Doctor Web warns of a miner Trojan downloaded instead of a program update
Real-time threat news | Hot news | All the news | Virus alerts
July 9, 2018
One of our users informed our technical support that Dr.Web Anti-virus constantly detected and deleted an application for mining cryptocurrency. An examination of the Anti-virus logs showed that the miner hid in the temporary folder on the infected computer. In addition, the application attempted to connect with an IP address corresponding to the website of the Astrum Soft company, the manufacturer of “Kompiuternyi Zal”. This software is designed to automate computer clubs and cybercafes.
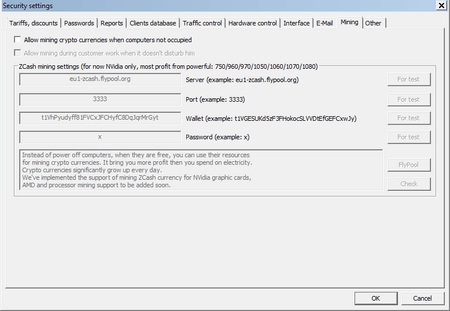
Officially, a function for mining cryptocurrency exists in the application. Users can enable it when computers are idle.
Nevertheless, further research showed that a miner which bothered the user and not the “Kompiuternyi Zal” application had been hidden. The miner was added to the Dr.Web virus databases as Trojan.BtcMine.2869. This Trojan was automatically downloaded from the servers of the Astrum Soft company via the update mechanism of the “Kompiuternyi Zal” program. The Trojan then installed itself into the system.
The “Kompiuternyi Zal” application periodically sends a request to the manufacturer server. This request contains an application version number and information about the system. The server can reply with a command to download and launch an executable file that is supposed to have an update feature for the program. However, the examined sample contains the file with malicious functionality. This malicious software closes the svchostm.exe and svcnost.exe processes, saves the mining Trojan to the computer, and modifies the Windows system registry key so the malicious software can launch automatically. Data on the wallet, where the mined cryptocurrency is transferred, is hardcoded in the Trojan’s body. After a user uninstalls the malicious software, the update mechanism can download and launch it again.
By July 9, security researchers have counted over 2700 computers infected by Trojan.BtcMine.2869. In the examined Trojan’s sample downloaded from the Astrum Soft server, names of infected computers (workers) start with the "soyuz6_" prefix. This prefix is hardcoded in the Trojan’s body. As of today, there are 613 "soyuz6_" infected computers. The Trojan was distributed over the May 24–July 4, 2018 period. The software company Astrum Soft and law enforcement were informed about the incident.
#malicious_software #cryptocurrencies #mining #Trojan