January 27, 2012
Otherwise Trojan.Winlock.5490, written in C, won't run in a system with a different default language. The Trojan horse incorporates anti-debugging features: when loaded, it checks if its process is launched in VirtualBox, QEmu or VMWare environment. If it is, the Trojan horse process is ended. A significant portion of Windows blockers work in the offline mode. They contain an unlock code in their own resources (plain text or encrypted ), or calculate it based on the number of parameters or do not have such a code at all. Trojan.Winlock.5490 belongs to the last group of extortion programs . It deletes itself automatically in a week after installation. However, after having blocked access to Windows it reports to a remote server and sends information about the infected machine, payment card numbers entered by the victim and receives "OK" as a response.
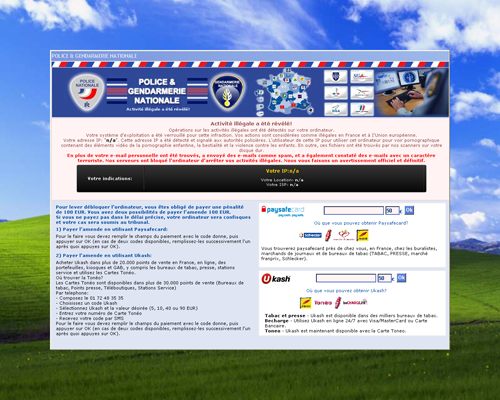
Once Trojan.Winlock.5490 is in the system, it starts an svchost.exe process with its injected code and orders Windows to hide the Task bar and stops all explorer.exe and taskmgr.exe process threads. Then the Trojan.horse adds its registry entry to be launched automatically and displays a window containing a demand to pay 100 euro with Paysafecard or Ukash card. The message language is French. The the card number entered by the victim is sent to the remote command server and the user is informed that the payment will be processed in 24 hours.
Because this Trojan horse does not use unlock codes, users are advised to scan their computers with Dr.Web LiveCD. You can also try to change the date in BIOS (set a date several months later than the current one) and scan hard drives with Dr.Web CureIt!. You may also delete the Trojan horse autorun entry from the Windows Registry found in Software\Microsoft\Windows\CurrentVersion\Run\.

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments