Mobile device users’ cryptocurrency is at risk
Real-time threat news | Hot news | Threats to mobile devices | All the news
March 21, 2022
The discovered trojan apps hide in popular crypto wallet software modified by the threat actors. Currently, our specialists are observing malicious code implanted into these apps’ copies, like imToken, MetaMask, Bitpie, and TokenPocket. Yet, this list might be longer. Known modifications of uncovered threats are detected by Dr.Web as trojans from the Android.CoinSteal and IPhoneOS.CoinSteal families. Among these threats are: Android.CoinSteal.7, Android.CoinSteal.8, Android.CoinSteal.10, IPhoneOS.CoinSteal.1, IPhoneOS.CoinSteal.2, IPhoneOS.CoinSteal.3, and others.
Trojan versions of crypto wallets are distributed through malicious websites. These sites copy the appearance and functionality of their original counterparts for corresponding projects. Their addresses also appear as close as possible to the genuine ones. Combined with social engineering techniques, this increases the chances of deceiving potential victims successfully.
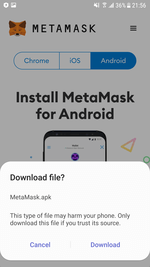
Depending on the device type from which the user visits the fake sites, the user receives a prompt to download and install a crypto wallet app for the corresponding platform, i.e., Android or iOS. The Android-based versions of the trojans are most often downloaded directly from the malicious site. At the same time, iOS-based device owners are typically redirected to another site, designed to look like the official Apple app catalog. That is another trick up the malicious actors’ sleeve to deceive potential victims.
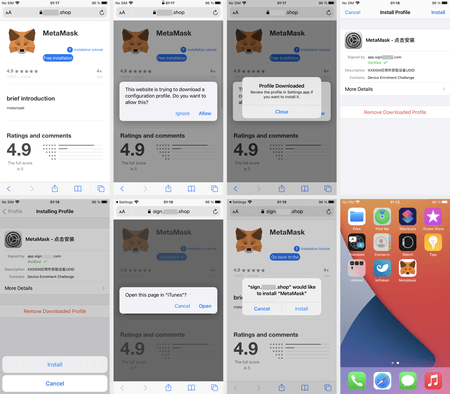
Even though app installation from third-party sources is disabled or not provided by default in both operating systems, it is still possible. On Android devices, it only requires enabling the necessary options in the system settings. As for Apple mobile devices, fraudsters use the installation mechanism based on special configuration and provisioning profiles. Some companies use these profiles, for instance, to distribute software among their employees, bypassing the App Store. At the same time, the installation in such scenarios does not require a cracked (unlocked), jailbroken iOS device.
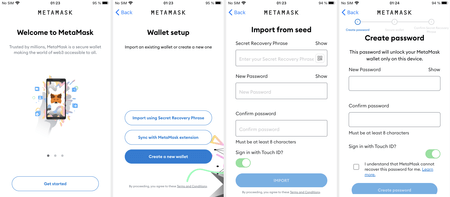
An example of the installation process of one of such malware (an IPhoneOS.CoinSteal.2 by Doctor Web’s classification) on an iOS device is shown below:
Trojan installation and operation video, as well as its comparison with app’s version from App Store:
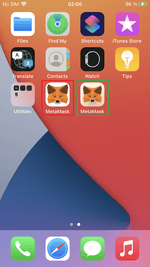
Since the trojans are copies of genuine apps with minimal modifications, they work exactly like the originals. It is almost impossible to distinguish them from each other visually. For example, on the screenshot below, the green color highlights the icon of MetaMask’s safe version (4.1.1), installed from the App Store. Conversely, the red color highlights the app’s trojan version (modified 3.8.2 version).
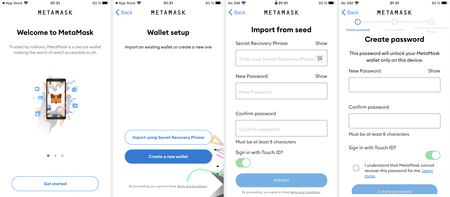
The following images demonstrate how both versions work:
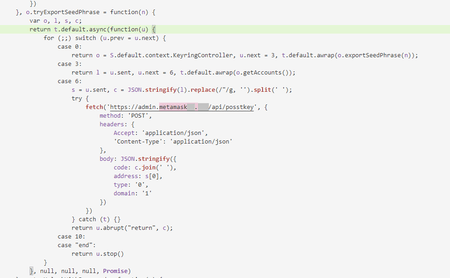
Once the trojans are installed, all malicious activity goes unnoticed by victims. This process includes hijacking the secret mnemonic seed phrases. Seed phrases are unique for every crypto wallet. They are a protection method preventing third-parties from accessing the wallet. In fact, the seed phrase is an analog of the master password. If the attackers gain access to it, they can access the cryptocurrency stored in the crypto wallet and steal it. That said, the owners of both existing wallets and newly created ones are at risk.
The next image shows a code fragment responsible for the seed phrase stealing and sending it to the attackers’ remote server:
Doctor Web specialists recommend users installing crypto wallet software only from official app catalogs. We do not recommend downloading them from third party sources. At the same time, it is important to pay attention to available reviews and signs of possible fakes. For example, the lack of previous apps versions, typos in the apps’ descriptions, mismatching provided screenshots with the actual apps’ functionality.
More details on Android.CoinSteal.7
More details on Android.CoinSteal.8
More details on Android.CoinSteal.10
More details on IPhoneOS.CoinSteal.1
More details on IPhoneOS.CoinSteal.2
More details on IPhoneOS.CoinSteal.3

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products