2015’s virus activity review from Doctor Web
December 29, 2015
Users and security researchers will remember this year due to a wide spread of encryption ransomware for Linux that managed to infect more than 3,000 computers worldwide. Moreover, a large number of new malware programs for Microsoft Windows, the most popular operating system among computer users all around the world, were registered in 2015. Among them are new encoders, backdoors, spyware, and cryptocurrency mining software. Also, the number of new Trojans for OS X have dramatically increased—thus, the leaders among the malware for this platform are adware programs and installers of unwanted applications. The Dr.Web virus databases were updated with new entries for malware targeting Google Android. Judging from the number of known threats, this operation system takes the second place after Microsoft Windows. In 2015, numerous fraudsters continued to develop new schemes of deception. Finally, in the past month, the botnets were still operating. Among the most active of them were those created using the Win32.Rmnet.12 and Win32.Sector file viruses.
Principal Trends Of The Year
- Distribution of a dangerous encryption ransomware for Linux
- Increase in a number of malware for OS X
- Emergence of new malware for Google Android
- Distribution of new malicious programs for Windows
Most remarkable events of 2015
This spring, Doctor Web security researchers examined the BackDoor.Hser.1 Trojan that targeted Russian defense enterprises. The Trojan was spread via mass mailing to private and corporate email addresses of the employees of more than ten domestic enterprises that were members of a famous Russian group of companies. All these enterprises were engaged in defense activities or acted for military industrial complex.
The malicious messages had a Microsoft Excel file that contained an exploit for this program. Thus, the Trojan penetrated an attacked computer. Moreover, upon a command, this malicious program can send a list of active processes that run on the infected computer to the remote server, download and launch any other malicious applications, and also open the command console and execute input/output redirection to a cybercriminals’ server, allowing criminals get control over the infected computer. For more information about BackDoor.Hser.1, refer to the corresponding article.
In June, cybercriminals hacked the Russian Public Opinion Research Center (VTsIOM) website. They uploaded webpages that offered users to download a malicious program under the guise of different harmless files to the VTsIOM’s server.
All the uploaded files contained a malicious program belonging to the Trojan.DownLoader family, the representatives of which were designed to covertly download and install various dangerous applications on a compromised computer. Using this downloader, cybercriminals were able to install a cryptocurrency mining software and other malicious programs. According to the statistics collected by Doctor Web analysts, due to large popularity of the VTsIOM’s website, tens of thousands of users fell victim to this fraudulent scheme.
In August, Doctor Web security researchers detected Trojan.BtcMine.737, a dangerous Trojan intended for cryptocurrency mining using the resources of a compromised computer. Like a network worm, it was able to “travel” a network without user intervention in order to infect all computers connected to it.
This autumn, a spread of Trojan.MWZLesson, that can infect POS terminals, was registered. Apart from its other spy and malicious functions, it was able to save and send bank card information to the command and control server. The researches showed that the Trojan was a modification of BackDoor.Neutrino.50, another malicious program. Aside from being able to operate on POS terminals, BackDoor.Neutrino.50 was capable to steal information stored by the Microsoft Mail client and account details used to get access to resources from a number of well-known FTP clients over the FTP protocol, to execute several DDoS attacks, and to infect local network computers.
In September 2015, virus makers tried to distribute Trojan.PWS.Stealer.13052 via email messages claiming to be from Doctor Web.
Users were offered to take part in testing a non-existent utility called “Dr.Web CureIt 2”, under the guise of which a Trojan penetrated a computer. Doctor Web timely warned users about the incident in the news article.
However, virus makers did not limit their malicious activity to using the name of Dr.Web Anti-virus developers. Soon, they attempted to distribute one more malicious program under the name of another anti-virus software manufacturer.
This Trojan named Trojan.BPLug.1041 was described in the article published by Doctor Web.
Finally, a spread of Linux.Encoder.1, an encryption ransomware that managed to infect more than 3,000 websites located on Linux servers, became one of the most notable events in 2015. This Trojan is far from being the first malware for Linux. In August 2014, Doctor Web announced a new Trojan called Trojan.Encoder.737 that was able to encrypt files stored on Synology NAS servers. However, the distribution area of Linux.Encoder.1 has broken all records.
