Doctor Web’s September 2022 review of virus activity on mobile devices
October 31, 2022
Malicious actors once again widely deployed specialized software tools that allow apps to be launched with no installation required. In addition, users continued to encounter various spying and monitoring software.
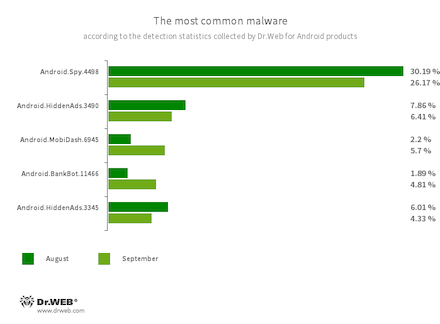
The Android.Spy.4498 trojan, which steals information from other apps’ notifications, was detected 32.72% less frequently compared to August. Last month, it accounted for just over a quarter of all malware detections.
During September, Doctor Web's specialists discovered other threats on Google Play. Among them were fake apps used in various fraudulent schemes, and adware.
PRINCIPAL TRENDS IN SEPTEMBER
- A decline in Android.Spy.4498 trojan activity
- A decrease in adware trojan activity
- An increase in the number of apps detected that have built-in, unwanted adware modules
- The emergence of other threats on Google Play
According to statistics collected by Dr.Web for Android
- Android.Spy.4498
- A trojan that steals the contents of other apps’ notifications. In addition, it can download apps and prompt users to install them, and it can also display various dialog boxes.
- Android.HiddenAds.3490
- Android.HiddenAds.3345
- Trojans designed to display intrusive ads. Trojans of this family are often distributed as popular and harmless applications. In some cases, other malware can install them in the system directory. When these trojans infect Android devices, they typically conceal their presence from the user. For example, they “hide” their icons from the home screen menu.
- Android.BankBot.11466
- The detection name for malware protected by the ApkProtector packer. Such malware includes banking trojans, spyware trojans, and other threats.
- Android.MobiDash.6945
- A trojan that displays obnoxious ads. It is a special software module that developers incorporate into applications.
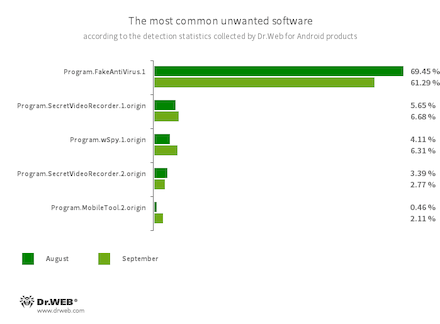
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of nonexistent threats, mislead them, and demand that they purchase the software’s full version.
- Program.SecretVideoRecorder.1.origin
- Program.SecretVideoRecorder.2.origin
- The detection name for various modifications of an application that is designed to record videos and take photos in the background using built-in Android device cameras. It can operate covertly by allowing notifications about ongoing recordings to be disabled. It also allows an app’s icon and name to be replaced with fake ones. This functionality makes this software potentially dangerous.
- Program.wSpy.1.origin
- Program.MobileTool.2.origin
- These are the apps that make it possible to spy on Android device owners and can be used for cyber espionage. Depending on their version and modification, they are capable of executing various actions. For example, they can track device location, read SMS and social media conversations, copy documents, photos and videos, snoop on phone calls, listen to the surroundings, etc.
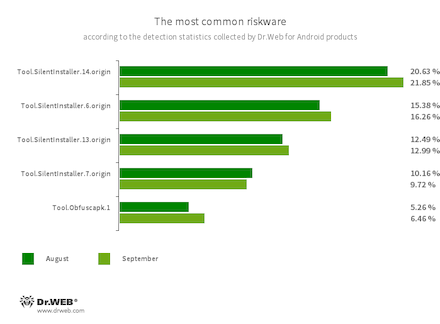
- Tool.SilentInstaller.14.origin
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.13.origin
- Tool.SilentInstaller.7.origin
- Riskware platforms that allow applications to launch APK files without installing them. They create a virtual runtime environment that does not affect the main operating system.
