Trojan.Rodricter spreads by exploiting critical Java vulnerability
Real-time threat news | All the news | Virus alerts
September 5, 2012
To spread malware, the attackers used compromised websites containing modified .htaccess files. A malicious script embedded in the page code caused a chain of redirects where the final address depended on the target computer's operating system. Windows users were redirected to a page that contained code involving various exploits. It is noteworthy that the server addresses, to which users were redirected, changed every hour.
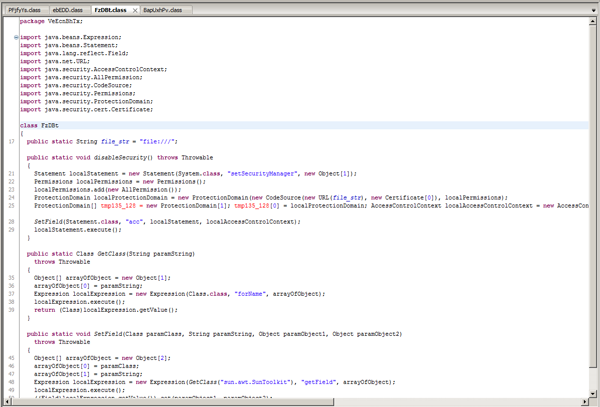
Web pages loaded in browsers featured code exploiting two vulnerabilities, namely, CVE-2012-1723 and CVE-2012-4681. The incorporated exploit depends on the version of Java Runtime: for versions 7.05 and 7.06, the vulnerability CVE-2012-4681 is used to bypass security mechanisms.
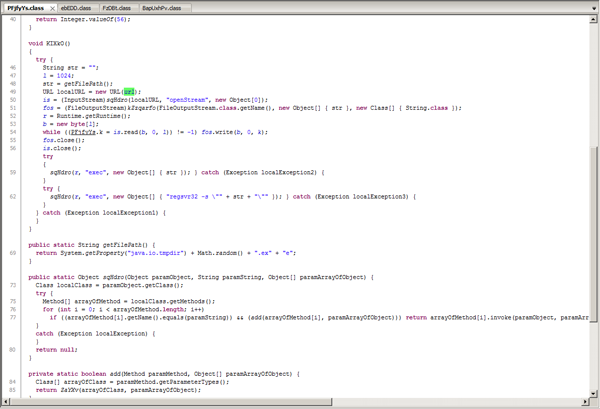
If the vulnerability was exploited successfully, a Java applet decrypts the file “class” whose main purpose is to download and run executable files. This approach was used to spread Trojan.Rodricter.21.
Trojan.Rodricter.21 features rootkit technologies and consists of several components. So, once launched on an infected computer, its dropper checks whether anti-virus software and debuggers are present in the system, and then tries to elevate its privileges. To accomplish this, the vulnerability of the OS, in particular, may be exploited. It also disables UAC if it is used in the system. Further steps depend on the permissions the Trojan horse has managed to acquire. The Trojan saves its main component to the disk and, if it has obtained sufficient privileges, infects one of the standard Windows drivers in order to hide its principal module in the compromised system. Thus, Trojan.Rodricter.21 can well be classified as a rootkit Trojan. Among other things, the malware is able to change Internet Explorer and Mozilla Firefox settings. For the latter, the Trojan installs an additional search engine plug-in in the \searchplugins\ folder, replaces User-Agent, and changes the default search engine. As a result, all search queries sent from the infected system look as follows: http://findgala.com/?&uid=%d&&q={search query}, where % d is the Trojan’s unique identifier. Trojan.Rodricter.21 also modifies the hosts file by adding to it the addresses of websites belonging to criminals.
The Trojan.Rodricter.21 main module is saved as an executable file in the temporary folder; it is intended to introduce arbitrary content into the user's traffic.
The signature of this threat has been added to the database of Dr.Web anti-virus software and Dr.Web CureIt! utility. Doctor Web strongly recommends that users install the latest security updates, first and foremost — updates for the Java Runtime Environment.