Virus situation
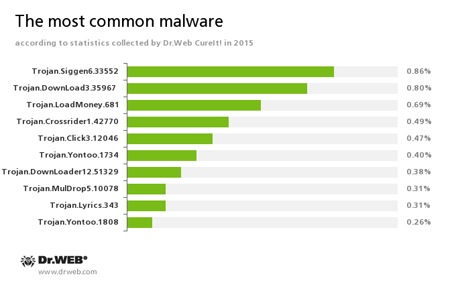
According to statistics collected using Dr.Web CureIt! in 2015, Trojan.Siggen6.33552, a malicious program designed to install another malware on the attacked computer, has become the most frequently detected Trojan. The second place is taken by Trojan.DownLoad3.35967, an downloader capable of downloading and installing unwanted applications. The third place belongs to Trojan.LoadMoney.681—another downloader program. The following diagram shows ten malicious programs most frequently detected by Dr.Web CureIt! in 2015:
Trojan.Crossrider1.42770
Trojans designed to display various advertisements.Trojan.Click
A family of malicious programs designed to generate traffic for various websites by redirecting users to the corresponding webpages.Trojan.Yontoo
These plug-ins for popular browsers display advertisements to users as they browse web pages.Trojan.DownLoader
A family of malicious programs designed to download other malware to the compromised computer.Trojan.MulDrop5.10078
A dropper Trojan designed to unpack other malicious programs and run them on the infected computer.Trojan.Lyrics
A family of Trojans that display annoying advertisements and open dubious webpages without user consent.
The statistics given above shows that, among all malware detected by Dr.Web CureIt! in 2015, adware, installers of unwanted applications, and downloader programs have a dominant position.
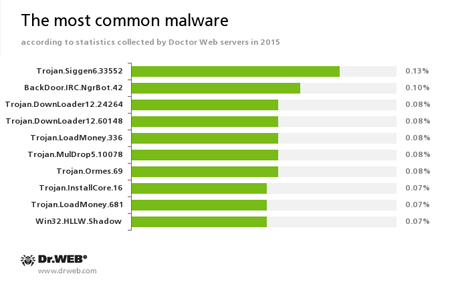
We can see a suchlike situation judging from the Doctor Web statistics servers collected during the year. The leader here is an installer of unwanted applications called Trojan.Siggen6.33552. The second place belongs to BackDoor.IRC.NgrBot.42 which is known to information security researchers since 2011. Malicious programs of this family are able to execute intruder-issued commands on infected machine controlled by cybercriminals via the IRC (Internet Relay Chat) text-messaging protocol. Also, among the leaders in detection frequency, downloader programs belonging to the Trojan.Downloader family can be mentioned. Below, we can see ten most frequently detected malicious programs, according to the Doctor Web statistics servers:
Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on the victim's computer.Trojan.Ormes.69
A Trojan that displays annoying ads in the browser.Trojan.InstallCore.16
A Trojan that installs adware and unwanted programs, also known as Trojan.Packed.24524.Win32.HLLW.Shadow
A network worm that can also use vulnerabilities in Microsoft Windows for its spreading. The worm is known under the names of Conficker and Kido.
The statistics displays that virus makers are still interested in concocting installers of unwanted applications and adware since they are probably the most profitable types of malware. The same tendency was in 2014.
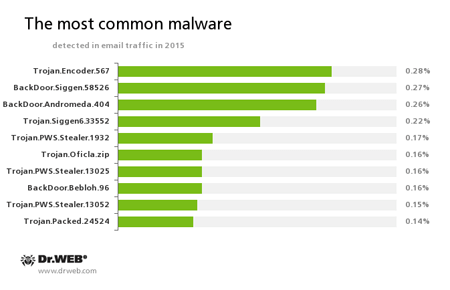
Among malicious attachments distributed via email messages, the leader of 2015 is a dangerous encryption ransomware called Trojan.Encoder.567. It encrypts files and demands a ransom for decryption of compromised data. Trojan.Encoder.567 can encrypt important user files, for example, of the following types: .jpg, .jpeg, .doc, .docx, .xls, xlsx, .dbf, .1cd, .psd, .dwg, .xml, .zip, .rar, .db3, .pdf, .rtf, .7z, .kwm, .arj, .xlsm, .key, .cer, .accdb, .odt, .ppt, .mdb, .dt, .gsf, .ppsx, .pptx.
