Phishers vs. customers of Russian hosting providers, new attacks on social networkers, and other virus events of October 2011
Virus reviews | All the news | Virus alerts
2 ноября 2011 года
VKontakte users under attack
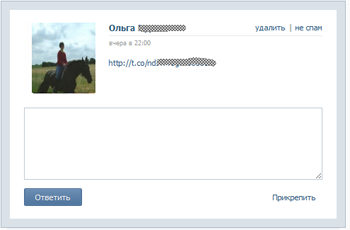
Fraudsters are adapting to the virtual social networking environment and are inventing new schemes to deceive careless users. In particular, one scheme involved sending a message to the victim supposedly from someone on their friend list.
Clicking on the link contained in such a message directed the user to a web page containing a video clip where they were prompted to enter their VKontakte access login and password. Account information submitted via this page ended up in the hands of criminals.
Hosting provider customers in danger
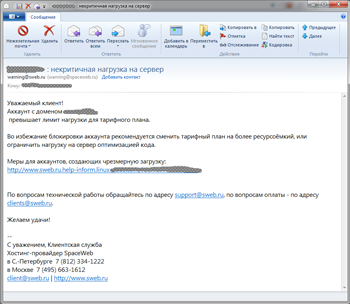
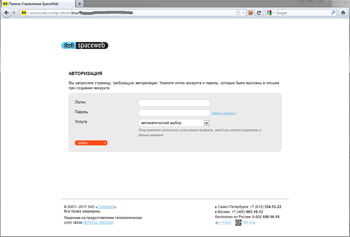
Customers of several Russian hosting providers also became targets of fraud. Phishers attacked Peterhost, SpaceWeb, FirstVDS, Timeweb, and Agava customers. In all of these fraud incidents, criminals used a similar scheme. With the WHOIS service, they compiled a list of sites hosted by the provider and determined the site owner’s e-mail address. The criminals then sent a message supposedly from the provider's headquarters to that address. The message notified the owner that their site consumed more resources than allowed by their current contract. To solve this problem, they suggested to the customer that they follow a link to a fake web page that looked exactly like the authentic site. The bogus page URL, though similar to the genuine provider site address, would have a different domain suffix. If the victim entered their account information into the form found on the bogus page, the data instantly fell into the criminals’ hands.
With this information at their disposal, intruders could covertly modify the contents of the hosted site, e.g., use it to spread malicious programs or publish illegal content.
Computers controlled remotely with BackDoor.Bitsex
This malicious program written in C is saved onto a disk as SetupEngine.dll. When launched, BackDoor.Bitsex puts Audiozombi.exe and SetupEngine.dll into a folder and starts the executable which loads the SetupEngine.dll. After that, the malicious program determines the name of its control server and connects to it. The Trojan horse also checks the active process list for running anti-viruses, sends a corresponding report to the remote server, and launches a keylogger in the compromised system.
BackDoor.Bitsex comes with a wide array of features that enable criminals to view information stored on disks that are accessible in the compromised system, take screenshots and photos by means of a web camera (if available), load web pages, download and launch programs, display custom messages on the screen in the infected system, and carry out DDoS attacks at various servers. There are almost a dozen known malicious features incorporated into BackDoor.Bitsex.
Other threats in October
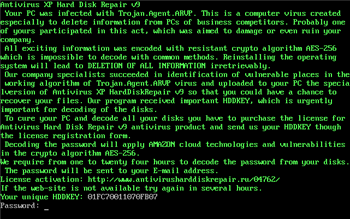
In October Doctor Web's virus analysts discovered a new extortionist program that blocks the Master Boot Record. The distinguishing feature of Trojan.MBRlock.16 is the absence of the system unlock code in the program's resources. The code is generated in the system using information about its hardware configuration.
When launched, Trojan.MBRlock.16 behaves like the utility Antivirus XP Hard Disk Repair and displays a message notifying the user that their system has been infected by Trojan.Agent.ARVP and that all of the information on their hard drives has been encrypted by malware (in reality, none of the files have been encrypted). To save the user data, criminals offer the victim the opportunity to buy a license by sending a generated key via a web form found on bogus sites and by transferring a payment. The unique key (HDDKEY) and the unlock password are generated by Trojan.MBRlock.16 using the system hardware information.
To help users who have fallen victim to the extortionist program, Doctor Web offers an unlock password generator that can be downloaded from ftp://ftp.drweb.com/pub/drweb/tools/mbrlock16keygen.exe. You can also use the unlock service. the unlock service.
