Doctor Web’s annual virus activity review for 2019
February 11, 2020
Overview
In 2019, two of the most common threats were trojans and malicious scripts designed to covertly mine cryptocurrencies. Trojans stealing passwords and other confidential information posed a serious threat as well. Throughout the year, users were attacked by banking trojans, such as Win32.Bolik.2. Doctor Web virus analysts detected it spreading in early spring and summer. This malware has properties reflective of a polymorphic file virus and is capable of infecting other applications. Win32.Bolik.2 performed web injections, hooked network traffic and keystrokes, and also stole information from bank-client systems.
In the spring, our experts discovered several vulnerabilities in the Steam client of the popular game, Counter Strike 1.6, which was exploited by the Belonard trojan. It made a botnet out of the infected computers and transformed them into proxy servers.
Email traffic was dominated by threats that downloaded other trojans onto the compromised computers and executed arbitrary code. Apart from that, cybercriminals distributed miners, spyware and banking trojans in email messages.
Even though most of the detected malware targeted Windows users, macOS users were also at risk. One of the threats they faced was the backdoor, Mac.BackDoor.Siggen.20, used by cybercriminals to download and execute arbitrary code on infected devices.
Android mobile device users were threatened by adware trojans, spyware, bankers, and all kinds of loaders that downloaded other malicious applications and executed arbitrary code.
Principal trends of the year
- The spread of miner trojans, designed to covertly mine cryptocurrencies
- An upturn in encoder activity
- New threats for macOS
- Rapid distribution of malware for Android on Google Play
Most notable events of 2019
In January Doctor Web’s researchers discovered a trojan in a cryptocurrency monitoring tool. This malware downloaded other Trojans on a victim’s PC and used them to steal private data, including passwords from cryptocurrency wallets.
In March, Doctor Web analysts published a detailed study of the Belonard trojan, which exploits zero-day vulnerabilities in the Counter-Strike 1.6 Steam client. Once on the victim’s computer, the trojan replaced client files and created game proxies to infect other users. The number of malicious CS 1.6 servers created by Belonard reached 39% of the total number of official servers registered on Steam. All Trojan.Belonard modules have been successfully detected by Dr.Web antivirus and do not threaten our users.
In May, Doctor Web experts reported on a new threat to the macOS operating system—Mac.BackDoor.Siggen.20. This software allowed Python code to be downloaded and executed on any of the user's devices. Websites that distribute this malware also infect Windows computers with the BackDoor.Wirenet.517 (NetWire) spyware trojan. The latter is a long-known RAT trojan that helps cybercriminals remotely control the victim’s computer, including using the camera and microphone on the device. Besides that, the distributed RAT trojan has a valid digital signature.
In June, a sample of the rare Trojan.MonsterInstall Node.js trojan was studied in the Doctor Web virus lab. When launched on a victim's device, it downloads and installs the modules it needs for operation, collects information about the system, and sends it to the developer’s server. After receiving a response from the server, it adds itself to autorun and starts mining the TurtleCoin cryptocurrency. Developers of this malware use cheats for popular games from their own webpages to distribute the trojan and infect files on other similar websites.
Virus situation
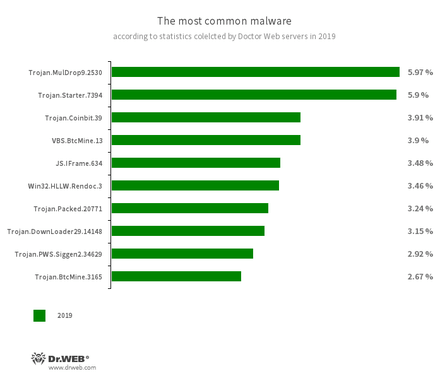
According to Doctor Web statistics servers, trojans and scripts that covertly mine cryptocurrency on devices were most often detected on computers in 2019. Trojans that installed various malware were active as well.
- Trojan.MulDrop9.2530
- A trojan dropper that distributes and installs malware.
- Trojan.Starter.7394
- A Trojan whose main purpose is to launch an executable file with a specific set of malicious functions in an infected system.
- Trojan.Coinbit.39
- Trojan.BtcMine.3165
- Trojans that silently mine cryptocurrency using the computing power of the infected devices.
- VBS.BtcMine.13
- A VBS script designed to covertly mine cryptocurrencies.
- JS.IFrame.634
- A script incorporated into html pages. When such pages are opened, the script redirects a user to malicious or unwanted websites.
- Win32.HLLW.Rendoc.3
- A network worm that spreads via removable media, among other channels.
- Trojan.Packed.20771
- A malware family protected by a packer.