BackDoor.Siggen.58526 takes the second place. This Trojan can download malicious programs and run them on a infected computer without user knowledge and execute the commands received from cybercriminals. The third place belongs to BackDoor.Andromeda.404, a downloader Trojan designed to download other malicious programs from the remote servers and launch them on a compromised machine. Ten malware applications frequently detected by Dr.Web anti-virus software in email traffic during all the year are represented in the diagram below:
Apart from the abovementioned Trojans, the following malware programs were detected among email messages in 2015:
Trojan.PWS.Stealer
A family of Trojans designed to steal passwords and other confidential information stored on the infected computer.Trojan.Oficla
A family of Trojans mainly distributed via email messages. Once one of these Trojans infects a system, it hides its further activity. Trojan.Oficla connects the computer to a botnet, which allows cybercriminals to upload other malicious software to the compromised machine. After the system gets infected, cybercriminals that run the botnet get control over the victim’s computer. In particular, they become able to upload, install, and use any malicious software they choose.BackDoor.Bebloh.96
A malicious program belonging to the family of banking Trojans. This application poses a threat to users of e-banking services (RBS), because it allows cybercriminals to steal confidential information by intercepting data submitted through forms in the browser window and by embedding the malicious code into bank webpages.Trojan.Packed.24524
A Trojan that installs adware and unwanted applications, also known as Trojan.InstallCore.16.
We can conclude that, in 2015, in addition to downloader Trojans, virus makers that distribute malware via email messages became more interested in developing encryption ransomware and backdoors capable of stealing passwords and other confidential data from infected computers.
Botnets
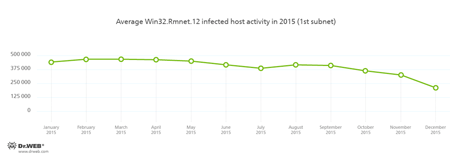
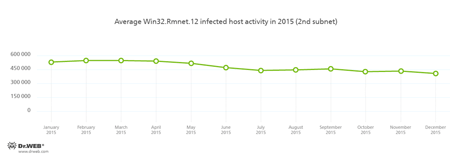
Throughout the whole year, Doctor Web security researchers have been keeping a close watch on several botnets activity created by cybercriminals using different malware. At that, activity of the Win32.Rmnet.12 botnet was gradually decreasing during the year. This dangerous virus consists of several modules and can embed content into loaded webpages, redirect users to the specified websites, and send data entered by a user to the remote servers. Besides, Win32.Rmnet.12 can steal passwords stored by popular FTP clients and execute various commands from cybercriminals. It is also able to replicate itself infecting executable files. Moreover, the virus can spread with the help of scripts written in VBScript and embedded into webpages. Activity of two subnets of the Win32.Rmnet.12 botnet is shown in the graphs below:
