Doctor Web’s December 2021 review of virus activity on mobile devices
January 28, 2022
At the same time, more threats have been found on Google Play, like fake apps from the Android.FakeApp malware family. These are used in various fraudulent schemes. Trojans from the Android.Joker family that subscribe users to paid mobile services, and other malware were among discovered threats as well.
PRINCIPAL TRENDS IN DECEMBER
- Adware trojans remain among the most common threats found on Android devices
- The emergence of new trojans on Google Play
According to statistics collected by Dr.Web for Android
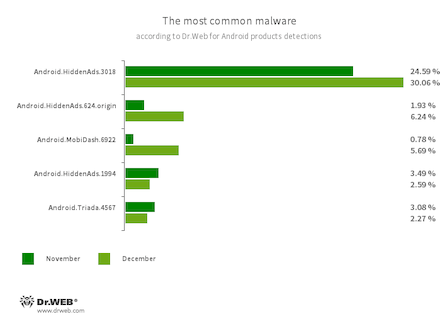
- Android.HiddenAds.3018
- Android.HiddenAds.624.origin
- Android.HiddenAds.1994
- Trojans designed to display obnoxious ads. Trojans of this family are often distributed as popular and harmless applications. In some cases, other malware can install them in the system directory. When these trojans infect Android devices, they typically conceal their presence from the user. For example, they “hide” their icons from the home screen menu. (The Android.HiddenAds.3018 is a newer version of the Android.HiddenAds.1994 trojan.)
- Android.MobiDash.6922
- A trojan that displays obnoxious ads. It represents a special software module that the developers incorporate into applications.
- Android.Triada.4567
- A multifunctional trojan that performs various malicious actions. This malware belongs to the trojan family that infects other app processes. Some modifications of this family can be found in the firmware of Android devices, which attackers implanted during manufacturing. Some of them can also exploit various vulnerabilities to gain access to protected system files and folders.
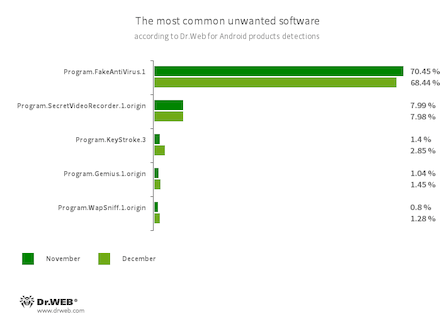
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of non-existing threats, mislead them, and demand they purchase the software’s full version.
- Program.SecretVideoRecorder.1.origin
- An application designed to record videos and take photos in the background using Android devices’ built-in cameras. It can operate covertly, allowing to disable notifications about ongoing recordings, as well as to replace the app’s icon and name with fake ones. Such functionality makes this software potentially dangerous.
- Program.KeyStroke.3
- An Android application capable of intercepting keystrokes. Some modifications of this software can also track incoming SMS, control call history, and record phone calls.
- Program.Gemius.1.origin
- An application that collects information about Android devices and how their owners are using them. With technical data, it also collects confidential information, like device location, browser bookmarks, web history, and typed URLs.
- Program.WapSniff.1.origin
- An Android program designed to intercept WhatsApp messages.
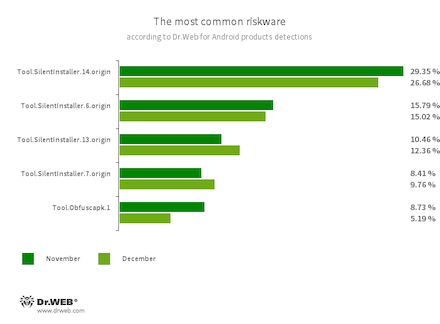
- Tool.SilentInstaller.14.origin
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.13.origin
- Tool.SilentInstaller.7.origin
- Riskware platforms that allow applications to launch APK files without installation. They create a virtual runtime environment that does not affect the main operating system.