- Tool.Obfuscapk.1
- The detection name for applications protected by the Obfuscapk obfuscation tool. This tool is used to automatically modify and scramble the source code of Android apps to make reverse engineering more difficult. Cybercriminals use this tool to protect malicious applications from being detected by anti-virus programs.
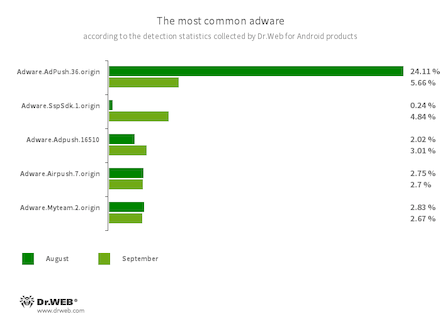
Program modules incorporated into Android applications. These are designed to display obnoxious ads on Android devices. Depending on the family and modification involved, they can display full-screen ads and block other apps’ windows, show various notifications, create shortcuts, and load websites.
- Adware.AdPush.36.origin
- Adware.Adpush.16510
- Adware.SspSdk.1.origin
- Adware.Airpush.7.origin
- Adware.Myteam.2.origin
Threats on Google Play
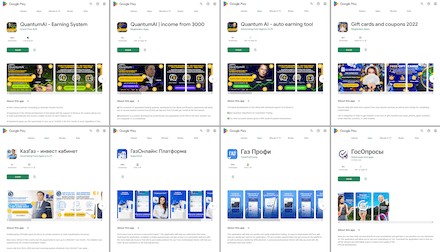
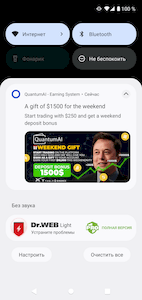
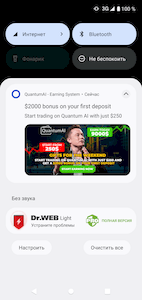
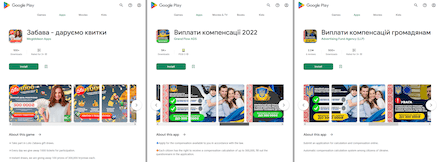
In September, new fake applications were uncovered on Google Play. The functionality of these apps did not match the declared one. With the help of these fakes, malicious actors executed various fraudulent schemes and targeted users from different countries. For instance, the Android.FakeApp.1005, Android.FakeApp.1007, Android.FakeApp.1011, and Android.FakeApp.1012 trojan apps were distributed under the guise of software that could allegedly help users improve their financial literacy, invest in oil and gas projects, and gain access to special automatic trading systems and online income-generating services. Among them were apps called “QuantumAI | income from 3000”, “QuantumAI - Earning System”, “Quantum AI - auto earning tool”, “КазГаз - инвест кабинет” (KazGaz - invest cabinet), “ГосОпросы” (GosOprosy), “ГазОнлайн: Платформа” (GazOnlain: Platforma), “Газ Профи” (Gaz Profi), and “Gift cards and coupons 2022”.
Some of them targeted Russian users, while others targeted Russian-speaking users in Kazakhstan and European Union countries. The trojans loaded fraudulent websites where potential victims were offered the opportunity to create an account to “access” a particular service. To do so, users had to provide their personal data: their first and last names, email address, and mobile phone number. In some cases, they were also asked to enter a one-time code sent to their phone via SMS. When “registration” was complete, users either were redirected to another dubious website or saw a message stating that the operation was completed successfully and that a “manager” or an “expert” would contact them soon. With that, the information provided by victims was sent to an unknown third-party which could then use it at their own discretion. This could include executing future phishing attacks, or selling it to advertising and marketing agencies or on the black market.
