BadRabbit fears Dr.Web-protected computers: Our research on the infamous Trojan
Real-time threat news | Hot news | All the news | Virus alerts
October 26, 2017
Trojan.BadRabbit contains at least three components: a dropper, an encryption worm, and a disk encoder that is also capable of decoding. Once launched, the dropper is entirely loaded to the memory. The dropper’s samples are presented as an executable file with the icon of the Adobe Flash installer. Then the Trojan saves the encryption worm to the file C:\Windows\infpub.dat and runs it using the system program rundll32.exe. It then shuts down its own process.
The Trojan gathers information on the infected computer and also checks whether the processes of the two anti-virus programs have been launched: Dr.Web and McAfee (it is particularly interested in processes named dwengine.exe, dwwatcher.exe, dwarkdaemon.exe, dwservice.exe, McTray.exe, mfevtps.exe, and mcshield.exe). If BadRabbit detects such processes, it skips the first encryption stage in an apparent effort to avoid early detection. However, it attempts to run full disk encryption after a system’s restart. Due to the fact that current Dr.Web Anti-virus versions do not allow the boot record (MBR) to be modified, any attempt to encrypt disks will be unsuccessful. Thus, users of Dr.Web Anti-virus 9.1 and later and Dr.Web KATANA are completely protected from Trojan.BadRabbit provided they have not disabled the preventive protection component or changed its settings.
The disk encoder then checks the arguments of its process, and if it is running without arguments, it operates as a decoder. Before starting its encrypting activities, Trojan.BadRabbit makes a number of preparations and then creates a task in the Task Manager to restart he computer in 3 minutes. Then every 30 seconds the Trojan deletes the previous task and creates a new one, thus shifting the time for the task’s execution. Perhaps, this is done in the event the computer’s user deletes the Trojan before disk encryption is complete.
Then BadRabbit generates a 32-symbol password for disk encryption, records information about the computer to a special structure, encrypts it with a public key, and saves it in another structure, which is encoded with the Base64 algorithm and saved to MBR. The virus writers took disk encryption algorithm and a bootloader from the open source code Diskcryptor project and made some minor changes. The Trojan searches for the first system disk and installs its loader there. Then the contents of this disk are encrypted.
Part of BadRabbit’s code was adopted from Trojan.Encoder.12544, also known as NotPetya. Once launched, this encoder checks for the availability of the file C:\Windows\cscc.dat, and if this file is present, the Trojan shuts itself down (thus, creating the file cscc.dat in the C:\Windows folder can prevent the malicious consequences of the Trojan’s launch). Once launched from the memory of the infected computer, the encryption worm checks whether it has the privileges needed to extract one of its two drivers, depending on the system’s bitness. These drivers are taken from a tool for encrypting files with open source DiskCryptor code.
To launch these drivers, in the course of its operation, BadRabbit tries to register the system service “cscc” with the description “Windows Client Side Caching DDriver”. If the Trojan fails to register this service, it attempts to launch the DiskCryptor driver named “cdfs” by modifying the system registry.
Just like Trojan.Encoder.12544, Trojan.BadRabbit uses Mimikatz tools to intercept passwords of open Windows sessions. Depending on an operating system’s capacity, the Trojan unpacks the respective version of the tool, saves it with an arbitrary name to the C:\Windows folder, and then runs it. Then it searches for network folders available for writing, tries to open them using the obtained account data, and save its copy there.
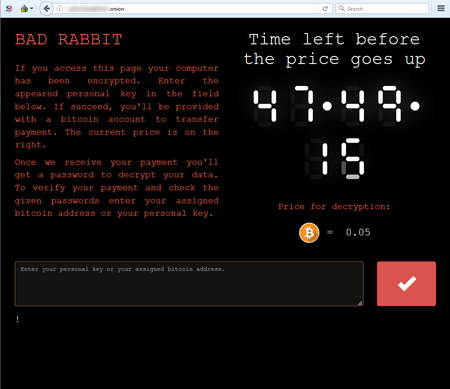
After executing all of its preliminary operations, the Trojan creates a task called “drogon” to restart the computer. While finishing the session, BadRabbit clears system logs and removes the task it created earlier. The encoder encrypts files with the following extensions: .3ds, .7z, .accdb, .ai, .asm, .asp, .aspx, .avhd, .back, .bak, .bmp, .brw, .c, .cab, .cc, .cer, .cfg, .conf, .cpp, .crt, .cs, .ctl, .cxx, .dbf, .der, .dib, .disk, .djvu, .doc, .docx, .dwg, .eml, .fdb, .gz, .h, .hdd, .hpp, .hxx, .iso, .java, .jfif, .jpe, .jpeg, .jpg, .js, .kdbx, .key, .mail, .mdb, .msg, .nrg, .odc, .odf, .odg, .odi, .odm, .odp, .ods, .odt, .ora, .ost, .ova, .ovf, .p12, .p7b, .p7c, .pdf, .pem, .pfx, .php, .pmf, .png, .ppt, .pptx, .ps1, .pst, .pvi, .py, .pyc, .pyw, .qcow, .qcow2, .rar, .rb, .rtf, .scm, .sln, .sql, .tar, .tib, .tif, .tiff, .vb, .vbox, .vbs, .vcb, .vdi, .vfd, .vhd, .vhdx, .vmc, .vmdk, .vmsd, .vmtm, .vmx, .vsdx, .vsv, .work, .xls, .xlsx, .xml, .xvd, .zip. As the result of the Trojan's operation, the infected computer displays a demand for a ransom in Bitcoin, and a website of cybercriminals in TOR states that a victim has 48 hours to pay. When the time expires, the ransom is increased.
Our investigation into Trojan.BadRabbit continues. We have published details pertaining to this malicious program’s operation in our virus knowledge database.
#virus #ransom #Trojan #Trojan.Encoder