December 23, 2022
Over the course of last month, Doctor Web’s malware analysts discovered many new malicious applications on Google Play. Among them were dozens of fake apps that cyber criminals use in various fraudulent schemes, as well as trojans that subscribe victims to paid services.
PRINCIPAL TRENDS IN NOVEMBER
- A decrease in the activity of malicious and unwanted apps that display ads
- Increased spyware activity
- The discovery of new threats on Google Play
According to statistics collected by Dr.Web for Android
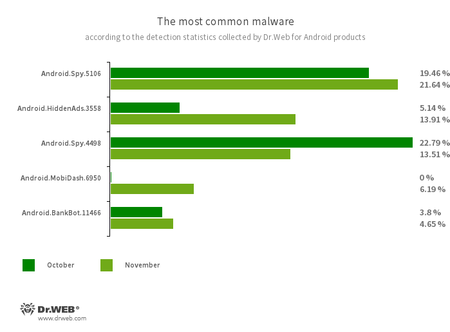
- Android.Spy.5106
- Android.Spy.4498
- The detection name for various modifications of the trojan that steals the contents of other apps’ notifications. In addition, it can download apps and prompt users to install them, and it can also display various dialog boxes.
- Android.HiddenAds.3558
- A trojan designed to display intrusive ads. Trojans of this family are often distributed as popular and harmless applications. In some cases, other malware can install them in the system directory. When these infect Android devices, they typically conceal their presence from the user. For example, they “hide” their icons from the home screen menu.
- Android.MobiDash.6950
- A trojan that displays obnoxious ads. It is a special software module that developers incorporate into applications.
- Android.BankBot.11466
- The detection name for malicious applications protected with an ApkProtector software packer. Among them are banking trojans, spyware, and other malicious software.
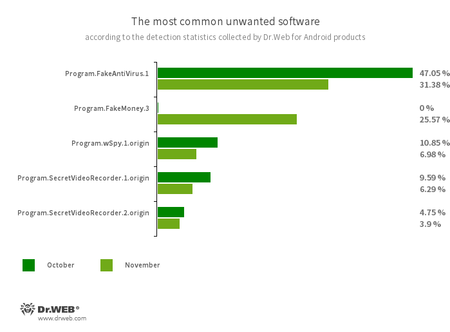
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of nonexistent threats, mislead them, and demand that they purchase the software’s full version.
- Program.FakeMoney.3
- The detection name for an Android application that allegedly allows users to earn money by watching video clips and ads. This app makes it look as if rewards are accruing for completed tasks. To withdraw their “earnings”, users allegedly have to collect a certain sum. But even if they succeed, in reality they cannot get any real payments.
- Program.wSpy.1.origin
- A commercial spyware app designed to covertly monitor Android device user activity. It allows intruders to read SMS and chats in popular messaging software, listen to the surroundings, track device location and browser history, gain access to a phonebook and contacts, photos and videos, and take screenshots and pictures through a device’s built-in camera. In addition, it has keylogger functionality.
- Program.SecretVideoRecorder.1.origin
- Program.SecretVideoRecorder.2.origin
- The detection name for various modifications of an application that is designed to record videos and take photos in the background using built-in Android device cameras. It can operate covertly by allowing notifications about ongoing recordings to be disabled. It also allows an app’s icon and name to be replaced with fake ones. This functionality makes this software potentially dangerous.
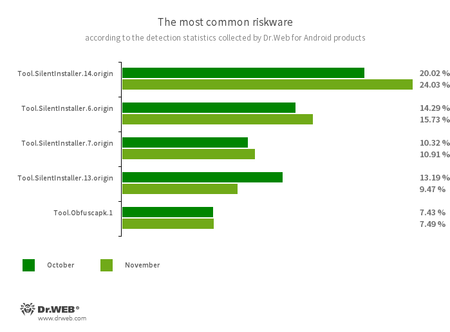
- Tool.SilentInstaller.14.origin
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.7.origin
- Tool.SilentInstaller.13.origin
- Riskware platforms that allow applications to launch APK files without installing them. They create a virtual runtime environment that does not affect the main operating system.
- Tool.Obfuscapk.1
- The detection name for applications protected by the Obfuscapk obfuscation tool. This tool is used to automatically modify and scramble the source code of Android apps to make reverse engineering more difficult. Cybercriminals use this tool to protect malicious applications from being detected by anti-virus programs.
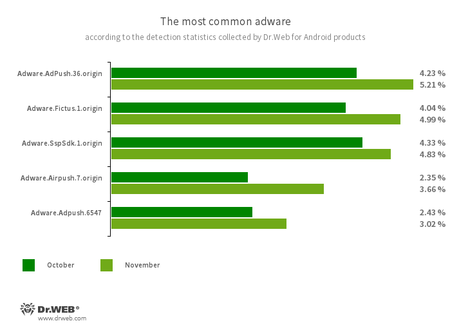
Program modules incorporated into Android applications. These are designed to display obnoxious ads on Android devices. Depending on the family and modification involved, they can display full-screen ads and block other apps’ windows, show various notifications, create shortcuts, and load websites.
