Elimination of botnet and other viral events in March 2011
Virus reviews | All the news | Virus alerts
April 4, 2011
Trojan.Spambot botnet shut down
On March 17, 2011, the largest generator of spam, the Trojan.Spambot botnet, ceased its operation. Twenty-six command centers of the botnet became non-operational, and hundreds of thousands of bots, left without anything to control them, went into hibernation.
According to Microsoft, a computer infected with Trojan.Spambot could send up to 10,000 messages per hour. Some experts estimate that the number of bots in the spam network was around 815,000. Thus, the total spam traffic generated by the botnet Trojan.Spambot could reach several billion messages per day. Microsoft was said to have played a key part in a joint operation with US authorities to behead the Trojan.Spambot botnet.
Trojan.Spambot, the first known examples of which date back to 2005, became one of the most technologically advanced and complex malware species. Its developer perfected the program for several years, and an analysis of the Trojan's code served as the source of many analytical publications.
A civil lawsuit filed by Microsoft against the unidentified individuals behind this botnet became the legal basis of the operation. According to widespread belief, the attackers are of Russian origin.
It is still difficult to make predictions about the future of the spam industry. The significant damage caused by the closure of the largest spam networks can be quickly reversed by the growth of other botnets. Win32.HLLM.Beagle, whose activity in recent years was low, has taken the leading position as the largest generator of spam traffic. Both spam networks specialize in so-called “pharma spam”—the advertising of drugs.
In the future, we can expect botnet architecture to move towards decentralization. Also, some think that the Trojan.Spambot botnet will recover.
Trojan horses in terminals
In March 2011 Doctor Web announced the discovery of a new modification of Trojan.PWS.OSMP that infects express payment terminals. This Trojan horse modifies the account numbers of payment recipients. And its latest modification probably enables criminals to create virtual terminals.
Interestingly, the Trojan horse wasn't detected during the analysis of a compromised terminal but while monitoring the botnet of another Trojan horse that enables Trojan.PWS.OSMP to get into terminal systems.
A terminal is infected in two stages. First, the terminal is compromised by BackDoor.Pushnik, which is a 620 KB, packed executable file written in Delphi and spread via removable media. Once installed, the Trojan gets instructions from command centers and, after several intermediate steps, downloads and runs a 60-70 KB binary file containing Trojan.PWS.OSMP. It looks through the running processes in search of the maratl.exe process which is a part of the payment terminal software environment. If successful, the Trojan horse injects its code into the process and replaces the recipient’s account number in the process' memory with the criminal's account number.
The latest known version of the Trojan horse implements a different scheme of fraud. Trojan.PWS.OSMP copies a configuration file of the payment terminal to its server. A stolen configuration file is supposed to help criminals create a fake terminal on their computer, which should allow them to redirect transferred funds to their account.
New critical vulnerabilities in Adobe products
On March 14, 2011, Adobe Systems announced the discovery of another vulnerability in Adobe Flash Player 10.2.152.33 and in some of its earlier versions.
The vulnerability allows intruders to attack a system using an swf file. This vulnerability exists in the versions of the product for Windows, Mac OS, Linux, Solaris, and earlier versions of Android.
Updates closing the vulnerability were released only on March 21. Thus, the vulnerability remained unclosed for a week. Shortly afterwards, source code examples showing how the vulnerability was exploited became available to the public on the Internet.
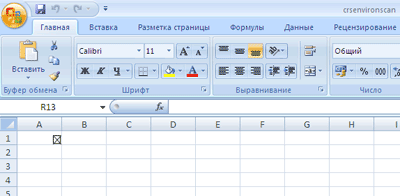
An attack is conducted by means of an xls file with an embedded swf object:
Figure 1. The embedded swf file in an Excel document.
This swf file loads shell-code into memory and then executes an attack on the vulnerable flash-player, using the Heap Spray technique. Then the swf file code loads a second swf file that exploits the vulnerability in the bytecode interpreter ActionScript CVE-2011-0609, common to all vulnerable systems.
The demonstration of the vulnerability provoked mailings of messages with an attached Trojan xls file that included Exploit.SWF.169. When the file is launched, MS Excel stops responding for some time, and the user sees an empty table with an embedded flash video clip that doesn't display anything.
