November 2011 virus activity review: virus makers and spammers forgot about the elections
Virus reviews | All the news | Virus alerts
December 2, 2011
Spam in November
The Russian State Duma elections on December 4, 2011, didn't attract the attention of spammers; despite expectations, the bulk of politics-related spam didn't increase compared with previous months. Strangely, in spam traffic scanned by Dr.Web software, the quantity of unsolicited messages concerning Ukrainian politics exceeded the quantity concerning Russian politics.
At the same time, a large-scale spam mailing was registered when the message subject concerned a salary increase for Russian military personnel. The e-mails contained an attachment featuring the threat Exploit.Rtf.based. The malicious code exploits a Microsoft Word vulnerability that enables intruders to execute arbitrary code upon opening an RTF file so a malicious application can acquire the user's privileges. Since the subject is a matter of great concern for a large number of servicemen, many of them may have fallen for the trick.
Threats to mobile devices
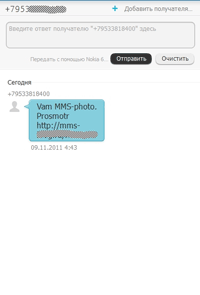
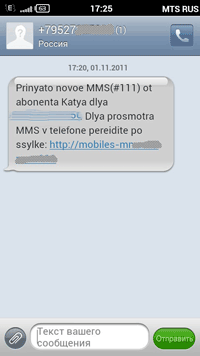
Many Russians owning mobile phones supporting Java fell victim to cyber fraud. The fraudulent scheme begins as follows. An unsuspecting victim receives a short message informing them that they have received an MMS. In order to view the message’s content, they have to follow a link. If they do, an image or a video clip, along with a Trojan horse, is downloaded onto their device. In many cases the Trojan was Java.SMSSend.251. However, such programs are often modified to complicate their detection. According to Doctor Web's virus analysts, on average a new modification appears once a fortnight.
 |
 |
When launched on a compromised mobile phone, this Trojan horse starts sending messages to a certain number and funds are withdrawn from the subscriber's account. Typically, criminals send such messages during weekends or in night hours to ensure that it takes as long as possible for the user and the carrier's support engineers to resolve the issue.
Trojan horse for pharmacists
In the first days of November, virus makers set loose a Trojan horse designed specifically to steal data from applications used by pharmaceutical companies. When launched in the infected system, BackDoor.Dande (written in C) checks whether its copy is already present in the system and determines the active user login and OS version. If the OS is Windows XP or Windows Server 2003, the backdoor connects to a remote controlling server and downloads an encrypted configuration file and Trojan.PWS.Dande code which is decrypted and saved in a directory on the disk. In addition, the backdoor can execute instructions received from a server such as to download, save and launch Trojan.PWS.Dande, delete the program, or write data into the configuration file.
It should be mentioned that the backdoor features a rather uncommon server search routine. If a known server becomes unavailable, the malware will use a server name-generating algorithm to find another one. In addition, the payload can only be used on a machine that has been infected by this malware. Since the Trojan horse infects the advapi32.dll file, which is loaded by all processes in the system, its code is easily injected into all of them.

Trojan.PWS.Dande steals information from client applications used to order pharmaceutical products. Collected information includes system information and account passwords. Probably, criminals are most interested in order quantities and prices. All the stolen information is encrypted and transmitted to a server controlled by criminals. To put it another way, this is a rare instance of a Trojan horse being designed to steal information related to a particular type of business.
Other threats in November
In November Doctor Web's analysts also discovered a new modification of a complex backdoor for Mac OS X that was dubbed BackDoorFlashback.8.
BackDoor.Flashback is a multi-component backdoor program for Mac OS X whose installer is disguised as an Adobe Flash Player installer. Mac OS X. users are offered the opportunity to download an archive containing the FlashPlayer-11-macos.pkg file (downloading wouldn't start for other operating systems). After launching, the installer tries to download the main Trojan horse module from a certain site. If the module can't be downloaded, the installer quits.
Unlike its predecessors, the new BackDoor.Flashback.8 can inject its code into processes by means of two routines employed separately depending on the presence of exported dyld module routines in the target process. If the routines are unavailable, the Trojan horse searches the memory for the procedures it needs.
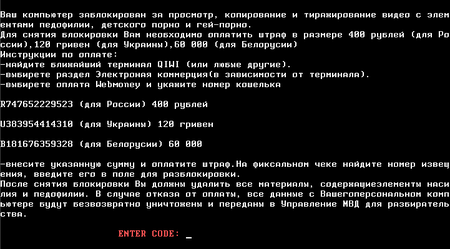
In addition, the second half of November was marked by the emergence of a new modification of Trojan.MBRLock ransomware.
When launched in a compromised system, Trojan.MBRlock.17 saves its file into a temporary directory with a random name, launches the calc.exe process (the standard Windows calculator) and injects its code into the process. After that the injected code creates a file in the %APPDATA%\Adobe\Update\ directory, launches explorer.exe and injects its code into this process too. In turn, explorer.exe infects MBR and attempts to shut down Windows. Interestingly, unlike its predecessors, Trojan.MBRlock.17 writes its components such as fonts, message text and the original MBR code into random disk sectors and can change its code constants that determine which sectors are to be selected for storing its data. An unlock key is generated according to certain parameters. The Trojan horse also backs up the first disk sector and deletes the partition table.
All in all, November 2011 demonstrated an average infection spread rate, with the number of incidents related to Trojan.Encoder and Trojan.FolderLock up compared with previous months. From the beginning of November onwards, Doctor Web received sixty-six support requests concerning the malicious activities of Trojan.FolderLock, and the last week of the month alone saw 63 requests connected with Trojan.Encoder.123. To avoid data losses, we recommend making timely backups of the data stored on your computer.