- Adware.AdPush.36.origin
- Adware.Adpush.6547
- Adware.Fictus.1.origin
- Adware.SspSdk.1.origin
- Adware.Airpush.7.origin
Threats on Google Play
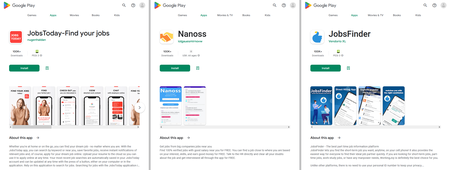
In November, Doctor Web’s malware analysts discovered over 80 new malicious apps on Google Play. Among them were many trojans from the Android.FakeApp family, which cyber criminals used in a variety of scams. For instance, trojans like Android.FakeApp.1036, Android.FakeApp.1039, Android.FakeApp.1041, Android.FakeApp.1045, Android.FakeApp.1046, Android.FakeApp.1047, and Android.FakeApp.1055 were distributed under the guise of job-search software. In reality, though, they only loaded websites with fake vacancies.
When users tried to apply for a job announcement they liked, they were asked to provide their personal information, including their first and last names, email address, and mobile phone number. This data would then end up in the cybercriminals’ hands. In some cases, potential victims of the fraudsters were asked to contact “the employer” directly, using WhatsApp or Telegram messengers. Posing as representatives of various companies, scammers invited users to join dubious online money-making services and then tried to swindle money from them. Read more on this case in special news material on our website.
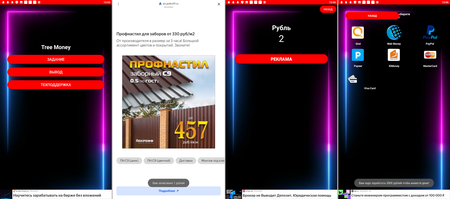
Other trojans allegedly allowed users to make money by watching ads. Dubbed Android.FakeApp.1081, Android.FakeApp.1082, Android.FakeApp.1083, and Android.FakeApp.1084, these malicious apps loaded advertising video clips and banners. For each successfully completed view of a full-screen ad, users “received” a reward of 1 ruble. However, when they tried to withdraw the money, these applications informed them that they needed to collect a much larger sum—up to several thousand rubles. In this case, the authors of these fake apps deceived the victims to make them watch as many ads as possible and, thus, generate more income for the fraudsters. At the same time, in order to increase the volume of ad traffic even more, some modifications of these trojans had a “reference” or “help” information section in which it was stated that if a user clicks on ads, the reward would allegedly increase to 2 rubles. In reality, users did not receive any rewards at all and only wasted their time.
These malicious applications were targeted toward Russian-speaking users. However, their creators made many grammatical and lexical mistakes. Among them were mistakes in the apps’ names, like “Заработка без вложений” (Zarabotka bez vlozheniy—“To earning without investment”), “Заработка денег с Одной клик” (Zarabotka deneg s Odnoy klik—“To earning money with One of click”). Also mistakes were made in the texts of the apps’ interface, like “Порог начисление деньги это 2000 рублей” (Porog nachislenie dengi eto 2000 rublei—“2000 rubles is a minimum accrual money”), “Вам зачисленно 1 рублей” (Vam zachislenno 1 rublei—“You have been creditted 1 rubles”), and “Вам надо заработать 3000 рублей чтобы вывести денег” (Vam nado zarabotat 3000 rublei chtobi vivesti deneg—“You have to earn 3000 rubles to withdraw some money”).
Our specialists uncovered over 20 modifications of these trojan apps.
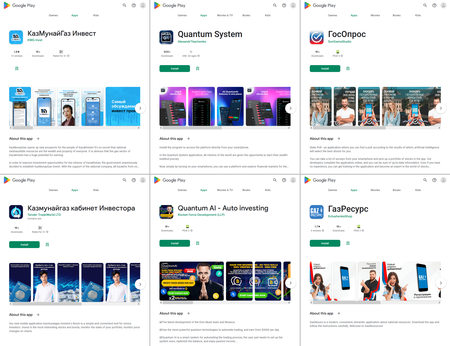
Among the fake apps discovered were the usual trojans that allegedly allow money to made through various investments, such as cryptocurrencies and the stock market, and also by trading in oil and natural gas. They were distributed under the guise of different instruments, like directories or trading apps, and were targeted toward users from a variety of countries, including Russia and Kazakhstan. These fakes loaded fraudulent websites, misleading potential victims.
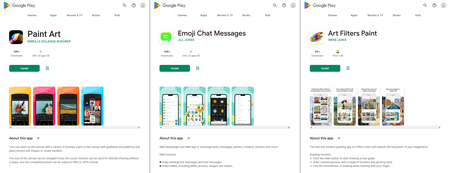
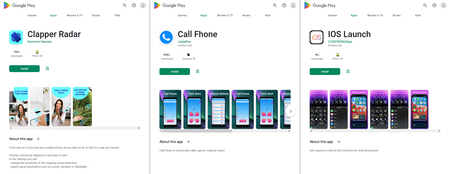
Apart from them, Doctor Web’s specialists uncovered other trojan apps that subscribe victims to paid services. They were added to the Dr.Web anti-virus base as Android.Joker.1917, Android.Joker.1920, and Android.Joker.1921, and also as Android.Subscription.13, Android.Subscription.14, and Android.Subscription.15. The first three were disguised as the Paint Art, Emoji Chat Messages, and Art Filters Paint apps. The latter three were hiding in the Call Fhone, IOS Launch, and Clapper Radar apps.
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web anti-virus products for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products