Virus news of August 2010
Virus reviews | All the news | Virus alerts
Rootkit for 64-bit systems
As our 2009 virus activity review predicted, the first rootkit for 64-bit systems made its debut. The new version of BackDoor.Tdss brought new challenges to security software developers.
Windows operating systems for the 64-bit platform feature defence mechanisms that prevent the installation of malicious drivers — the system checks whether the driver has a digital signature while the PatchGuard technology doesn’t allow malware to modify the OS kernel. However, the new BackDoor.Tdss successfully bypasses the obstacles by means of a bootkit, which, once installed, allows the backdoor to modify the MBR and take control of the operating system loading process. It allows the rootkit driver to be installed in the system before the defence mechanisms are activated.
Currently the Dr.Web virus database contains entries that allow the anti-virus to detect various modifications of the new BackDoor.Tdss. On September 1, 2010, Doctor Web released its updated GUI Scanner for 32-bit systems. Development of a 64-bit version of the Dr.Web Shield anti-rootkit is underway; it will be made available to all Dr.Web users shortly.
Malicious programs for Android
On August 26, Doctor Web released a new product — Dr.Web for Android. It came out at just the right moment, with entries for several modifications of Android.MobileSpy programs and Android.SMSSend.2 added into the Dr.Web virus database. Android.SMSSend.2 is a malicious program that sends paid short messages from a compromised device without its owner’s consent.
None of the known malicious programs for Android is capable of self-replication. This means that users must be lured into installing such programs into their systems. Yet all of them pose a threat to personal information stored on devices as well as to users’ cell phone accounts.
Despite the fact that prior to installation a user is informed about which Android features the application is going to use, criminals resort to various social engineering techniques to make a victim disregard such messages. Malicious programs are offered to users as games, screen savers, and applications that disguise their malicious intentions behind harmless features. Spyware can also be installed if an intruder gets access to a device belonging to a careless user.
Pay to extract
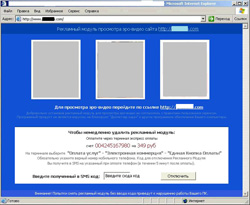
In August, a large number of malicious sites with the same look and feel as popular web sites specializing in film, song and e-book archives were discovered.
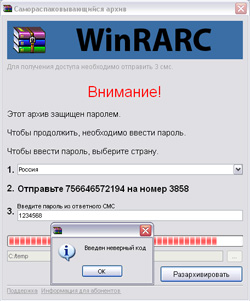
These malicious sites allow a user to download an 8-16 megabyte executable file, the likes of which are detected as Trojan.SMSSend modifications by Dr.Web. The files look like self-extracting archives, and launching such files brings up a window supposedly displaying how the extraction is progressing. However, at a certain moment, the progress bar stops and the user is prompted to send a paid short message from his mobile phone in order to complete the process. Ultimately the user is deceived twice –several hundred roubles are debited from the mobile account and no useful information is found in the archive.
Criminals resorting to such fraud create sites featuring design elements resembling known Internet services (Google, Yandex) or popular software products (WinRAR) which violates the copyright of the owners of these brands.
Trust, but verify!
In August, two intrusion schemes showed how easily a user can be tricked into launching a malicious program. In both cases victims received messages supposedly from their trusted contacts, who in turn were also victims of the malicious schemes.
On August 16, Win32.HLLW.Natchswas spread over ICQ. The program ends operation of popular ICQ clients, retrieves an ICQ account password, connects to a server using the account information and sends itself to contacts on the list of the compromised account. Win32.HLLW.Natchs can also maintain a simple conversation with a potential victim and transfer its files via the ICQ protocol instead of offering a download link. These abilities added credibility to malicious messages.
On August 30, spam messages were reportedly being distributed among Facebook users. Messages contained a link to a specifically designed application available on the social networking web site. The application exploited a Facebook vulnerability that allows messages to be sent to everyone on the “friends list” of the user who clicks on the link. With this act, criminals demonstrated the great malicious potential of applications uploaded onto social networking sites.
Doctor Web recommends that you exercise caution whenever you get a message with an attached executable file or containing a link to an unfamiliar web site even if such a message is from a trusted contact. If you’ve received such a message, you should contact the supposed sender by another means to make sure that he indeed sent the message.