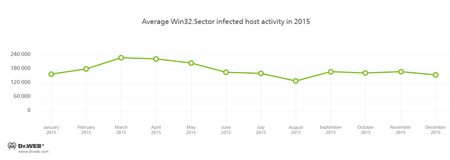
Another file virus, Win32.Sector, has been known to security researchers since 2008. Its purpose is to download executable files from a P2P network and run them on a compromised computer. The virus can plant itself into running processes and spread itself infecting files stored on local disks, removable media, and in shared folders. At the beginning of the year, activity of this botnet increased a little. However, by autumn, the tendency to its decrease was registered:
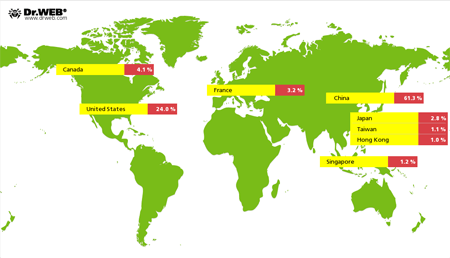
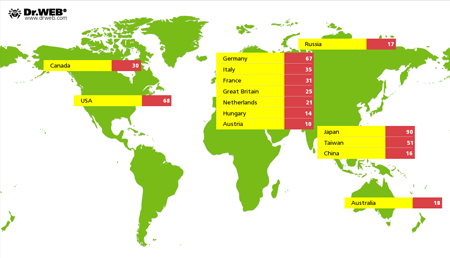
During 2015, Doctor Web specialists continued to monitor activity of Linux.BackDoor.Gates.5. This Trojan can execute DDoS attacks on different websites. In total, cybercriminals attempted 31,880 such attacks. The majority of targeted websites (that is more than 61%) were located in China. The United States took the second place; and Canada, the third. The following picture represents the geography of DDoS attacks organized using Linux.BackDoor.Gates.5 in 2015:
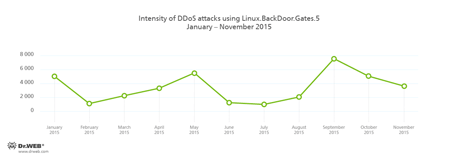
Periodically, the number of DDoS attacks varied, and, by December, they came to nothing at all. You can see intensity of DDoS attacks using Linux.BackDoor.Gates.5 (judging by the number of unique IP addresses) from January to November 2015 in the graph below:
Encryption ransomware
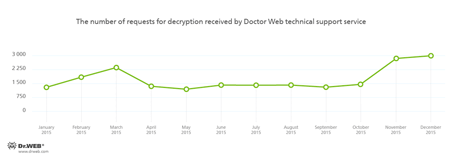
Like in 2014, encryption ransomware posed a serious threat to users. They are rightfully considered the most dangerous malware family. If a year ago the average number of requests received by Doctor Web technical support from users of compromised devices was about 1,000, by the end of 2015, it increased almost threefold:
The most common ransomware programs in 2015
- Trojan.Encoder.567
- Trojan.Encoder.858
- BAT.Encoder
- Trojan.Encoder.741
- Trojan.Encoder.761
- Trojan.Encoder.556
- Trojan.Encoder.398
- Trojan.Encoder.2843
- Trojan.Encoder.888
- Trojan.Encoder.263
To avoid losing important files, follow the guidance below:
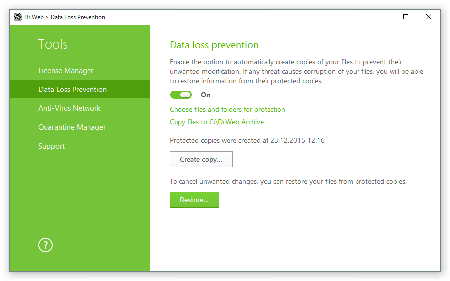
- Make sure that Preventive Protection is turned on in the Dr.Web Security Space settings (v9, 10, and 11). It can save your computer from threats unknown to the Dr.Web virus database.
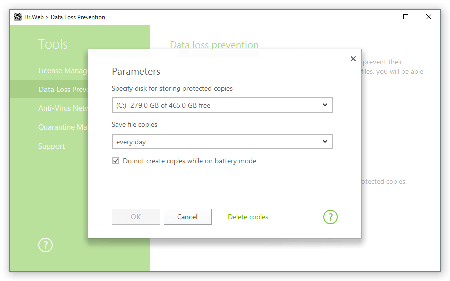
- Then turn on “Data loss prevention” in the Tools section and configure store parameters for backup copies of important files.
- Create a backup copy of critical data and configure its automatic saving choosing a suitable time period.
These actions along with your carefulness will guard your computer from the majority of existing threats including encryption ransomware.
