Banking Trojan attacks European users of Android devices
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
November 16, 2018
The Trojan, dubbed Android.Banker.2876, was being distributed under the guise of the official applications of European financial institutions: Spain’s Bankia, Banco Bilbao Vizcaya Argentaria (BBVA), and Santander; France’s Credit Agricole and Groupe Banque Populaire; and Germany’s Postbank. Our experts have found a total of six modifications of Android.Banker.2876. All of them were promptly removed from Google Play after Doctor Web contacted Google.
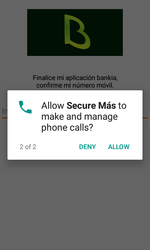
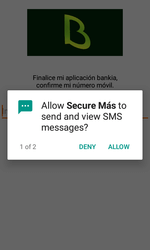
Once launched by a user, the Trojan requests permission to manage and make phone calls and send and receive SMS. Android devices below version 6.0 automatically grant these permissions during the Trojan’s installation. See the below example of a request:
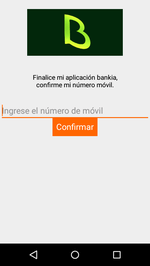
Android.Banker.2876 collects and sends confidential information—the mobile device’s phone number and SIM card data, as well as a number of specifications about the mobile device—to the Firebase cloud and then notifies the attackers that the device has been infected successfully. The Trojan then displays a dialog requiring the victim to enter their phone number to continue working with the program. Each modification of the banker Trojan is designed for a specific audience. For example, if the Trojan is disguised as the application of a Spanish bank, the interface of Android.Banker.2876 and the displayed text will be in Spanish.
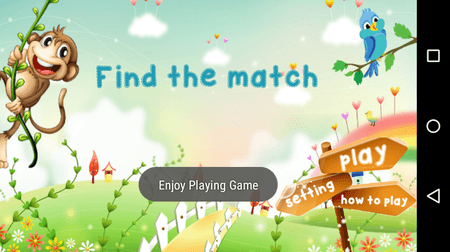
The phone number entered by the victim is transferred to the cloud database. The user is then shown a second dialog telling them to wait for “registration” confirmation. The dialog has a “Submit” button. When pressed, it launches a game built into the Android.Banker.2876, startling the user.
If the Trojan was successful when it uploaded the information about the mobile device to the cloud, it hides its icon from the home screen and then automatically runs in the background whenever the infected smartphone or tablet is on.
Android.Banker.2876 intercepts all incoming SMS and stores their contents in a local database. The text in the messages is uploaded to Firebase and is also distributed via SMS to the cybercriminals’ mobile number. As a result, the attackers are able to obtain one-time passwords used to confirm bank transactions and other confidential data that can be used for phishing attacks. In addition, the phone numbers collected by the Trojan can help the malware’s developers arrange fraudulent campaigns.
All known modifications of Android.Banker.2876 are successfully detected and removed by Dr.Web for Android, so they do not pose any threat to our users.
#Android, #Google_Play, #banking_Trojan, #phishing, #fraud
Your Android needs protection
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 135 million downloads on Google Play alone
- Free for users of Dr.Web home products