Crime and punishment
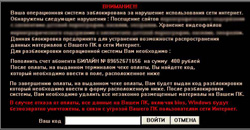
In August, Moscow law enforcement agencies–for the first time in history–launched an official criminal investigation against extortionists who used Windows blockers (Trojan.Winlock programs as classified by Dr.Web). The criminals had been in operation for the previous 12 months. Law enforcement agencies hope that the investigation will be supported by the entire telecom community. For its part, Doctor Web thanks all users who provided information about the latest modifications of blocker programs.
Also last month, the number of detections of Trojan.Winlock dropped by 50 percent and reached 140,000 instances of detections per month. However, roughly 100 people a day are applying to Doctor Web for support in cases related to Internet fraud.
The top spots on this month’s rankings list of the most prolific blockers went to two modifications of Windows blockers, neither of which involved demanding payment via short messages. Instead users were offered to either have their money credited to a mobile phone account or transferred by means of electronic payment systems.
Other news
Exploit.Cpllnk–the program that exploits a Windows vulnerability to launch malware from removable data-storage devices–was the most frequently detected malicious program on user machines in August. However, incidences of its detection dropped in the last days of the month.
Users in Europe remained the targets of banking Trojans that resulted in tougher security measures being introduced. This involved entering a large number of single-use codes on Internet banking web sites to safeguard transactions. The number of such codes has increased from 20 to 40.
Fake anti-viruses (Trojan.Fakealert) spread in Europe as well as in Russia. European users were prompted to pay for a bogus anti-virus with their credit cards, while Russians were typically pushed into sending paid short messages. To compel Russian users into paying for the fake, images from adult-content web sites would be displayed, leading them to believe that malicious programs had entered their systems. It was claimed that the bogus anti-virus would help users eliminate such “infections”.
Client software for the Oficla botent (Trojan.Oficla) and Trojan.PWS.Panda password stealers were spread via e-mail.
September will most likely see more revelations regarding the 64-bit rootkit. Some anti-virus vendors will probably enhance their products with features that will allow them to cure systems of the rootkit. The number of ransomware species appears to be on the decline, while e-mail will most likely remain one of the basic means of spreading malware in the months to come.
Malicious files detected in mail traffic in August
| 01.07.2010 00:00 — 01.08.2010 00:00 | ||
|
1
|
245764 (13,62%)
| |
|
2
|
212565 (11,78%)
| |
|
3
|
207763 (11,51%)
| |
|
4
|
198346 (10,99%)
| |
|
5
|
126509 (7,01%)
| |
|
6
|
81090 (4,49%)
| |
|
7
|
72949 (4,04%)
| |
|
8
|
58206 (3,22%)
| |
|
9
|
51422 (2,85%)
| |
|
10
|
46564 (2,58%)
| |
|
11
|
45415 (2,52%)
| |
|
12
|
38610 (2,14%)
| |
|
13
|
35934 (1,99%)
| |
|
14
|
33936 (1,88%)
| |
|
15
|
27392 (1,52%)
| |
|
16
|
25509 (1,41%)
| |
|
17
|
25469 (1,41%)
| |
|
18
|
23430 (1,30%)
| |
|
19
|
21457 (1,19%)
| |
|
20
|
21093 (1,17%) | |
| Total scanned: | 12,924,385,092 |
| Infected: | 1,804,893 (0,01%) |
Malicious files detected on user machines in August
| 01.07.2010 00:00 — 01.08.2010 00:00 | ||
|
1
|
2323984 (18,74%)
| |
|
2
|
1371549 (11,06%)
| |
|
3
|
992910 (8,01%)
| |
|
4
|
630531 (5,09%)
| |
|
5
|
521687 (4,21%)
| |
|
6
|
376117 (3,03%)
| |
|
7
|
348662 (2,81%)
| |
|
8
|
282339 (2,28%)
| |
|
9
|
258509 (2,09%)
| |
|
10
|
248243 (2,00%)
| |
|
11
|
218202 (1,76%)
| |
|
12
|
215135 (1,74%)
| |
|
13
|
212685 (1,72%)
| |
|
14
|
188934 (1,52%)
| |
|
15
|
181195 (1,46%)
| |
|
16
|
149215 (1,20%)
| |
|
17
|
146271 (1,18%)
| |
|
18
|
121070 (0,98%)
| |
|
19
|
118002 (0,95%)
| |
|
20
|
105532 (0,85%) | |
| Total scanned: | 65,191,497,071 |
| Infected: | 12,398,403 (0,02%) |