Figure 2. Loading an MS Excel document containing Exploit.SWF.169.
Meanwhile Exploit.SWF.169 carries out a local attack. It saves to the disk and runs the executable file with the Trojan.MulDrop1.64014 or Trojan.MulDrop.13648 payload.
Attacks on social networking websites
Nowadays social networking websites are popular targets of hacker attacks. The last month provided another confirmation of that trend—LiveJournal and Facebook came under attack.
On March 4, 2011, a mass mailing of phishing emails sent on behalf of LiveJournal’s administration was carried out. Messages contained a notice about suspension and probable removal of LiveJournal accounts.
The sender field of the phishing emails contained the do-not-reply@livejournal.com address which is actually used to send notifications to LiveJournal users. A fraudulent link was provided to would-be victims; it directed them to a bogus website livejorrnal.com or xn--livejurnal-ivi.com.
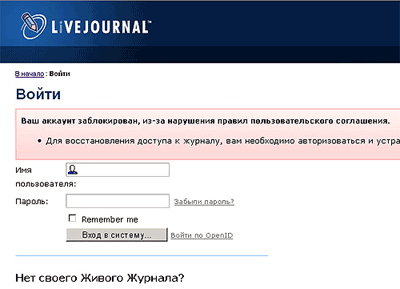
Users following the link ended up on a page that mimicked the original LiveJournal design. Data entered by users on the page was transmitted to fraudsters.
Figure 3. Fraudulent page that duplicates the look of LiveJournal.
A few days later Facebook suffered a similar attack. Its users began receiving spam messages sent on behalf of existing Facebook accounts. Such messages contained a short URL (the trick commonly employed for such attacks). It prevents users from learning beforehand where the link leads. In this case, it led to a fraudulent page that copied the Facebook design. This page contained a notification and prompted users to submit their personal information. If victims filled in the requested fields, the attacker gained access to their individual accounts and then used those accounts to send a similar fraudulent message to the friends on the victim's list.
Obviously, criminals continue to refine their social engineering techniques and methods in attacks via social networking sites.
On March 30, 2011, LiveJournal suffered another DDoS-attack. The service administration estimated it to be the largest in its history. The attack continued for several hours, and during this time the service was virtually unavailable.
A wave of spam related to the disaster in Japan
As expected, there were attackers ready to exploit others’ misfortune, and the disaster in Japan was followed by a wave of spam messages on corresponding topics.
Some samples of spam contained calls for donations, and the supposed senders included well-known charity organizations (Red Cross, Salvation Army, etc.).
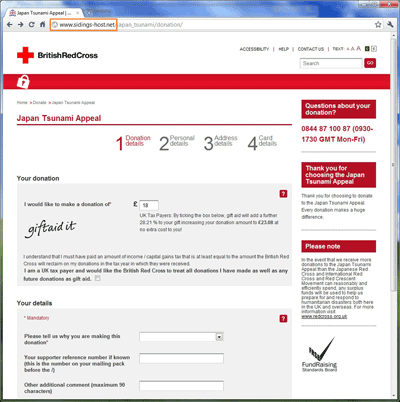
The message body usually contained a link to a fraudulent resource that was ready to accept donations.
Figure 4. Fake page for the Red Cross.
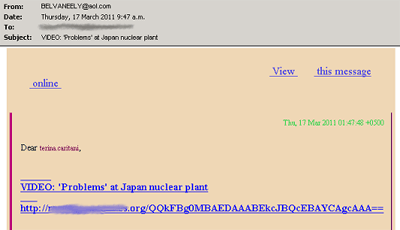
In other cases users were lured to malicious resources. For example, a message offered users the opportunity to watch a video of the disaster and provided a corresponding link.
Figure 5. Spam messages with a link to a Japan disaster video.
