August virus review: Counter-Strike users under attack and Trojan.Mayachok proliferates
Virus reviews | Real-time threat news | All the news | Virus alerts
September 2, 2011
Android.SmsSend growth in August
The majority of malicious programs for Android covertly send short messages to paid service numbers from a compromised device or sign up the subscriber to premium services while withdrawing fees from the victim's account. Android.SmsSend horses do not destroy files or spy on the device's owner. They solicit inexperienced users to send paid short messages that let them (the users) install applications that can otherwise be obtained for free elsewhere.
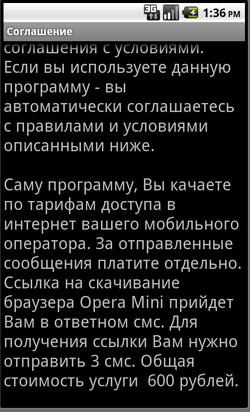
The makers of Trojan horses from the Android.SmsSendfamily, known since August 2010, use the same fraudulent scheme as the one adopted to distribute Trojan.SmsSend for desktops. A victim downloads an application from a web-site, e.g. the program is Opera Mini. During installation the user is prompted to send several short messages to continue the installation. A reply usually contains a link and a password that the victim needs to enter on a bogus web-site. After that, they are given an opportunity to download the full distribution of the software they need. The essence of this fraud is that the user can download the application free of charge from its developer's site rather than pay to criminals.
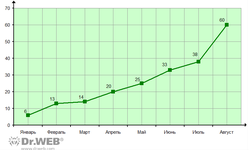
At the beginning of 2011, the Dr.Web virus databases listed a total of six variants of this Trojan horse, but now they number over 60. In other words, the number of Android.SmsSend has increased tenfold in seven months. The number of new modifications sent to Doctor Web's virus laboratory in August 2011 also rose dramatically— 22 previously unknown versions of the Trojan horse have been found since the beginning of August as opposed to the usual average of five to seven per month. Thus, we can talk about a 36% rise in the number of Android.SmsSend versions in August 2011.
Obviously, such a sharp increase is due to the cost-effectiveness of this fraud scheme which includes the production and distribution of these Trojan horses and the easy profits obtained by deceiving careless users whose mobile devices have been infected. It is likely that this trend will persist. The graph below shows how the number of detections of new Android.SmsSend versions grew throughout the year.
Users of mobile devices running Android are recommended to search the web for information about the programs they want to install and to never send messages to pay for applications known to be available free of charge. Additionally, download applications only from trusted resources such as the official Android Market to make sure no malware gets onto your device.
Counter-Strike players under attack
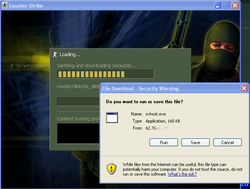
In August 2011 Doctor Web's virus analysts discovered a threat to game fans. A post about another threat appeared on Doctor Web's forum on August 5: While attempting to connect to a certain Counter-Strike 1.6 server, a user’s computer started downloading svhost.exe and bot2.exe files and also the admin.cmd file (distributed as Counter-Strike.cmd at the beginning of 2011). It should be noted that such behaviour is not typical of the Counter-Strike client.
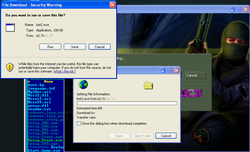
An examination by Doctor Web's virus analysts revealed the following scheme A group of attackers set up a Counter-Strike game server that distributed the Trojan horse Win32.HLLW.HLProxy. (Some time ago, this Trojan horse was spread among Counter-Strike fans as a "useful" application, so many people downloaded and installed it on their PCs of their own free will). The Trojan horse distribution mechanism was rather peculiar. When a user connected to the game server, the player was displayed a special MOTD welcome screen, which could feature server advertising or any set of rules defined by its administrators. The window's contents were an HTML file. The MOTD file created by criminals contained an IFRAME to redirect the client to a server controlled by the intruders. From this server the admin.cmd file containing the Trojan horse Win32.HLLW.HLProxy was downloaded and launched on the victim's computer.
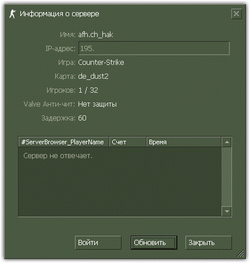
The main purpose of the Trojan horse was to launch on a player's computer a proxy server that emulated several Counter-Strike game servers on the same machine and transmitted corresponding information to servers belonging to VALVE When accessing a game server emulated by the Trojan horse, the client software was redirected to the attackers’ real game server from which the player received the Trojan horse Win32.HLLW.HLProxy. So the number of infected machines increased exponentially. The screenshot below illustrates the Trojan horse’s activity; several game servers with one IP address are supposedly running on an infected machine.
In addition, the Trojan horse can carry out DDoS attacks on gaming servers and servers belonging to VALVE, so many of them could be unavailable at different times. We can assume that one of the criminals' goals was to collect money from game server owners for bringing in new players as well as to carry out DDoS attacks on "unwanted" game servers. Doctor Web recommends that Counter-Strike fans be vigilant: do not agree with browser prompts to download and install executable files on your computer As of August 29, 2011, this malicious software was still being distributed from certain game servers.
