Trojan attack warning for Counter-Strike fans
Real-time threat news | All the news | Virus alerts
August 5, 2011
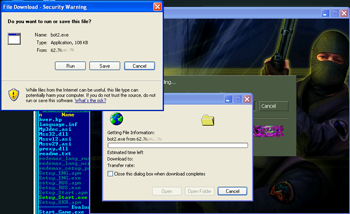
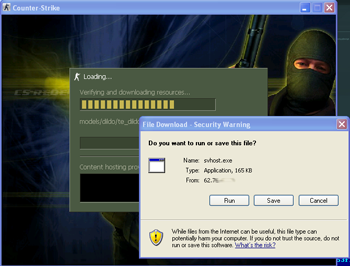
Typically, when a connection with a Counter-Strike server is established, the client downloads missing components required for the game from the remote host. In this case a user sees a standard browser dialogue prompting them to download two executable files (svhost.exe and bot2.exe) and the admin.cmd file (distributed as Counter-Strike.cmd at the beginning of this year). It should be noted that such behaviour is not typical of the Counter-Strike client.
An examination by Doctor Web's virus analysts revealed the following scheme. A group of attackers set up a Counter-Strike game server, distributing the Trojan horse Win32.HLLW.HLProxy (some time ago, this Trojan horse was spread among fans of Counter-Strike as a "useful" application, so many people downloaded and installed it on their PCs of their own free will).
The Trojan horse distribution mechanism was rather peculiar. When a user connected to the game server, the player was displayed a special MOTD welcome screen, which could feature server advertising or any set of rules defined by its administrators. The window's contained an HTML-file. The MOTD file created by criminals contained an IFRAME, which redirected the client to an intruders-controlled server. From this server the admin.cmd file is downloaded and launched on the victim's computer, this file contains the Trojan horse Win32.HLLW.HLProxy.
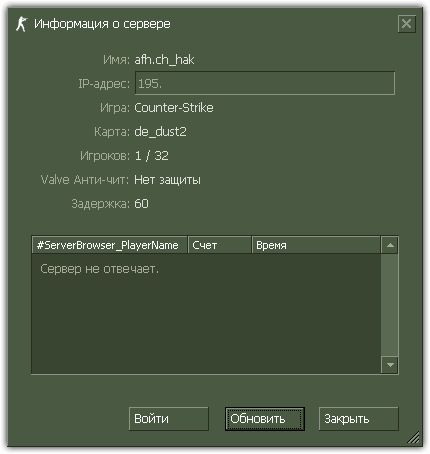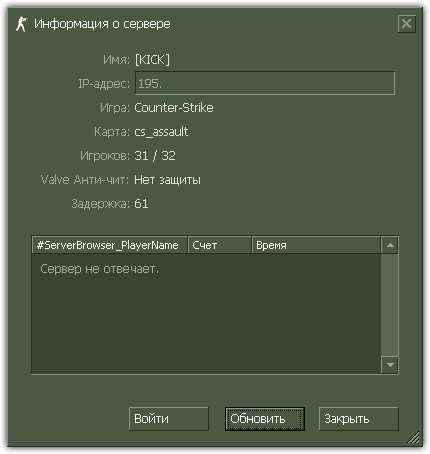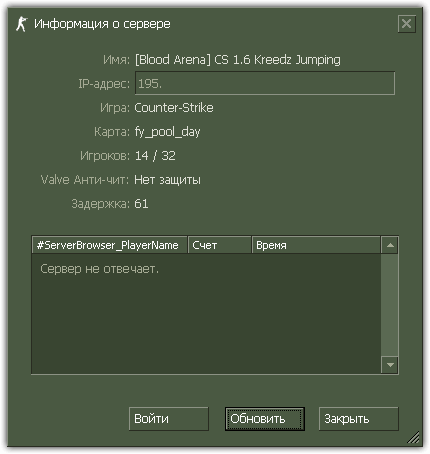
The main purpose of the Trojan horse is to launch on a player's computer a proxy server, which emulates several Counter-Strike game servers on the same machine and transmits corresponding information to servers belonging to VALVE. When accessing a game server emulated by the Trojan horse, the client software was redirected to a real game server controlled by the attackers, from which the player received the Trojan horse Win32.HLLW.HLProxy. So the number of infected machines increased exponentially. The screenshot below provides an illustration of the Trojan horse activity where several game servers with one IP address are supposedly running on an infected machine.
In addition, the Trojan horse can carry out DDoS-attacks on gaming servers and servers belonging to VALVE, so many of them might be unavailable in different periods of time. We can assume that one of the criminals' goals was to collect money from owners of game servers for bringing in new players, as well as DDoS-attacks on "unwanted" game servers. Currently, in addition to the Trojan horse users who connect to the server receive additional "gifts".
The analysis conducted by Doctor Web revealed that the svhost.exe file hides Trojan.Click1.55929. Once the Trojan horse gets into an infected system, it creates its copy named SVHOST.EXE in the C:\Program Files\Common Files folder, launches it and performs its malicious tasks. The file bot2.exe file conceals already well known Trojan.Mayachok.1.
At present the signatures of these threats are added into the Dr.Web virus database. Doctor Web recommends Counter-Strike fans to be vigilant: do not agree with browser prompts to download and install executable files onto your computer.
Doctor Web expresses its sincere thanks to the virus hunter Michael Mal'tsev for his help in identifying the threat.