Linux
The most remarkable event in terms of Linux information security is a spread of an encryption ransomware called Linux.Encoder.1. The Trojan penetrated Linux web servers using vulnerabilities in popular content management systems (CMS) and infected more than 3,000 websites by November 24.
Using an unknown vulnerability, cybercriminals injected a shell script that helped execute various commands from the remote server. The dropper of Linux.Encoder.1, that was uploaded to the compromised server, identified the operating system architecture (32-bit or 64-bit), extracted from the body a corresponding sample of encryption ransomware, ran it, and then initiated its own removal. It should be noted that the Trojan successfully operated with web server privileges. In other words, it did not need to get root privileges. For more information about this Trojan, refer to the article.
Soon after this incident, Doctor Web security researchers registered several earlier modifications of this ransomware. One of them was named Linux.Encoder.2. You can read about the features and distinctions of the Linux.Encoder.1’s counterpart in the review published by Doctor Web.
However, attacks on Linux web servers were already registered this spring. Linux.BackDoor.Sessox.1, a Trojan detected in April, received IRC (Internet Relay Chat) commands and was able to attack a specified Internet server by sending repeated GET requests. Linux.BackDoor.Sessox.1 also scanned the attacked server for the ShellShock vulnerability that allows to execute an arbitrary code. For more information about this Trojan, refer to the news article.
In 2015, Doctor Web security researchers detected a number of backdoor Trojans for Linux. One of them was described in February. The scheme of the Trojan’s distribution was typical: cybercriminals hacked passwords for user accounts to access the system over SSH and installed Linux.BackDoor.Xnote.1. It has also a standard purpose—execution of the cybercriminal’s commands. Besides, Linux.BackDoor.Xnote.1 can run a shell with the specified environment variables and grant the command and control server access to this shell. It also can start a SOCKS proxy on the infected machine or start its own implementation of the portmap server.
Linux.BackDoor.Dklkt.1, another backdoor for Linux, was detected in July. The purpose of this Trojan was to execute several types of DDoS attacks. In August, Doctor Web analysts discovered a big number of malware programs capable of infecting Linux routers. In total, 1,439 devices are known to be infected with the mentioned malicious programs; at that, in 649 cases, geographical location of infected devices was determined—the majority of incidents took place in Japan. Users in Germany, the USA, and Taiwan also suffered from such attacks.
In September, Doctor Web published an article about Linux.Ellipsis.1 that was notable for its “paranoid” behavior. It was designed to create a proxy server on the attacked computer. The server was used to provide its anonymity in order to access devices hacked by another malware program—Linux.Ellipsis.2. Judging by some of its features, it is a creation of the same virus writer and is designed to brute-force passwords.
All in all, we can say that cybercriminals’ interest in Linux systems is gradually growing—so, in future, emergence of new malware for this platform is very possible.
OS X
Virus makers become more and more interested in targeting Apple users. The majority of threats for Apple computers detected in 2015 are adware Trojans and installers of unwanted applications. The exception is a new modification of the Mac.BackDoor.OpinionSpy Trojan detected at the beginning of the year that has been known to information security experts since 2010.
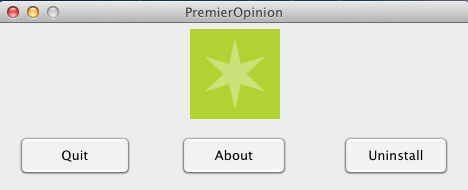
Despite the fact that developers of this application label it as a utility to carry out marketing investigations, Mac.BackDoor.OpinionSpy is a full-blown spyware Trojan. It tracks the user’s activity and transmits to the command and control server all the information about visited sites, opened tabs, and followed links. It also monitors the traffic transmitted through the network card of the Apple computer including traffic of the instant messaging clients (such as Microsoft Messenger, Yahoo! Messenger, AIM, iChat). Read more about this backdoor in the article published by Doctor Web.