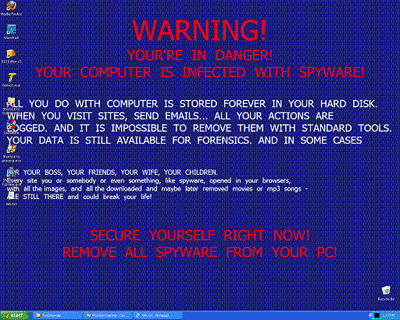
When the user tried to view the video, they were redirected to a malicious site from which Trojan.FakeAlert was installed onto their computer.
Figure 6. The result after attempting to view a Japan disaster video.
Criminals are taking advantage of this occasion to spread a wide range of Trojan software: fake anti-viruses and system utilities, and all kinds of blockers.
Viruses detected in March in mail traffic
| 01.03.2011 00:00 - 31.03.2011 01:00 | ||
| 1 | Trojan.Inject.28090 | 2517487 (9.89%) |
| 2 | Trojan.Inject.27975 | 2063777 (8.10%) |
| 3 | Trojan.DownLoad2.20306 | 1656904 (6.51%) |
| 4 | Trojan.DownLoader2.22364 | 1457945 (5.73%) |
| 5 | Trojan.Inject.28053 | 1358480 (5.33%) |
| 6 | Trojan.DownLoader2.265 | 1352313 (5.31%) |
| 7 | Win32.HLLM.MyDoom.33808 | 1184204 (4.65%) |
| 8 | Trojan.DownLoader2.17823 | 1057371 (4.15%) |
| 9 | Trojan.DownLoader2.1901 | 1030685 (4.05%) |
| 10 | Trojan.DownLoader2.2035 | 940626 (3.69%) |
| 11 | Trojan.DownLoader2.2977 | 837149 (3.29%) |
| 12 | Win32.HLLM.Netsky.18401 | 834193 (3.28%) |
| 13 | Trojan.DownLoader2.10188 | 682540 (2.68%) |
| 14 | Trojan.DownLoad1.58681 | 568003 (2.23%) |
| 15 | Trojan.DownLoader2.16572 | 563631 (2.21%) |
| 16 | Trojan.Packed.20878 | 409260 (1.61%) |
| 17 | Win32.HLLW.Texmer.51 | 404317 (1.59%) |
| 18 | Win32.HLLM.Netsky.35328 | 369690 (1.45%) |
| 19 | Trojan.MulDrop.64589 | 367488 (1.44%) |
| 20 | Trojan.DownLoad.41551 | 341949 (1.34%) |
| Total scanned: | 74,983,221,402 |
| Infected: | 25,463,678 (0.03%) |
Viruses detected in March on users' computers
| 01.03.2011 00:00 - 31.03.2011 01:00 | ||
| 1 | Win32.HLLP.Neshta | 16013222 (29.74%) |
| 2 | Win32.HLLP.Novosel | 11746302 (21.82%) |
| 3 | JS.IFrame.95 | 5125132 (9.52%) |
| 4 | Win32.HLLP.Whboy.45 | 4336264 (8.05%) |
| 5 | Win32.Siggen.8 | 3985715 (7.40%) |
| 6 | Win32.HLLW.Whboy | 2565223 (4.76%) |
| 7 | ACAD.Pasdoc | 1072822 (1.99%) |
| 8 | Trojan.MulDrop1.48542 | 486108 (0.90%) |
| 9 | Trojan.Click.64310 | 462653 (0.86%) |
| 10 | Win32.Antidot.1 | 455366 (0.85%) |
| 11 | JS.Click.22 | 393754 (0.73%) |
| 12 | Win32.HLLP.Whboy | 254289 (0.47%) |
| 13 | Win32.HLLW.Shadow.based | 241028 (0.45%) |
| 14 | Win32.Sector.22 | 229577 (0.43%) |
| 15 | Win32.HLLP.Rox | 216080 (0.40%) |
| 16 | Win32.Sector.12 | 204476 (0.38%) |
| 17 | Trojan.Packed.21230 | 186951 (0.35%) |
| 18 | Exploit.Cpllnk | 168504 (0.31%) |
| 19 | Win32.Virut.56 | 155258 (0.29%) |
| 20 | Trojan.DownLoad.32973 | 142519 (0.26%) |
| Total scanned: | 139,536,970,982 |
| Infected: | 53,840,333 (0.04%) |