New mining Trojan for Linux removes anti-viruses
Real-time threat news | Hot news | All the news | Virus alerts
November 20, 2018
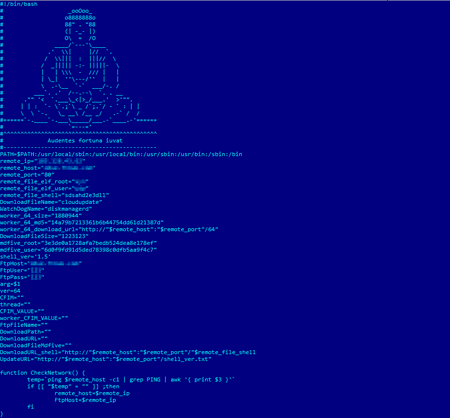
The Trojan, added to the Dr.Web virus databases as Linux.BtcMine.174, is a big shell script containing over 1,000 lines of code. This malware consists of several components. When launched, the Trojan verifies that the server from which it will subsequently download other modules is available and searches on the disk for a folder with write permissions into which these modules are then loaded. After that, the script is moved to the previously selected folder named diskmanagerd and, using the utility nohup, is re-launched as a daemon. If no such utility exists in the system, the Trojan automatically downloads and installs the coreutils package which includes nohup.
Once successfully installed, the malicious script downloads a version of the Linux.BackDoor.Gates.9 Trojan. This family of backdoors allows the commands issued by cybercriminals to be executed and DDoS attacks to be carried out.
Once installed in the system, Linux.BtcMine.174 searches for competing miners and terminates their processes when it detects them. If Linux.BtcMine.174 is not launched as root, it uses a number of exploits to escalate its privileges in the infected system. Doctor Web malware analysts have detected at least two exploits used by Linux.BtcMine.174: Linux.Exploit.CVE-2016-5195 (also known as DirtyCow) and Linux.Exploit.CVE-2013-2094. The Trojan downloads DirtyCow source files from the Internet and compiles them right on an infected machine.
After that, the malware tries to find running anti-virus software services with the names safedog, aegis, yunsuo, clamd, avast, avgd, cmdavd, cmdmgd, drweb-configd, drweb-spider-kmod, esets, and xmirrord. If it detects them, the Trojan does not simply end the antivirus’s process, but also uses package managers to remove its files as well as the directory in which the product was installed.
Then Linux.BtcMine.174 adds itself to the Autorun list and downloads and launches a rootkit on the infected device. This module is also an sh script based on public source code. Among the rootkit module’s notable features is the ability to steal user-entered passwords for the su command and to hide files in the file system, network connections, and running processes. The Trojan collects data on hosts the machine had previously connected to via SSH and tries to infect them.
After completing all these steps, Linux.BtcMine.174 launches a Monero (XMR) miner in the system. The Trojan checks every minute to see whether the miner is running and, if necessary, automatically restarts it. It also connects to the management server in a continuous loop to download any available updates.
Linux.BtcMine.174, as well as all of its components, is successfully detected by Dr.Web Anti-virus for Linux and poses no threat to our users.
The full list of indicators of compromise can be found here: https://github.com/DoctorWebLtd/malware-iocs/tree/master/Linux.BtcMine.174.
#Linux #cryptocurrency #mining #Trojan