Below are examples of such fake applications:
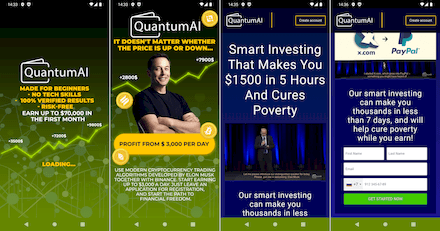
At the same time, to attract users’ attention, some of these trojans would periodically display notifications with fake messages. For example, messages with promises of substantial earnings as well as bonuses and gifts for customers; or with warnings about the allegedly limited number of available spots for users to register.
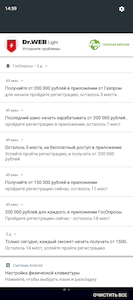
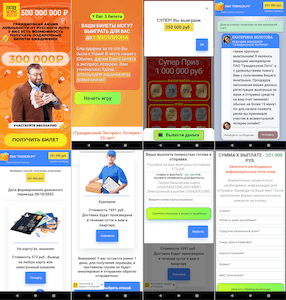
In order to reach a larger audience, cybercriminals advertised these trojans in third-party apps through the advertising systems built into them. With that, such an advertisement in the form of full-screen banners and videos could in some cases be targeted. For example, it could target Russian-speaking users in European Union countries with a proposal to install an app that would allegedly allow them to obtain free shares of a large Russian company from the oil and gas sector.
Below are examples of ads that helped scammers spread the fake apps:
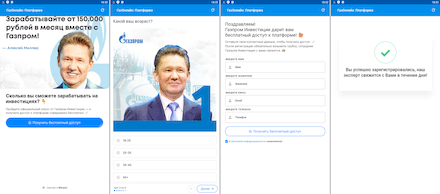
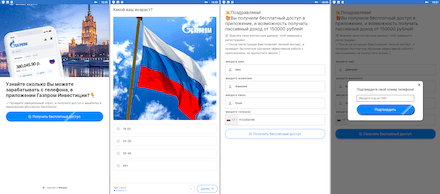
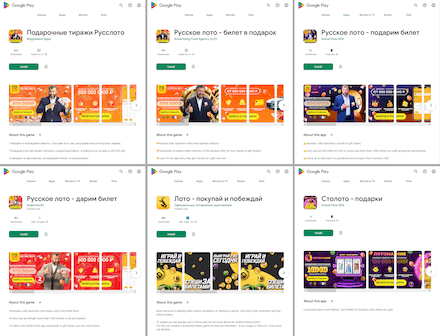
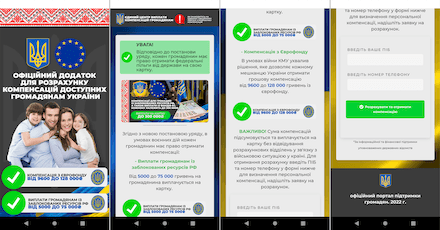
The Android.FakeApp.1006, Android.FakeApp.1008, Android.FakeApp.1009, Android.FakeApp.1010, Android.FakeApp.1019 trojans, as well as some modifications of the Android.FakeApp.1007 trojan, were distributed among Russian and Ukrainian Android users. With the help of these apps, users could allegedly receive free lottery tickets to take part in draws, or find information on government financial support and apply for it.
In reality, the trojans loaded fraudulent websites containing false information. They simulated both lottery draws and the process of searching and applying for social benefits. To “receive” the prizes and the government support, potential victims had to provide their personal data. Moreover, they were also asked to pay a commission or a fee for the money “transfer” or for courier “delivery”. Information provided by users, including bank card details, and the payment fell into the hand of the attackers, while the victims themselves did not receive any of the promised government support or the lottery prizes.
Examples of how these trojan applications operate are provided below:
Our specialists also discovered new unwanted adware modules. Dubbed Adware.AdNoty.1 and Adware.AdNoty.2 in accordance with Doctor Web classification, these modules can be integrated into a variety of software. They periodically display notifications with ads, for example, that promote games and apps. When the user taps such notifications, various websites are loaded in the browser of Android devices. These websites are loaded in accordance with a list of advertising URLs, which is defined by the modules’ configuration.
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web anti-virus products for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products