercept DNS queries of Internet Explorer, Mozilla Firefox, Google Chrome, Opera and Safari. Consequently, when attempting to go to an address, the user ends up on a web page crafted by criminals; meanwhile, the correct URL will be displayed in the address bar. Virus writers use this method to prompt the user, their potential victim, to submit a phone number into a field and reply to a short message; doing so signs the user up to a chargeable service.
The table below lists the most common threats detected with Dr.Web CureIt! on home computers in April 2013.
| 1 | Trojan.Mods.1 | 3.07 |
| 2 | Trojan.Hosts.6815 | 1.84 |
| 3 | BackDoor.IRC.NgrBot.42 | 1.28 |
| 4 | Trojan.Hosts.6838 | 0.99 |
| 5 | Trojan.Zekos&lng=en">Trojan.Zekos | 0.87 |
| 6 | Win32.HLLW.Phorpiex.54 | 0.76 |
| 7 | Trojan.SMSSend.2363 | 0.73 |
| 8 | Win32.HLLP.Neshta | 0.72 |
| 9 | Trojan.Packed.23938 | 0.58 |
| 10 | Trojan.Packed.142 | 0.56 |
| 11 | BackDoor.Andromeda.22 | 0.56 |
| 12 | Trojan.StartPage.48148 | 0.56 |
| 13 | Trojan.Packed.23971 | 0.55 |
| 14 | Trojan.MulDrop4.25343 | 0.54 |
| 15 | BackDoor.Gurl.2 | 0.52 |
| 16 | Win32.Sector.22 | 0.47 |
| 17 | Trojan.Hosts.6708 | 0.42 |
| 18 | Trojan.PWS.Panda.2401 | 0.37 |
| 19 | Trojan.PWS.Stealer.1932 | 0.35 |
| 20 | Exploit.CVE2012-1723.13 | 0.33 |
Botnets
In early April, Doctor Web's analysts managed to gain control over a control server of a botnet comprised of computers infected with BackDoor.Bulknet.739 This malware sends massive volumes of spam and can execute criminal commands including commands to perform updates, download new message templates or spam mailing lists, or stop sending spam. If the program terminates abnormally, it can notify the intruders.
This malware sends massive volumes of spam and can execute criminal commands including commands to perform updates, download new message templates or spam mailing lists, or stop sending spam. If the program terminates abnormally, it can notify the intruders BackDoor.Bulknet.739. contacted the server controlled by Doctor Web's analysts. Statistics collected by the virus analysts helped greatly to analyse this malware, the details of which can be found in one of our previously published reviews.
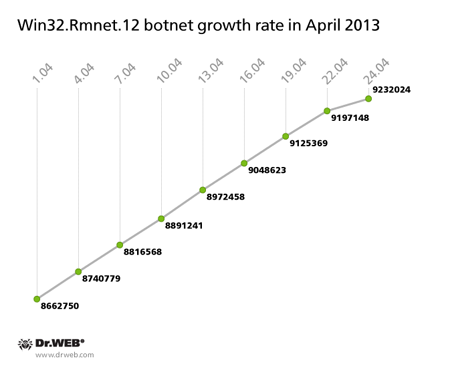
The growth rate of the botnet created with the file infector Win32.Rmnet.12 remained unchanged: 569,274 infected computers joined the network in April, and the total number of infected machines has reached 9,232,024. The diagram below illustrates how the network expanded:
Another botnet, formed by a related file infector Win32.Rmnet.16, showed a significant drop in its growth rate compared with previous months with around 500 hundred new joiners in April and reached a total of 262,604 infected hosts (against 262,083 hosts at the end of March). It should be noted that this is the lowest rate of growth demonstrated by the Win32.Rmnet.16 botnet over the last year. A similar tendency persists with regard to the BackDoor.Finder botnet which grew by only 114 nodes in April, and the daily number of corresponding infections ranged between 1 and 3. If this trend continues, it will be possible to speak about a decline in the spread of these malicious programs and state that the aforementioned botnets have almost stopped growing.