Among the most frequently detected installers of unwanted applications for OS X, we should mention Adware.Mac.InstallCore.1 discovered by Doctor Web security researchers in May 2015. It was able to download and install malicious plugins for Safari, Firefox, and Chrome. These extensions were detected as Trojans belonging to the Trojan.Crossrider family. Another installer, Adware.Mac.WeDownload.1, was described in September. It spread by means of an affiliate program focused on generating income from file downloads, like its counterpart, Adware.Mac.Tuguu.1, examined by Doctor Web analysts in December 2015.
Judging by the fact that suchlike programs are frequently detected in the wild, it is hardly possible that new samples of these malicious applications do not emerge.
Dangerous and non-recommended sites
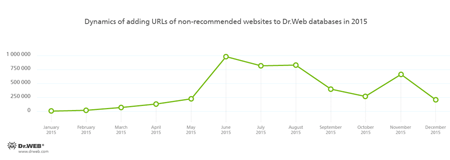
There are a huge number of Internet resources non-recommended for minors that can also harm your computer. Dr.Web SpIDer Gate and Parental Control, the databases of which are regularly updated with new links to malicious and non-recommended websites, will help you withstand such Internet resources. The dynamics of this process is shown in the following diagram:
Non-recommended websitesNetwork frauds
Fraudsters that try to make a profit on careless and unexperienced Internet users’ are still active. In 2015, Doctor Web announced an increase in the number of network frauds using fake car dealers websites. To attract the potential victim’s attention, cybercriminals send bulk SMS messages with the text informing the recipient that they have won a car.
Besides, such websites contain a separate page with description of the “promo” conditions, according to which a participant that has “won” a car is asked to pay 1% of the car’s value in tax via a payment terminal or to purchase the MTPL insurance. Thus, the main cybercriminals’ purpose is fulfilled: after transferring the payment, the victim will get neither the money back not their prize.
Numerous online stores selling some strange items or goods of questionable quality continue to prosper. They have been already described in news articles by Doctor Web in 2015. It is no doubt that new dubious online stores will still appear on the Internet.
Mobile devices
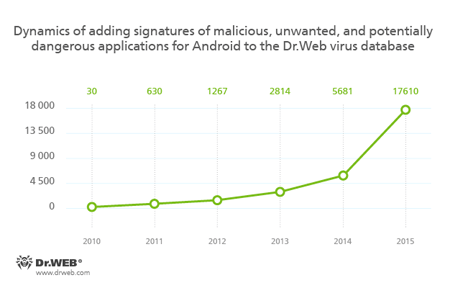
In the past year, virus makers were still showing their interest in mobile devices users. As expected, one of the main cybercriminals’ targets in 2015 were users of Android smartphones and tablets. For the last year, Doctor Web security researchers detected a huge number of malicious, unwanted, and potentially dangerous Android applications. As a result, the Dr.Web virus database was updated with 11,929 new entries and expanded by 210%.
The majority of malware for Android devices is still represented by SMS Trojans. According to the Dr.Web virus databases, the quantity of signatures for the Android.SmsSend family increased by 164.2% and amounted to 7,103 entries. The number of signatures for the Android.SmsBot (+192.8%) family also increased. In total, it is obvious that malicious applications sending messages to premium numbers and subscribing users to chargeable services without their knowledge or consent are still one of the main dangers for Android devices users.
Moreover, different banking Trojans for Android posed a serious threat to users in 2015. This malware can steal logins and passwords to access online banking applications and covertly transfer money to cybercriminals’ bank accounts. Doctor Web specialists detected a big number of such Trojans this year. At that, among them not only the representatives of the well-known families such as Android.Banker and Android.BankBot were registered but also new malware programs of this type were discovered—the Android.ZBot banking Trojans, in particular.
It should be noted that attacks using banking Trojans for Android are popular among virus makers all over the world. In 2015, such Trojans were widely used against Russians and South Koreans. For example, Android.BankBot.65.origin, a dangerous malware program designed to steal money from Russian users, was incorporated in a legitimate online banking application and spread masquerading as an update for the corresponding software on a popular website dedicated to mobile devices. For more details about Android.BankBot.65.origin, refer to the corresponding news article.