Win32.Induc.2 infects Delphi IDE
Discovered in August, the new Trojan horse Win32.Induc.2 compromises the Delphi IDE, so that afterwards all the programs compiled in the environment contain malicious code. The main difference between Win32.Induc.2 and Win32.Induc lies in the malicious payload of the latter, while the former can only replicate itself.
The Trojan horse adds its shortcut under the name APMV in the Windows autorun directory and supplies it with a random icon. When launched upon a subsequent start of the operating system, Win32.Induc.2 searches for the Delphi IDE installation directory, copies itself into the defines.inc file, and modifies the sysinit.pas file so that launching an infected program saves the Trojan horse into the ~.exe and launches it. Then Win32.Induc.2 recompiles the sysinit module and restores the original content of the Source directory to hide its presence in the system. The Trojan horse places the compiled dcu file into the /lib directory to infect all the programs created by the user thereafter.
As mentioned above, this Trojan horse modification comes with a payload that is implemented in a very peculiar way. The malicious file contains several URLs pointing to user avatars on several forums. The avatars incorporate an encrypted string containing another URL used by the Trojan horse to download an encrypted exe-file from a remote host. Thus, Win32.Induc.2 can download and run executable files that could harm the operating system.
Darkness botnets attack LineAge2 servers
BackDoor.DarkNess is not just a backdoor allowing anyone to create a bot network and carry out a DDoS attack on the chosen target. It is a versatile tool for various tasks. For example, BackDoor.DarkNess.25 can steal user data from such popular programs as Total Commander (the FTP connection settings), FlashFXP, FileZilla, WS_FTP, QIP, CuteFTP, and The Bat!, but the main purpose of the backdoor is to carry out DDoS attacks on command from a remote server. BackDoor.DarkNess is written in Delphi; the administrative part is implemented in PHP. This is what the bootnet administrative center page looks like:
Over the past four months, Doctor Web's virus analysts discovered 49 botnets created using BackDoor.DarkNess. About ten of them are still operational, and Doctor Web continues to monitor their activity closely. During this period bots received 363 unique commands, most of which initiated DDoS attacks. The most popular targets of such attacks are numerous LineAge-2 online servers: LA2 game servers were attacked in 13.5% of all cases (71 unique attacks). Other sites that came under attack were devoted to the following topics (in descending order of popularity): escort agencies, malware and information security forums, online shops selling fake watches of the world's leading brands, media, hosting providers, pizza delivery, and finally, Forex exchange. The most popular targets for hacker attacks include the following servers:
- f**kav.ru (35 unique attacks, 6,6%)
- tempelgirls.ch (31 unique attacks, 5,8%)
- katera.ru (26 unique attacks, 4,9%)
- flyspb.ru (16 unique attacks 3%)
- realescort.eu (15 unique attacks, 2,8%)
- superbeach.ru (12 unique attacks, 2,2%)
- auction.de (8 unique attacks, 1,5%)
- all-lineage2.ru (7 unique attacks, 1,3%)
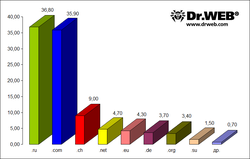
If the attacked site had database access scripts (e. g., a forum), these scripts were also utilized for a DDoS attack in 14.5% of the cases. The distribution of the attacked servers among domains (by percentage) is illustrated by the chart below:
The chart shows that the greatest number of servers that came under attack belonged to the ru and com domains (36.8% and 35.9% respectively), the ch domain occupies the third position and is followed by .net (4.7%), .eu (4.3%), .de (3,7%), .org (3,4%) and .su (1,5%). The share of attacks on sites in other domains was less than one percent.
We can assume that due to the wide availability of this backdoor, the number of botnets and their activity is unlikely to diminish in the near future. Despite the fact that BackDoor.DarkNess has been known about for a long time, it still enjoys certain popularity: Doctor Web's virus laboratory gets 30 new samples per month of this backdoor, an average of one sample per day. We also expect new versions of BackDoor.DarkNesswith additional payload besides the basic DDoS-bot function.
Trojan.Mayachok.1 and Mayachok.2 — the season hits
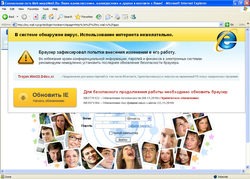
The beginning of August was marked by a rapid growth in the number of Trojan.Mayachok.1 infections. Many users suddenly found themselves unable to surf the web, and instead of seeing the sites they requested, they saw a message stating that the channel in their area was overloaded so access to certain sites was restricted until more bandwidth was available. Furthermore, it offered users the option to use the back-up channel To confirm their intentions and their urgent need to switch to a backup channel, they had to reply to an incoming short message. If a user did submit their phone number through the web form and replied to the message, a certain amount of money was withdrawn from their mobile account. Were fixed the cases of blocking Internet access with the substitution of site “Rostelekom”; however, to this the appetites of criminals were not limited: here is the incomplete list of the Internet- resources, whose pages can substitute this Trojan: youtube.com, vkontakte.ru, odnoklassniki.ru, rostelecom.ru, support.akado.ru, my.mail.ru.