The threat of the month
A new representative of the well-known malicious family Trojan.Mayachok was one of the most peculiar threats analysed by Doctor Web in April. Despite the fact that analysts currently know about 1,500 species of the family, Trojan.Mayachok.18607 is quite different from the rest: apparently, its developers decided to completely rewrite the program, after keeping some of their basic features.
Trojan.Mayachok.18607 can infect both 32- and 64-bit versions of Windows. Trojan.Mayachok.18607’s main function is to implement web injects: as users load various web pages, the malware embeds third-party content into them. Google Chrome, Mozilla Firefox, Opera and several versions of Microsoft Internet Explorer, including the latest one, are at risk. When the user of an infected machine visits some popular sites, genuine web pages are displayed in the browser window; these pages contain content injected by the Trojan.
The attackers’ main objective is to force the user to enter their mobile phone number into a specific field. After that they are subscribed to services promoted by http://vkmediaget.com for a fee of 0.60 USD per 24 hours.
Encoders on the offensive
Encoder Trojans are among the most dangerous threats in the modern IT world. Two such programs— Trojan.Encoder.205 and Trojan.Encoder.215—were spread on a large scale in April. Trojan.Encoder programs seek out music, Microsoft Office, image and archive files on the hard drives of infected computers and then encrypt them. After that they display a demand requiring that the user pay as much as several thousand dollars to decrypt the data.
Spread with spam, these Trojans can do a lot of damage— several hundred systems have already been compromised by the encoders. More information on how to neutralize such threats can be found in news material published by Doctor Web.
Threats to Android
The second month of spring 2013 once again confirmed that Android is the main target for cybercriminals interested in mobile platforms. Throughout April, Doctor Web's analysts discovered new malicious Android applications whose definitions were promptly added to the Dr.Web virus databases.
The discovery on Google Play of programs containing the malicious adware module Android.Androways.1.origin became one of the most significant events related to Android security. Criminals distributed the module as part of their seemingly harmless ad network which enables developers to integrate the module into their software so that it generates revenue. Similarly to legal ad network modules, Android.Androways.1.origin can display push notifications in the status bar, however, these messages can be used to show fake prompts to update various programs. If the user agrees to an update, they risk downloading an Android.SmsSend program to their device.
In addition, Android.Androways.1.origin can execute a number of commands from a remote server and upload such information as the device's phone number and IMEI, and the operator code to the server. More detailed information about this threat can be found in our news material.
Trojan horses primarily targeting devices used in China stand out from the multitude of malware designed to attack Android. Criminals usually embed them into legitimate applications. Various software catalogues and forums remain the most popular ways to distribute them. In April, Doctor Web's analysts discovered several such malicious programs. These include Android.Uapush.2.origin, Android.MMarketPay.3.origin, Android.DownLoader.17.origin, and several versions of Android.Infostealer spy programs and a number of SMS Trojans.
Android.Uapush.2.origin is a Trojan horse whose main purpose is to display advertising messages in the notification bar. However, it also has other functions. In particular, Android.Uapush.2.origin collects information about browser bookmarks, outbound calls, address book contact details and personal information stored by the IM client QQ. The Trojan uploads stolen information to a remote server.
Android.MMarketPay.3.origin is a malicious program discovered in early April. This Trojan is a modification of malware that Doctor Web reported on last year. Similarly to its predecessor, Android.MMarketPay.3.origin is designed to automatically buy applications on the Mobile Market portal maintained by the carrier China Mobile. This program can bypass the online store’s security restrictions and cause significant damage to Chinese users' finances by covertly purchasing applications.
As for Android.DownLoader.17.origin, it is a Trojan downloader that can download other applications from the Internet. Once the apk-package is downloaded, Android.DownLoader.17.origin attempts to install it. This Trojan was found in a large number of games and other applications available for downloading from several Chinese sites, so it can be assumed that the criminals who made it have ambitious plans with regard to the program. In particular, they can use it to increase the rating of applications or adjust the installations counter for programs distributed from partner sites. The illustration below provides information about some of the compromised applications that contain Android.DownLoader.17.origin.
Discovered in April, Android.Infostealer.4.origin, Android.Infostealer.5.origin and Android.Infostealer.6.origin are Trojans that steal such sensitive information as a device's IMEI, phone number and list of installed applications and sends this data to a remote, criminal-controlled server.