However, in most cases, banking Trojans spread as independent malicious applications with the help of sending bulk SMS messages containing a link to download some banker Trojan. In 2015, Russian users often received “notifications” on incoming MMS messages, but, for example, in South Korea, users were offered to visit a wedding, track postal items, and even get familiar with some criminal case file.
Also, this year, new ransomware Trojans continued to appear. These malicious programs became notorious in the middle of 2014 and have posed a serious threat to Android devices users since then. Such programs usually lock compromised mobile devices and demand a ransom to unlock them. Nevertheless, there are more dangerous modifications of suchlike ransomware. For example, Android.Locker.71.origin, a Trojan detected in February 2015. It was designed to encrypt all accessible files and demanded a $200 ransom.
The number of entries for ransomware of the Android.Locker family in the Dr.Web virus database
| 2014 | 2015 | Dynamics |
|---|---|---|
| 137 | 965 | +604.4% |
The outgoing year was also marked with new Trojans that were distributed through Android firmware or even pre-installed on mobile devices. One of such programs was detected in January and was named Android.CaPson.1. This Trojan was able to send and intercept SMS messages, open webpages, transmit information about a compromised device to the remote server, and download other programs. In September, Doctor Web specialists detected Android.Backdoor.114.origin, a Trojan that was pre-installed on a popular tablet. It was able to covertly download, install, and remove programs upon a command from cybercriminals. Already in October 2015, a pre-installed Android.Cooee.1 Trojan was detected on several mobile devices. It was incorporated in a launching application (Android graphical shell) and was designed for showing advertisements. Moreover, it was able to download and run not only additional advertising packages but also other applications, including malicious ones.
Malware attempting to get root privileges on Android devices posed yet another threat to their owners in 2015. For example, in April, Doctor Web security researchers detected Trojans belonging to the Android.Toorch family. They spread via Chinese popular websites with downloadable software. Furthermore, the malware could be downloaded to mobile devices with the help of numerous aggressive advertising modules embedded into different applications. If Trojans succeeded in getting root privileges, they could download, install, and remove specified programs without user knowledge. Later, Android.Backdoor.176.origin and its modification—Android.Backdoor.196.origin—were discovered. These malicious programs tried to get root privileges using a modified version of the Root Master utility. They were mainly designed to covertly install and remove applications upon cybercriminals’ command. Other suchlike Trojans were detected in 2015. Among them are Android.Backdoor.273.origin, that spread via Google Play, and Android.DownLoader.244.origin, that could be downloaded from popular websites with downloadable software by potential victims. Both of them were intended to stealthily download and install other malicious programs. Thus, 2015 was the year of a dramatic growth of different types of Trojans whose main purpose was to download and install software without user knowledge.
In 2015, virus makers again paid attention to the Google Play applications. Particularly, such Trojans as Android.Spy.134 and Android.Spy.135 displayed fake Facebook authorization form prompting users to enter their login and password details into that form. Then the malware forwarded the divulged data to the remote server. In total, these Trojans had been already downloaded more than 500,000 times.
Also, Doctor Web security researchers detected Android.DownLoader.171.origin in one of the Google Play applications. This Trojan was downloaded more than 100,000 times. It was also distributed through popular websites with downloadable software—thus, total number of downloads exceeded 1,500,000. Android.DownLoader.171.origin was designed to download and install various applications. For more information about this Trojan, refer to the article.
In September 2015, Android.MKcap.1.origin was detected. Cybercriminals employed it to automatically subscribe users to various chargeable services. Later this month, Android.MulDrop.67 was discovered. Its main purpose was to display advertisements and download and install other Trojans.
In October, the Android.PWS.3 Trojan was detected on Google Play. It was disguised as a benign audio player. It prompted the potential victim to log in to popular social network account. Once the user entered their login and password, the Trojan forwarded that information to cybercriminals.
Another threat posed to users of Android devices in 2015 was activity of various aggressive advertising modules incorporated into different software. In comparison with 2014, this year, the number of signatures for them in the Dr.Web virus database increased by 266% and amounted to 290 entities.
