Doctor Web’s October 2020 review of virus activity for mobile devices
November 9, 2020
In October, the number of threats detected on Android devices increased by 12.36% compared to the previous month. According to statistics, malware increased by 9.08%, unwanted software by 6%, and riskware by 197.24%. With that, adware decreased by 1.51%.
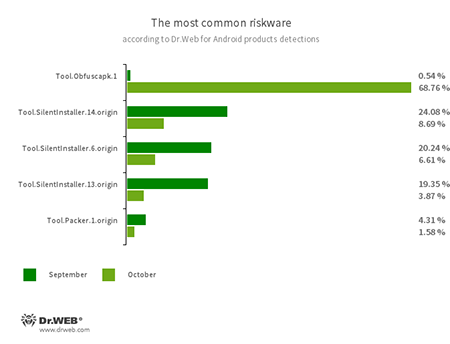
The near triple growth in detected riskware is due to the spread of apps protected by the Tool.Obfuscapk.1 tool. This tool is used to obscure the source code of Android applications. It can be used by legitimate developers, as well as malware creators trying to prevent anti-virus programs from detecting trojans.
New threats were also found on Google Play. Doctor Web specialists have discovered numerous trojans from the Android.FakeApp family. They were spread as reference software supposedly designed to help users get the information about their tax returns and availability of various social compensations. Their real purpose is to download fraudulent websites that scammers use to steal confidential information and money from victims.
Another malware from Google Play was dubbed Android.HiddenAds.2314. This trojan is designed to display obnoxious ads and was spread under the guise of picture editing software.
PRINCIPAL TRENDS IN OCTOBER
- An increased number of threats on Android devices
- A significant increase in riskware detected on protected devices
- New threats on Google Play
According to statistics collected by Dr.Web for Android
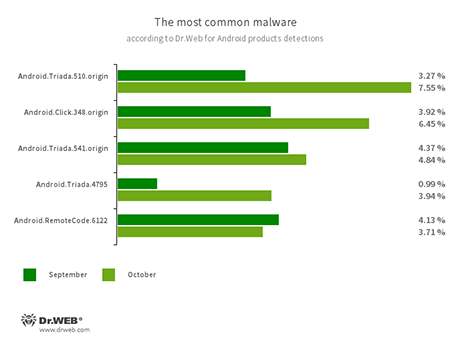
- Android.Triada.510.origin
- Android.Triada.541.origin
- Android.Triada.4795
- Multifunctional trojans that perform various malicious actions. This malware belongs to the trojan family that infects other apps’ processes. Some modifications of this family were found in the firmware of Android devices, which attackers implanted during manufacturing. Some of them can also exploit vulnerabilities to gain access to the protected system files and folders.
- Android.Click.348.origin
- A trojan that automatically loads websites and clicks links and advertisement banners. It can be spread as a harmless app so users will not perceive it as threatening.
- Android.RemoteCode.6122
- A malicious application that downloads and executes arbitrary code. Depending on its modification, it can load various websites, open web links, click advertisement banners, subscribe users to premium services and perform other actions.
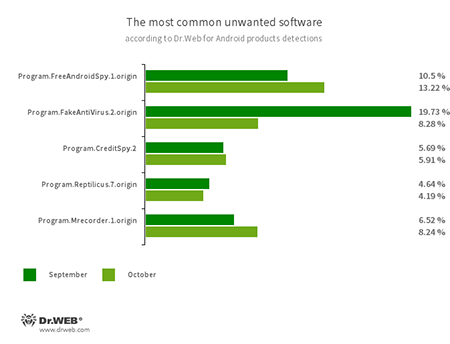
- Program.FreeAndroidSpy.1.origin
- Program.Reptilicus.7.origin
- Program.Mrecorder.1.origin
- Software that monitors Android user activity and may serve as a tool for cyber espionage. These apps can track device locations, collect information from SMS and social media messages, copy documents, photo and video, spy on phone calls, etc.
- Program.FakeAntiVirus.2.origin
- The detection name for adware programs that imitate anti-virus software. These apps inform users of non-existing threats, mislead them and demand they purchase the full version of the software.
- Program.CreditSpy.2
- The detection name for programs designed to assign credit ratings to users based on their personal data. These applications upload SMS, contact information from phonebooks, call history and other information to the remote server.
- Tool.Obfuscapk.1
- The detection name for applications protected by the Obfuscapk obfuscation tool. This tool is used to automatically modify and scramble Android apps’ source code to make reverse engineering more difficult. Cyber criminals use the tool to protect malicious applications from being detected by anti-virus programs.
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.13.origin
- Tool.SilentInstaller.14.origin
- Riskware platforms that allow applications to launch APK files without installation. They create a virtual runtime environment that does not affect the main operating system.
- Tool.Packer.1.origin
- A packer tool designed to protect Android applications from unauthorised modification and reverse engineering. This tool is not malicious by itself, but it can be used to protect both harmless and malicious software.
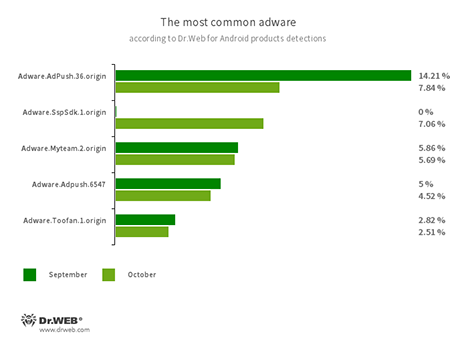
Program modules incorporated into Android applications and designed to display obnoxious ads on Android devices. Depending on their family and modifications, they can display full screen ads and block other apps’ windows, show various notifications, create shortcuts and load websites.
- Adware.Adpush.36.origin
- Adware.SspSdk.1.origin
- Adware.Adpush.6547
- Adware.Myteam.2.origin
- Adware.Toofan.1.origin
Threats on Google Play
In October, Doctor Web’s specialists discovered 17 new modifications of the Android.FakeApp trojan family, which were spread as harmless applications, namely reference software. Most of them were hidden in apps that were supposedly designed to help verify the availability of various social compensations and assist in receiving tax returns. According to Dr.Web’s classification, they were dubbed Android.FakeApp.208, Android.FakeApp.209, Android.FakeApp.210, Android.FakeApp.212, Android.FakeApp.213, Android.FakeApp.214, Android.FakeApp.215, and Android.FakeApp.216.
Another modification represented a sport-themed application and was added to the virus database as Android.FakeApp.211.
Their real and only functionality, however, was to load fraudulent websites. In total, these trojans have been downloaded over 105,000 times by the Android users.
Upon launching, these trojans load websites where a potential victim is asked to provide their personal information to “check” whether any financial reimbursements are available to them. After a reimbursement has been “found”, the user is asked for additional information and then prompted to pay a commission or fee to transfer the “refunded” money. If the user agrees, the thieves obtain the victim’s confidential data (e.g., name and surname, mobile number, email address, etc.) and their bank card information, including the CVV2 code. It goes without saying that the unfortunate victim does not receive any money.
The Android.HiddenAds.2314 trojan from the Android.HiddenAds malware family was another thread discovered on Google Play in October. It was spread as a picture editing application. Upon launch, its icon is hidden from the apps list in the main screen menu in order to make it harder for the user to locate the threat and delete it from the infected device. Next, it begins displaying obnoxious ads on top of the interface of other software and the system UI. This makes it more difficult to use the device.
We recommend users install Dr.Web anti-virus products for Android to protect their devices from malicious and unwanted programs.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products