At the same time, many computers were infested by the second version of this Trojan.Mayachok program; its special feature was a modification of the volume boot record, after which it showed a message in the browser window claiming that the machine was infected by the Trojan.Win32.Ddox.ci Trojan horse. To solve the “problem” the criminals offered the victim the chance to update the browser by sending a paid message to a short number. The Trojan horse’s makers were diligent enough to design different banners for the most popular browsers: Microsoft Internet Explorer, Mozilla Firefox, Opera, and Google Chrome.
To eliminate these threats, users whose systems have been compromised by the Trojan horse programs Trojan.Mayachok.1 and Trojan.Mayachok.2, should scan the disks of their computer with Dr.Web or use the emergency system restore tools Dr.Web LiveCD or Dr.Web CureIt!.
Threats in mail traffic
Virus writers have not forgotten about one of the traditional schemes for spreading malicious programs: e-mail spam. In August, BackDoor.Pushnik.15, which steals electronic funds from WebMoney users, became the most frequently mailed malware. Downloader malware is also spread in large numbers via e-mail. For example, Trojan.DownLoad2.24758 was detected in e-mail traffic in 13.79% of the cases. The long-known Trojan.Oficla family is not far behind. Among other threats detected in August in mail traffic, we should mention different modifications of Win32.HLLM.MyDoom and also Trojan.Tenagour.3 and Win32.HLLM.Netsky.
Malicious files detected in mail traffic in August
| 01.08.2011 00:00 - 31.08.2011 17:00 | ||
| 1 | Trojan.DownLoad2.24758 | 150146 (26.36%) |
| 2 | Trojan.Oficla.zip | 123791 (21.73%) |
| 3 | Exploit.Cpllnk | 48091 (8.44%) |
| 4 | BackDoor.Pushnik.15 | 39771 (6.98%) |
| 5 | BackDoor.Pushnik.16 | 27612 (4.85%) |
| 6 | Trojan.Tenagour.3 | 21166 (3.72%) |
| 7 | Win32.HLLM.MyDoom.33808 | 18437 (3.24%) |
| 8 | Win32.HLLM.MyDoom.54464 | 15161 (2.66%) |
| 9 | Win32.HLLM.Netsky.18401 | 11308 (1.99%) |
| 10 | Trojan.DownLoad2.32643 | 7547 (1.32%) |
| 11 | Win32.HLLM.Netsky.35328 | 7503 (1.32%) |
| 12 | BackDoor.IRC.Nite.60 | 7383 (1.30%) |
| 13 | Win32.HLLM.Netsky | 6783 (1.19%) |
| 14 | Win32.HLLM.Beagle | 5135 (0.90%) |
| 15 | Trojan.Siggen2.58686 | 5090 (0.89%) |
| 16 | Trojan.Packed.246 | 4971 (0.87%) |
| 17 | Trojan.Carberp.13 | 4622 (0.81%) |
| 18 | Win32.HLLM.MyDoom.based | 4373 (0.77%) |
| 19 | Trojan.MulDrop1.54160 | 2981 (0.52%) |
| 20 | Trojan.Siggen3.345 | 2450 (0.43%) |
Total scanned: 243,888,860
Infected: 569,637 (0.23%)
Malicious files detected on user machines in August
| 01.08.2011 00:00 - 31.08.2011 17:00 | ||
| 1 | JS.Click.218 | 113154597 (58.49%) |
| 2 | Win32.Rmnet.12 | 26016817 (13.45%) |
| 3 | JS.IFrame.112 | 14774950 (7.64%) |
| 4 | Trojan.IFrameClick.3 | 10379698 (5.37%) |
| 5 | Win32.HLLP.Neshta | 7375872 (3.81%) |
| 6 | Trojan.MulDrop1.48542 | 3065544 (1.58%) |
| 7 | Win32.HLLP.Whboy.45 | 2091622 (1.08%) |
| 8 | JS.IFrame.117 | 1645574 (0.85%) |
| 9 | Win32.HLLP.Whboy.101 | 1403859 (0.73%) |
| 10 | JS.Click.222 | 1270764 (0.66%) |
| 11 | Win32.HLLP.Novosel | 1089446 (0.56%) |
| 12 | Win32.HLLW.Whboy | 1083364 (0.56%) |
| 13 | Trojan.Click.64310 | 810689 (0.42%) |
| 14 | ACAD.Pasdoc | 777253 (0.40%) |
| 15 | Trojan.DownLoader.42350 | 593013 (0.31%) |
| 16 | Trojan.NtRootKit.10544 | 477728 (0.25%) |
| 17 | JS.Click.232 | 422188 (0.22%) |
| 18 | JS.IFrame.95 | 412791 (0.21%) |
| 19 | HTTP.Content.Malformed | 408269 (0.21%) |
| 20 | Trojan.PWS.Ibank.323 | 384619 (0.20%) |
Total scanned: 129,475,241,055
Infected: 193,468,376 (0.15%)