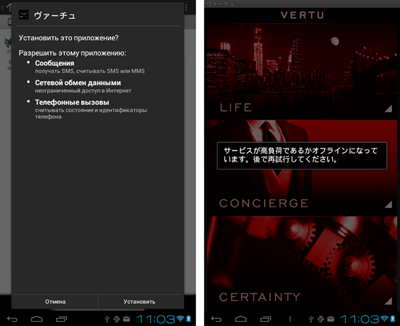
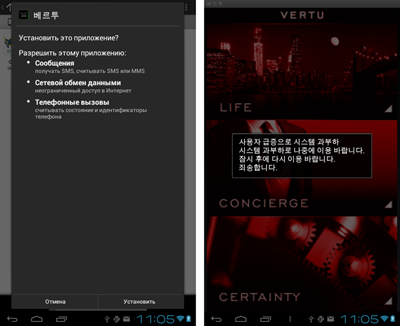
In the past month, cybercriminals didn't spare other East Asian countries, namely South Korea and Japan. An entry concerning the program Android.SmsSpy.27.origin, which also steals information, was added to the Dr.Web virus database at the end of the past month. This malware, which steals incoming short messages and sends them to a remote server, is spread as a Japanese and Korean version of a UI theme for Vertu phones.
Malicious files detected in mail traffic in April
| 01.04.2013 00:00 - 30.04.2013 23:00 | ||
| 1 | Trojan.PWS.Panda.3734 | 1.30% |
| 2 | Trojan.Inject2.23 | 1.11% |
| 3 | JS.Redirector.155 | 0.95% |
| 4 | Trojan.Necurs.97 | 0.88% |
| 5 | Trojan.Packed.196 | 0.77% |
| 6 | Win32.HLLM.MyDoom.54464 | 0.72% |
| 7 | Trojan.PWS.Stealer.2877 | 0.65% |
| 8 | Win32.HLLM.MyDoom.33808 | 0.51% |
| 9 | Trojan.Packed | 0.51% |
| 10 | SCRIPT.Virus | 0.39% |
| 11 | Trojan.Oficla.zip | 0.37% |
| 12 | BackDoor.Comet.152 | 0.37% |
| 13 | Trojan.PWS.Stealer.2830 | 0.37% |
| 14 | Trojan.PWS.Panda.547 | 0.35% |
| 15 | Win32.HLLM.Beagle | 0.32% |
| 16 | Trojan.PWS.Panda.2401 | 0.30% |
| 17 | Trojan.MulDrop2.64582 | 0.26% |
| 18 | Trojan.PWS.Stealer.1932 | 0.25% |
| 19 | Trojan.PWS.Panda.655 | 0.25% |
| 20 | Trojan.Siggen5.13188 | 0.21% |
Malicious files detected on user computers in April
| 01.04.2013 00:00 - 30.04.2013 23:00 | ||
| 1 | SCRIPT.Virus | 0.68% |
| 2 | Adware.Downware.915 | 0.65% |
| 3 | Tool.Unwanted.JS.SMSFraud.26 | 0.55% |
| 4 | Adware.Downware.179 | 0.47% |
| 5 | Adware.InstallCore.99 | 0.39% |
| 6 | JS.Redirector.189 | 0.38% |
| 7 | JS.IFrame.387 | 0.37% |
| 8 | Trojan.Packed.24079 | 0.36% |
| 9 | Adware.InstallCore.101 | 0.36% |
| 10 | Trojan.Redirect.140 | 0.34% |
| 11 | Adware.Webalta.11 | 0.34% |
| 12 | Tool.Unwanted.JS.SMSFraud.10 | 0.33% |
| 13 | JS.Redirector.188 | 0.33% |
| 14 | JS.Redirector.175 | 0.31% |
| 15 | Trojan.Fraudster.394 | 0.31% |
| 16 | Win32.HLLW.Shadow | 0.30% |
| 17 | Win32.HLLW.Autoruner.59834 | 0.29% |
| 18 | Tool.Skymonk.11 | 0.29% |
| 19 | Adware.Downware.1109 | 0.28% |
| 20 | Trojan.Fraudster.407 | 0.27% |