- Trojan.DownLoader29.14148
- A trojan designed to launch other malicious software.
- Trojan.PWS.Siggen2.34629
- A representative of a trojan family that steals passwords.
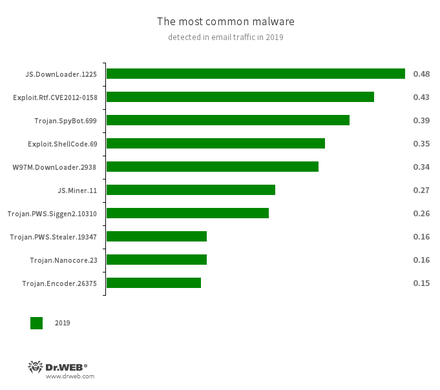
Email traffic was dominated by trojans that downloaded and installed other malware on compromised devices. Cybercriminals also used email to distribute ransomware, miners, banking trojans and spyware that stole confidential data.
- JS.DownLoader.1225
- A variety of malicious JavaScript scripts designed to download and install other malware on a computer.
- Exploit.Rtf.CVE2012-0158
- Modified Microsoft Office document. Exploits the CVE2012-0158 vulnerability in order to run malicious code.
- Trojan.SpyBot.699
- A multi-module banking Trojan. It allows cybercriminals to download and launch various applications on an infected device and their commands to be executed. The Trojan is intended to steal money from bank accounts.
- Exploit.ShellCode.69
- A family of malicious programs designed to download other malware to the compromised computer.
- W97M.DownLoader.2938
- A family of downloader trojans that exploit vulnerabilities in office applications and can download other malicious programs to a compromised machine.
- JS.Miner.11
- A family of JavaScript scenarios designed to covertly mine cryptocurrencies.
- Trojan.PWS.Siggen2.10310
- Trojan.PWS.Stealer.19347
- Representatives of a trojan family that steals credentials.
- Trojan.Nanocore.23
- A trojan that helps cybercriminals connect to infected computers and control them.
- Trojan.Encoder.26375
- Malware that encrypts files and demands a ransom to decrypt them.
Encryption Trojans
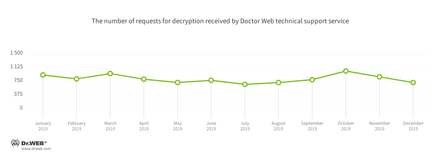
Compared to 2018, the number of help tickets to Doctor Web technical support with requests to decrypt files encrypted by trojan encoders increased by 19.52% over the past 12 months. See the request dynamics for 2019 below:
The most common ransomware programs in 2019:
- Trojan.Encoder.858 — 20,18% requests;
- Trojan.Encoder.18000 — 5.70% requests;
- Trojan.Encoder.11464 — 5,59% requests;
- Trojan.Encoder.26996 — 5.15% requests;
- Trojan.Encoder.567 — 4,20% requests;
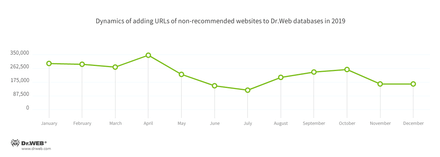
Dangerous and non-recommended websites
SpIDer Gate's Parental (Office) Control and Web Antivirus databases are regularly updated with new addresses of non-recommended and potentially dangerous websites. The list includes fraudulent and phishing resources, as well as webpages that distribute malware. The largest number of such websites was recorded in the first quarter, dropping to the lowest in the third quarter. See the dynamics of the updates to the databases of non-recommended and dangerous websites over the last year below.
Network fraud
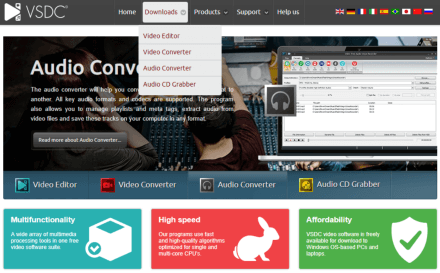
In April, Doctor Web specialists warned users about the official website of popular software for video and sound processing being compromised. Cybercriminals replaced the download link so that users downloaded the dangerous banking trojan, Win32.Bolik.2, together with the editor. The trojan is designed to perform web injections, hook traffic, keylog (registering keystrokes on the keyboard), and steal information from the bank-client systems of various financial institutions.
Cybercriminals later replaced Win32.Bolik.2 with another malware—a version of the Trojan.PWS.Stealer spyware (the KPOT Stealer). This trojan steals information from browsers, Microsoft accounts, various instant messengers, and other software.
In August, experts of the Doctor Web virus lab discovered that cybercriminals changed their strategy in mid summer and started copying websites of popular services to distribute Win32.Bolik.2. One of these resources was mimicking a well-known VPN service, while others were disguised as corporate office software websites.
