Doctor Web's January 2020 virus activity review
February 11, 2020
In January, Dr.Web server statistics revealed an increase in the total number of threats by 0.53% compared with the previous month. The number of unique threats dropped by 5.06%. Malicious browser extensions and adware prevailed among malware and unwanted programs. E-mail traffic was still dominated by malware that exploits vulnerabilities found in Microsoft Office programs. With that, we saw a two-fold increase in the number of banking trojan detections — Trojan.SpyBot.699.
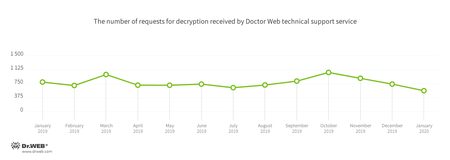
January also showed a downward trend in encoder activity. The number of user requests to decrypt infected files decreased by 24.02% as compared with December. Trojan.Encoder.26996 was the most active encoder, accounting for 18.48% of all incidents.
Principal trends in January
- The rise of malicious browser extensions
- Advertising trojans and adware remain amongst the most active threats
- An increase in the number of detected threats in e-mail traffic
- A decline in ransomware activity
According to Doctor Web’s statistics servers
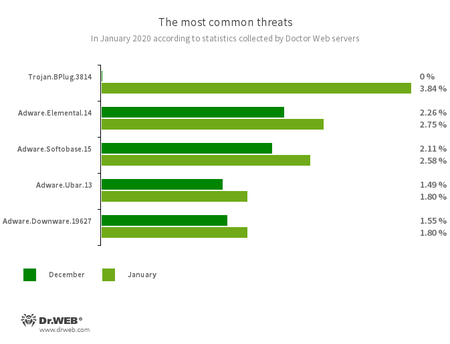
The most common threats in January:
- Trojan.BPlug.3814
- A malicious browser extension designed to perform web injections into viewed webpages and block third-party advertisements.
- Adware.Elemental.14
- Adware that spreads through file sharing services as a result of link spoofing. Instead of normal files, victims receive applications that display advertisements and install unwanted software.
- Adware.Softobase.15
- Installation adware that spreads outdated software and changes the browser’s settings.
- Adware.Ubar.13
- A torrent client designed to install unwanted programs on a user’s device.
- Adware.Downware.19627
- Adware that often serves as an intermediary installer of pirate software.
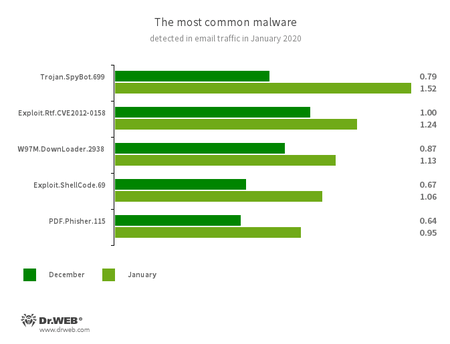
Statistics for malware discovered in email traffic
- Trojan.SpyBot.699
- A multi-module banking trojan. It allows cybercriminals to download and launch various applications on an infected device and run arbitrary code.
- Exploit.CVE-2012-0158
- A modified Microsoft Office document that exploits the CVE-2012-0158 vulnerability in order to run malicious code.
- W97M.DownLoader.2938
- A family of downloader trojans that exploit vulnerabilities in Microsoft Office applications. Designed to download other malware onto a compromised computer.
- Exploit.ShellCode.69
- A malicious Microsoft Office Word document that exploits the CVE-2017-11882 vulnerability.
- PDF.Phisher.115
- A PDF document used in phishing newsletters.
Encryption ransomware
In January, Doctor Web’s virus laboratory registered 24.02% fewer requests to decode files encoded by trojan ransomware than in December.
- Trojan.Encoder.26996 — 18.48%
- Trojan.Encoder.567 — 10.38%
- Trojan.Encoder.29750 — 4.81%
- Trojan.Encoder.858 — 3.54%
- Trojan.Encoder.11464 — 2.78%
Dr.Web Security Space for Windows protects against encryption ransomware
Dangerous websites
During January 2020, 97,166 URLs of non-recommended websites were added to the Dr.Web database.
| December 2019 | January 2020 | Dynamics |
|---|---|---|
| + 162 535 | + 97 166 | - 40.22% |
Malicious and unwanted programs for mobile devices
In January, the total number of detected threats on Android devices decreased by almost 13% compared to the previous month. At the same time, spyware and downloader trojans remain active.
During this month, Doctor Web virus analysts detected several new modifications of Android.Joker in Google Play. These trojans subscribe victims to paid services and download additional malicious components. Cybercriminals distributed them under the guise of harmless software — games, cameras, image galleries and other similar programs.
The following January events related to mobile malware are the most noteworthy:
- Detection of new threats on Google Play
- Decline in malware activity on protected devices
Find out more about malicious and unwanted programs for mobile devices in our special overview.