Doctor Web warns of malicious mailing
Real-time threat news | Hot news | All the news | Virus alerts
April 13, 2017
The mass mailing of malicious attachments is one of the most popular Trojan distribution methods. Cybercriminals try to compose a message in a manner that will make the recipient open the attached file which subsequently infects their computer.
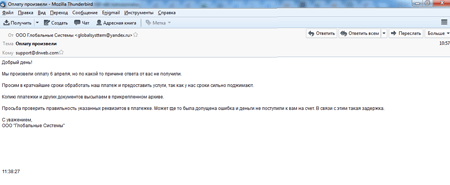
Over the past few days, emails with the subject header “Made the payment” have been distributed on behalf of a certain LLC Globalniye Sistemy (“Global Systems”). These letters contain the following text (the author’s syntax and spelling have been preserved):
Good day!
We made the payment on April, 6, but for some reason we haven’t received an answer from you.
We hereby request to process the payment as soon as possible and provide the services because time is an issue for us.
The copy of the billing statement and other documents are in the attached archive.
Please, check the details of the billing statement. Perhaps there has been a mistake that caused the failure in delivery of our payment. It could be the reason for the delay.
Yours faithfully,
LLC Globalniye Sistemy
The email has an attached archive called “Billing from LLC Globalniye Sistemy April 6 2017.JPG.zip” that is more than 4 MB in size. It contains an executable file with the extension .JPG[several dozen spaces].exe which was added to the Dr.Web virus database under the name Trojan.MulDrop7.24844. If a user tries opening this “image”, the program is launched for execution.
The application is a packed container that was created using the capabilities of the Autoit language. On launch the program checks whether it is running as the sole copy, and then saves a library to a disk in order to bypass User Accounts Control (UAC) on 32-bit and 64-bit versions of Windows and some other files. Then Trojan.MulDrop7.24844 registers itself in the autorun: on Windows XP—by modifying the system register; on newer versions of Windows—using Task Scheduler. The Trojan also tries to extract and save Google Chrome and Mozilla Firefox passwords in a text file.
One of the components launched by Trojan.MulDrop7.24844 on infected computers is an application for remote administration. Dr.Web Anti-virus detects it as Program.RemoteAdmin.753.
Another component of the Trojan, xservice.bin, which is also an encrypted Autoit container, extracts two executable files on a disk. These programs are 32-bit and 64-bit versions of the Mimikatz tool, which is designed to intercept passwords of open Windows sessions. xservice.bin can be launched with different keys. They influence the actions this file performs on infected computers.
| key | Description |
|---|---|
| -help | display possible keys (support information is displayed in unknown encoding) |
| -screen | makes a screenshot, saves it as a file called Screen(<HOURS>_<MINUTES>).jpg (<HOURS>_<MINUTES> stands for the current time) and sets file attributes to “hidden” and “system” |
| -wallpaper <path> | changes wallpaper to the one indicated in the parameter <path> |
| -opencd | opens CD drive |
| -closecd | closes CD drive |
| -offdesktop | prints to the console the following text: “Not working =(” |
| -ondesktop | prints to the console the following text: “Not working =(” |
| -rdp | RDP launch (look below) |
| -getip | receives IP address of the infected computer using the following website: http://ident.me/ |
| -msg <type> <title> <msg> | creates a dialog of the given type (err, notice, qst, inf) with a specified header and text |
| -banurl <url> | adds to the file %windir%\System32\drivers\etc\hosts the following string: “127.0.0.1 <url>”, where <url> is a command argument |
This application also activates a keylogger that records to the file any information about the keys pressed by a user. It also takes a screenshot at the moment of launch.
The Trojan gives criminals access to the infected device via RDP (Remote Desktop Protocol). For this purpose, it downloads a program called Rdpwrap from the Github server and installs it with parameters that allow it to run in the hidden mode. Dr.Web Anti-virus detects it as Program.Rdpwrap. Then Trojan.MulDrop7.24844 tries to get the password of the current user account with the help of the Mimikatz tool that was saved on the disk earlier. This password is saved in the system registry. It is then used to communicate with the infected computer. As a result of this connection, cybercriminals can get full control of the attacked computer.
The signature for Trojan.MulDrop7.24844 is already in the Dr.Web database, and it is successfully detected and removed by Doctor Web Anti-virus products. Doctor Web security researchers would like to warn Microsoft Windows users to stay vigilant and refrain from opening suspicious files attached to emails.