Mobile devices
Last year was memorable for mobile users by virtue of trojans and unwanted software that mainly displayed ads. Among them were numerous trojans of the Android.HiddenAds family.
For example, Doctor Web virus analysts discovered about 40 different modifications of these malicious applications on Google Play only in February, and they were installed by more than 10 million users. Throughout the year, our experts identified hundreds of such trojans. In total, they accounted for 22.27% of all threats detected on Android devices.
Attackers spread them under the guise of useful programs and even advertised them on social media and popular online services with millions of audience members (for example, Instagram and YouTube). Users believe they are installing harmless applications, so the trojans easily get ahold of many devices.
Upon installation and launch, the Android.HiddenAds trojans hide their icons from the list of apps on the home screen and start displaying annoying ads: banners, windows with animations, and videos. Such advertising blocks the windows of other applications and the operating system interface, interfering with the normal operation of Android devices.
In the spring, our virus analysts discovered the trojan Android.InfectionAds.1, which exploited critical vulnerabilities in the Android OS. It infected other software and could install applications without a user’s permission. The main function of Android.InfectionAds.1 was to display ads and replace advertising identifiers in the infected applications. The scheme diverted advertising revenue to the virus writers rather than to the app developers.
The creators of unwanted advertising modules (Adware), which many developers knowingly and sometimes unknowingly integrate into applications to monetize them, received money from displaying ads as well. The share of such modules among all Android threats was 14.49%.
As in previous years, users were targeted by various trojan downloaders and malware that download other trojans and applications, as well as execute arbitrary code. Such threats include, for example, representatives of the Android.DownLoader, Android.Triada, and Android.RemoteCode families. In 2019, these trojans were amongst the most common threats detected on Android devices.
In 2019, we detected many new clicker trojans that automatically follow links, load web pages with ads, and subscribe users to paid mobile services. Among the malware found by our experts were Android.Click.312.origin, Android.Click.322.origin, Android.Click.323.origin, and Android.Click.324.origin. These and other similar trojans spread under the guise of harmless and useful applications, such as photo editors, collections of desktop wallpapers, games, etc.
Banking trojans, which attacked users around the world, still posed a serious threat to Android device owners. For example, in August and October, Doctor Web virus analysts discovered yet another modification of the dangerous trojan, Android.BankBot.495.origin, aimed at clients of Brazilian financial organizations. This malicious application exploited the Android Accessibility Service, designed for people with disabilities. Using these functions, the banker steals confidential data, and cybercriminals use it to gain access to victims’ accounts.
The Flexnet Trojan, which belongs to the Android.ZBot family, continued to target users. By modern standards, this malware has a modest set of functions, which, however, are enough to successfully steal money from user accounts. With the help of this banker, cybercriminals steal victims' money, transferring it to their bank cards, mobile phone accounts, and as payment for various services.
The past year confirmed that cyber spying and sensitive data leaks remain relevant. In June, our experts uncovered the dangerous backdoor, Android.Backdoor.736.origin, on Google Play, also known as PWNDROID1. Later in November, its new modification was found. This trojan allowed cybercriminals to remotely control infected Android devices and perform various actions, such as hook SMS messages, monitor phone calls and device locations, listen to the environment, transfer user files to the server, and even download and install other software.
New user monitoring software was discovered in 2019 as well. Such applications are often promoted as a means of ensuring the safety of children and other family members, monitoring workers, etc. They are not malicious, but they can be used for illegal purposes.
Users of Android devices should also be wary of scammers. For example, trojans of the Android.FakeApp family, which loaded websites with fake polls, have been spreading again. Potential victims were offered a cash reward for taking part in the poll. To get the reward, users supposedly had to pay a fee or confirm their identity by transferring a certain amount to the scammers’ account. However, the victims never received any reward and lost the money.
Prospects and possible trends
At the end of 2018, users faced many informational threats, and their main risk was the loss of money and cyber spying. Our forecast suggested that this trend should have continued in 2019, which turned out to be true.
In the coming year, cybercriminals will continue to use malware to gain money illegally. In this regard, we should expect an increase in the activity of miner trojans, banking and adware trojans, as well as spyware, which will collect valuable information about users. Besides that, new fraudulent schemes are likely to emerge, as well as phishing campaigns and spamming.
It is not only Windows users who will be targeted. Owners of devices running macOS, Android, Linux, and other OS will remain on virus writers’ and online scammers’ radar. The malware and the ingenuity of cybercriminals will keep evolving, so users need to follow the rules of information security and use reliable anti-virus tools.