Doctor Web examines two Linux Trojans
Real-time threat news | Hot news | All the news | Virus alerts
June 5, 2017
The first of the two was added to the Dr.Web virus databases under the name Linux.MulDrop.14. This malicious program attacks only Raspberry Pi minicomputers. Criminals started distributing Linux.MulDrop.14 in the second half of May. The Trojan is a script that contains a compressed and encrypted application designed to mine cryptocurrency. Linux.MulDrop.14 changes the password on the devices it infects, unpacks and launches a miner, and then, in an infinite loop, starts searching for network nodes with an open port 22. After establishing a connection with them via the SSH protocol, the Trojan attempts to run a copy of itself on them.
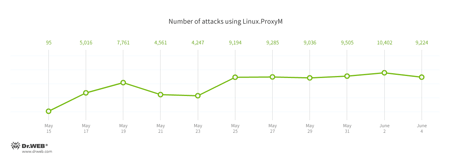
The other Trojan was named Linux.ProxyM. Attacks involving this Trojan have been noted since February 2017 but peaked in late May. The below chart shows how many Linux.ProxyM attacks Doctor Web specialists have pinpointed:
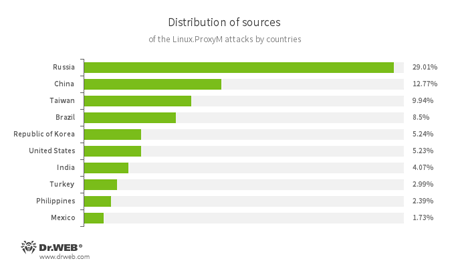
A significant portion of the attacked IP addresses is located in Russia. In second place is China, and in third place—Taiwan. The below illustration shows the geographical locations from which Linux.ProxyM attacks have been launched:
The Trojan uses a special range of methods to detect honeypots—special decoy servers used by digital security specialists to examine malicious software. Once launched, it connects to its command and control server and, after getting confirmation from it, runs a SOCKS proxy server on the infected device. Cybercriminals can use this Trojan to ensure that they remain anonymous online.
Both of these Trojans are successfully detected and removed by Dr.Web products for Linux, and, therefore, they pose no threat to our users.