Doctor Web: Dangerous Android banking Trojan gains control over mobile devices
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
July 18, 2017
Android.BankBot.211.origin is distributed under the guise of benign programs, for example, as Adobe Flash Player. Once a user installs and launches the Trojan, the banker tries to gain access to the Accessibility Service. For this purpose, Android.BankBot.211.origin displays a window with a request that reappears at every attempt to close it and doesn’t allow the device to be used.
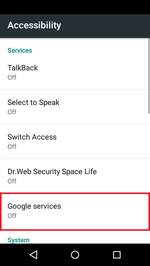
The Accessibility Service makes it easier to work with Android smartphones and tablets and is used in a variety of ways, including to help people with disabilities. It allows programs to independently click on different interface elements, such as buttons in dialog boxes and system menus. The Trojan forces the user to grant it these rights and uses them to independently add itself to the device administrator list. Then Android.BankBot.211.origin establishes itself as the default message manager and gains access to the screen capture function. All these actions are accompanied by a display of system requests that can be overlooked entirely because the malicious program immediately confirms them. If, at a later stage, the device owner tries to disable any function obtained by Android.BankBot.211.origin, the banker forbids it and returns the user to previous system menus.
After a successful infection, the Trojan connects to its command and control service, registers the mobile device there, and awaits further commands. Android.BankBot.211.origin can execute the following actions:
- Send an SMS containing a specific text to the number specified in the command;
- Send to the server SMS data stored in the device memory;
- Forward to the server information about the installed applications, the contact list, and phone call data;
- Open the link specified in a command;
- Change the address of the command center.
In addition, the malicious program tracks all incoming SMS and sends them to cybercriminals.
Besides the standard commands, cybercriminals can send the Trojan special orders. They contain encrypted information about the applications the banker is supposed to attack. Once Android.BankBot.211.origin receives such commands, it can:
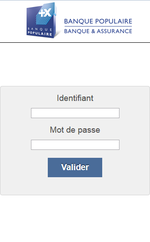
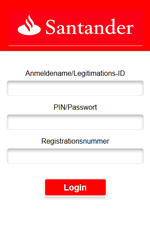
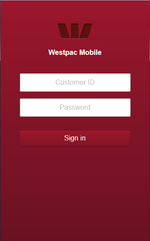
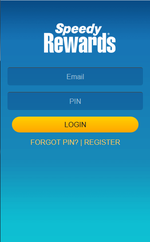
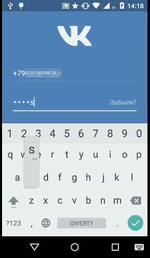
- Display fake input forms for login credentials on top of launched banking programs;
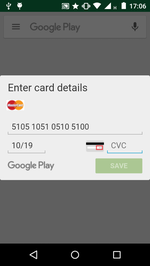
- Display a phishing dialog asking users to input their bank card details (for example, when making a purchase on Google Play);
- Block the operation of anti-viruses and other applications that could interfere with the Trojan’s work.
Android.BankBot.211.origin can attack users of any applications. Cybercriminals just have to update the configuration file with the list of targeted programs. The banker receives this list once connected to the command and control server. When the Trojan was first observed, cybercriminals were interested only in customers of Turkish banks. However, later on the list was expanded to include residents of other countries, including Germany, Australia, Poland, France, the United Kingdom, and the USA. At the moment this news article was posted, the list of programs attacked by the Trojan contained more than 50 applications designed to operate with payment systems, remote banking services (RBS), and other software.
Examples of the fraudulent windows Android.BankBot.211.origin can display:
The Trojan also collects information about all launched applications and user’s actions performed within them. For example, it tracks available text fields, such as menu elements, and logs key strokes and other components of the user interface.
Moreover, Android.BankBot.211.origin is capable of stealing login credentials and other authentication information input by users in any programs on any websites during authorization. To steal passwords, the Trojan takes a screenshot of every key stroke; as a result, it obtains the required sequence of characters before they are hidden. After that, the information input into the displayed fields and all the saved screenshots are sent to the command and control server.
Due to the fact that Android.BankBot.211.origin prevents anyone from removing it, the following actions must be performed in order to combat it:
- Load an infected smartphone or tablet in safe mode;
- Log into the system settings and go to the list of device administrators;
- Find the Trojan in this list and recall the corresponding rights (here the malicious program will try to frighten the device’s owner by warning them about the possible loss of all of their important data, but this is just a trick—the files are in no danger);
- Restart the device, perform a full anti-virus scan on it, and remove the Trojan after the scanning is complete.
All known versions of Android.BankBot.211.origin are successfully detected by Dr.Web Anti-virus; therefore, this banker does not pose any threat to our users.