At that, in January, applications with the Adware.HideIcon.1.origin advertising plugin were found in Google Play. This unwanted module displayed update notifications in the status bar of mobile devices, imitated the process of downloading important “files” which, once opened, redirected a user to different websites. Moreover, at launching other applications, Adware.HideIcon.1.origin was able to display full screen advertisements.
In February, the Adware.MobiDash.1.origin advertising module incorporated in Google Play applications was detected. In total, these applications were downloaded about dozens of millions of times. Later, Adware.HiddenAds.1, yet another advertising module, was registered. It was installed on mobile devices by a malicious application, operated without user knowledge, and was able to display various advertisements in the status bar. Another advertising module— Adware.Adstoken.1.origin—spread via malicious programs, showed advertisements, displayed messages in the status bar, and was able to open webpages with ads in a browser. At the end of the year, Doctor Web security researchers detected adware called Adware.AnonyPlayer.1.origin. This unwanted module showed advertisements on top of majority of launched applications.
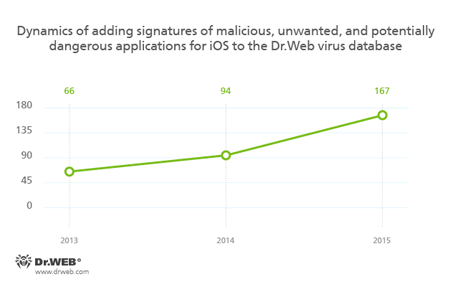
Still popular myth that Apple mobile devices are not subject to cybercriminals’ attacks will soon be dispelled. Year by year, more and more Trojans for iOS appears. Thus, if in 2014 the Dr.Web virus database contained 94 signatures for iOS malware, in 2015 their number grew by 77% and amounted to 167 entries.
One of the malware for iOS detected in 2015 is IPhoneOS.BackDoor.KeyRaider, a malicious program distributed in modified applications compromising jailbroken Apple devices. IPhoneOS.BackDoor.KeyRaider stole confidential data from infected gadgets and transmitted it to the server. In September, a new Trojan—IPhoneOS.Trojan.XcodeGhost—was detected in App Store. Its main purpose was to display fake dialogs in order to carry out phishing attacks, and automatically open links specified by virus makers. In November, Doctor Web specialists discovered its modification with the same functions that was named IPhoneOS.Trojan.XcodeGhost.8. In October, IPhoneOS.Trojan.YiSpecter.2 was detected. It was downloaded from different websites and could be installed on smartphones and tablets with or even without jailbreak. IPhoneOS.Trojan.YiSpecter.2 installed additional malicious modules, was able to display advertisements, and, upon cybercriminals’ command, remove applications and replace them with their fake versions.
In the end of the year, the IPhoneOS.Trojan.TinyV Trojan was detected. It spread in modified applications and infected jailbroken iOS devices. Upon a command from the server, IPhoneOS.Trojan.TinyV could covertly download and install software and modify the hosts file. As a result, users could be redirected to non-recommended websites. In addition to this, among malicious programs detected this year is Adware.Muda.1, an adware that infected jailbroken Apple devices. It displayed advertisements on top of launched applications and in the status bar. It also downloaded software without user knowledge.
Prospects and possible trends
Having analyzed the current information security situation, we suppose that a constant growth of malicious programs for Linux and iOS will not decrease in 2016. It is possible that their features will be extended—thus, apart from adware and installers of unwanted applications, Apple users may encounter the first encoders for OS X.
New malware for Android will still appear. At that, banking Trojans will surely be the main part of it. Users of Apple mobile devices should also be on their guard since, during 2015, several Trojans for iOS were detected; and there is every reason to believe that this tendency remains in 2016.
New botnets created by means of malicious programs not only for Windows but also for other platforms are very likely to appear. Finally, it is possible that new methods of network frauds (probably with usage of mobile devices) will emerge. Cybercriminals may improve their methods of stealing users’ personal and confidential information.
However, there is no doubt that Doctor Web specialists will be keeping a close watch on the information security situation in 2016 and will still timely inform our users about new threats.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live
[% END %]