Another Trojan horse discovered in October was dubbed Trojan.SkynetRef.1. This malicious program works as a local proxy-server which is used to load fake web pages in a browser. To set their brainchild loose, the criminals took time and effort to create several full-fledged websites such as fvsn.org, operadownload.info, downloadutorrent.info, downloadflashplayer.biz.
When users attempt to download a program from one of the sites, they are prompted to download and launch a special installer. It is always the same program, but its name may vary depending on which program the user chooses to download. The installer uses its own name to determine which application the user wants to download, and if the file name is changed (this often happens when it is checked by various automated services), the installer stops working. If the name is correct, it downloads and installs Trojan.SkynetRef.1 into the system along with the program selected by the user. The Trojan horse can replace pages loaded by a user with fake ones as defined in its configuration file.
Malicious files detected in mail traffic in October
| 01.10.2011 00:00 - 31.10.2011 23:00 | ||
| 1 | Trojan.Oficla.zip | 43106 (17.04%) |
| 2 | Trojan.DownLoader5.886 | 36915 (14.59%) |
| 3 | Win32.HLLM.MyDoom.33808 | 36678 (14.50%) |
| 4 | Trojan.PWS.Mailer.56 | 23177 (9.16%) |
| 5 | Win32.HLLM.MyDoom.54464 | 18309 (7.24%) |
| 6 | Trojan.MulDrop3.6042 | 12735 (5.03%) |
| 7 | Win32.HLLM.Netsky.18401 | 9577 (3.78%) |
| 8 | Win32.HLLM.MyDoom.based | 7015 (2.77%) |
| 9 | Win32.HLLM.Netsky.35328 | 6221 (2.46%) |
| 10 | Win32.HLLM.Netsky | 4288 (1.69%) |
| 11 | Win32.HLLM.Beagle | 4140 (1.64%) |
| 12 | Trojan.DownLoad2.22099 | 3508 (1.39%) |
| 13 | W97M.Spool | 2791 (1.10%) |
| 14 | JS.IFrame.151 | 2615 (1.03%) |
| 15 | BackDoor.IRC.Sdbot.4590 | 1854 (0.73%) |
| 16 | Exploit.IframeBO | 1815 (0.72%) |
| 17 | BackDoor.IRC.Bot.872 | 1470 (0.58%) |
| 18 | Win32.Sector.28480 | 1370 (0.54%) |
| 19 | Win32.HLLM.Netsky.based | 1343 (0.53%) |
| 20 | Win32.HLLM.Netsky.24064 | 1246 (0.49%) |
Total scanned: 118,243,404
Infected: 253,032 (0.21%)
Malicious files detected on user machines in October
| 01.10.2011 00:00 - 31.10.2011 23:00 | ||
| 1 | JS.Click.218 | 74679301 (42.06%) |
| 2 | Win32.Rmnet.12 | 33786253 (19.03%) |
| 3 | Trojan.IFrameClick.3 | 22083667 (12.44%) |
| 4 | Win32.HLLP.Neshta | 11033803 (6.21%) |
| 5 | JS.IFrame.112 | 6083679 (3.43%) |
| 6 | JS.IFrame.95 | 5325180 (3.00%) |
| 7 | Win32.HLLP.Sector.28332 | 4380023 (2.47%) |
| 8 | JS.IFrame.117 | 2747192 (1.55%) |
| 9 | Win32.HLLP.Whboy | 1776446 (1.00%) |
| 10 | Trojan.Fraudster.211 | 1725067 (0.97%) |
| 11 | Trojan.Mayachok.1 | 1681669 (0.95%) |
| 12 | Win32.HLLP.Whboy.45 | 1640615 (0.92%) |
| 13 | Win32.HLLP.Rox | 1106517 (0.62%) |
| 14 | Win32.Virut | 587649 (0.33%) |
| 15 | Trojan.MulDrop1.48542 | 531951 (0.30%) |
| 16 | Trojan.WMALoader | 511429 (0.29%) |
| 17 | Win32.Siggen.8 | 355786 (0.20%) |
| 18 | BackDoor.Ddoser.131 | 341686 (0.19%) |
| 19 | HTTP.Content.Malformed | 338613 (0.19%) |
| 20 | JS.Click.222 | 299005 (0.17%) |
Total scanned: 17,451,623,339,426,039
Infected: 177,541,621 (0.00%)