- Tool.Obfuscapk.1
- The detection name for applications protected by the Obfuscapk obfuscation tool. This tool is used to automatically modify and scramble Android apps’ source code to make reverse engineering more difficult. Cybercriminals use this tool to protect malicious applications from being detected by anti-virus programs.
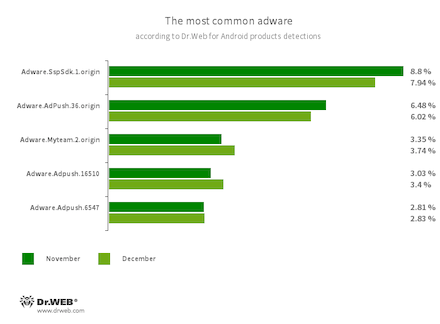
Program modules incorporated into Android applications and designed to display obnoxious ads on Android devices. Depending on their family and modifications, they can display full-screen ads and block other apps’ windows, show various notifications, create shortcuts, and load websites.
- Adware.SspSdk.1.origin
- Adware.AdPush.36.origin
- Adware.Adpush.16510
- Adware.Adpush.6547
- Adware.Myteam.2.origin
Threats on Google Play
New members of the Android.Joker malware family have been discovered on Google Play in December of 2021. These malicious apps download and run arbitrary code and subscribe users to paid mobile services. For example, Android.Joker.1097 and Android.Joker.1126 trojans were hiding in the messenger apps called Color Message and Elegant SMS. Android.Joker.1129 was spread as a Speed Clean Pro optimization tool designed to improve Android devices’ OS speed and functionality. The Android.Joker.1157 trojan was disguised as a PDF Camera Scanner app that allowed creating PDF documents, and Android.Joker.1160 as a Blood Pressure Record app to help users control their blood pressure.
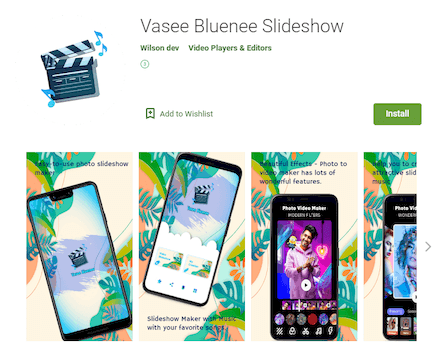
Our malware analysts also discovered another trojan from the Android.PWS.Facebook family. These malicious apps steal logins, passwords, and other data required to hack into Facebook accounts. The new modification of this family was spread as the Vasee Bluenee Slideshow app, designed to create slideshows and video clips. Its components were added to the Dr.Web virus base as Android.PWS.Facebook.101 and Android.PWS.Facebook.102.
Moreover, we also found more fake apps that are used in various scam schemes. The attackers spread some of them as software that provided information on social support in Russia. These apps include Android.FakeApp.721 (“Выплаты пособий населению” app) and Android.FakeApp.724 (“ФРП РУ Выплаты” app). Through them, the users could allegedly receive corresponding payments and compensations. The trojans, however, only loaded fraudulent websites where victims had to provide their personal information and pay a “commission” or “tax” to “transfer” money to their bank account.
Trojans dubbed Android.FakeApp.722 and Android.FakeApp.723 had similar functionality. Malware creators disguised them as apps that allegedly provided free lottery tickets. These programs loaded websites where users had to pay a “commission” in order to “get” the tickets and prizes.
At the same time, the Android.FakeApp.727 and Android.FakeApp.729 trojans were spread as cryptocurrency mining software. They hid in apps called Dogecoin Mining Cloud, Litecoin Mining Cloud, Bitcoin Miner, Ethereum Mining Cloud, and BTC Mining Cloud. Users who installed them were offered to gain cryptocurrency through the cloud service. To increase their mining power, they had to pay for premium plans.
These are not the first trojans of this type. For example, as early as August 2021, Doctor Web malware analysts discovered a similar malicious app called Multimine - BTC Cloud Mining. We added it to the Dr.Web virus base as Android.FakeApp.336.
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products