March 24, 2022
Because of the hackers' mistake, we got a unique opportunity to study the lists of victims and find out what backdoor management tools were used. Based on the acquired information, we concluded that the hacker group specialized in compromising the Asian companies’ mail servers with Microsoft Exchange software installed. That said, we also found victims from other countries, including:
- Egyptian government agency
- Italian airport
- USA marketing company
- Canadian transport and woodworking companies
The logs collected along with the command and control server included victims infected from August 2021 to early November of the same year. Yet, in some cases, BackDoor.Whitebird.30 was installed not only on the server running Microsoft Exchange, but on domain controllers, too. Based on the tools, methods, and infrastructure used, we conclude that the Calypso APT hacker group is behind the attack.
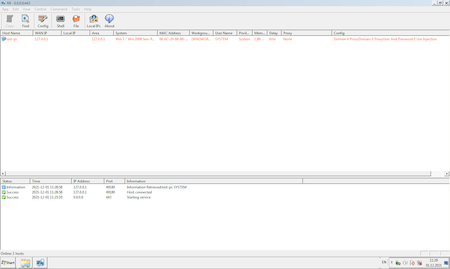
Remote Rover
Command and control server for BackDoor.Whitebird.30 calls Remote Rover. It allows hackers to remotely launch applications, update the backdoor configuration, download and upload files. Besides that, you can use a command shell via Remote Rover. This is what the control server interface looks like:
Remote Rover came with a configuration file CFG\default.ini with the following content:
E:\个人专用\自主研发远程\2021\RR\配置备份\telecom.cfg OneClock.exeIf you translate the content from Chinese into English, you can get this path:
E:\personal use\Independent research and development remote\2021\RR\Configuration backup\telecom.cfgFor a detailed description of the malware used and how it works, see the the PDF-version of the study or Dr.Web Virus Library.
- BackDoor.Siggen2.3622
- BackDoor.PlugX.93
- BackDoor.Whitebird.30
- Trojan.Loader.891
- Trojan.Loader.896
- Trojan.Uacbypass.21
- Trojan.DownLoader43.44599
Conclusion
During the investigation of the targeted attack, Doctor Web virus analysts found and described several backdoors and trojans. It’s worth noting that the attackers managed to remain undetected for as long as other targeted attack incidents. A hacker group compromised a telecommunications company's network more than two years ago.
Doctor Web specialists recommend regularly checking network resources’ efficiency and timely fixing failures that may indicate the presence of malware on the network. Data compromise is one of targeted attacks’ main dangers, but the long-term presence of intruders is also a cause for concern. Such development allows them to control the organization’s work for many years and gain access to especially sensitive information at the proper time. If you suspect malicious activity in the corporate network, the best option is to contact the Doctor Web virus laboratory for qualified help. Dr.Web FixIt! helps you to detect malware on servers and workstations. Taking adequate measures timely will minimize the damage and prevent the serious consequences of targeted attacks.

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments