Doctor Web’s overview of malware detected on mobile devices in September 2019
October 9, 2019
In September, Android users were threatened by various malware, many of which was distributed via Google Play. Those were the Android.DownLoader downloaders, the Android.Banker and Android.HiddenAds banking and adware trojans, as well as other threats. Doctor Web experts have also discovered several new versions of potentially dangerous applications, designed to spy on users, including Program.Panspy.1.origin, Program.RealtimeSpy.1.origin, and Program.MonitorMinor.
PRINCIPAL TRENDS IN SEPTEMBER
- Google Play remains the source of malicious and unwanted applications
- Users are still threatened by spyware
Mobile threat of the month
One of the malware detected last month was the Android.Banker.352.origin banking trojan, spread under the guise of the YoBit crypto exchange official application.
When launched, Android.Banker.352.origin displayed a fake authentication window and stole the credentials entered by customers. Then, it displayed an error message claiming the service was unavailable.
The trojan hooked two-factor authentication codes from text messages, as well as access codes from emails. It also hooked and blocked notifications from instant messengers and email clients. Android.Banker.352.origin stored all the stolen data in the Firebase Database.
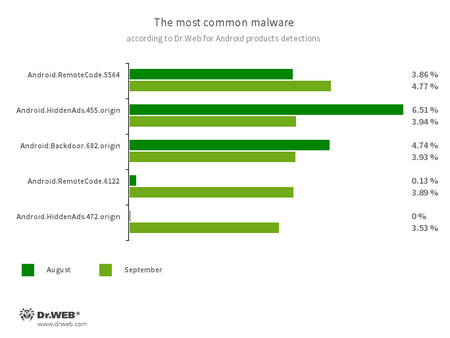
According to statistics collected by Dr.Web for Android
- Android.RemoteCode.6122
- Android.RemoteCode.5564
- Malicious applications that download and execute arbitrary code.
- Android.HiddenAds.455.origin
- Android.HiddenAds.472.origin (new threat)
- Trojans that display unwanted ads on mobile devices.
- Android.Backdoor.682.origin
- A trojan that executes cybercriminals’ commands and helps them control infected mobile devices.
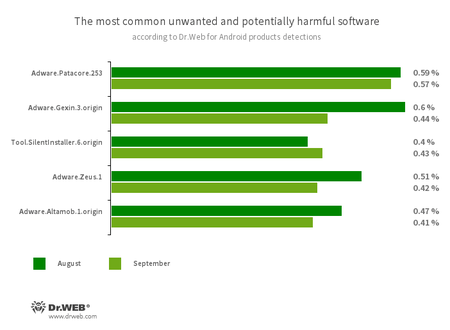
Program modules that incorporate themselves into Android applications and display obnoxious ads on mobile devices:
- Adware.Patacore.253
- Adware.Gexin.3.origin
- Adware.Zeus.1
- Adware.Altamob.1.origin
Riskware that silently launches applications without user intervention:
- Tool.SilentInstaller.6.origin
Threats on Google Play
In addition to the Android.Banker.352.origin banking trojan, September saw Doctor Web specialists detect the Android.Banker.347.origin malware on Google Play. It targeted Brazilian customers of credit service organizations. It is a modification of Android.BankBot.495.origin, Android.Banker.346.origin, and other bankers, reported by our company in earlier publications.
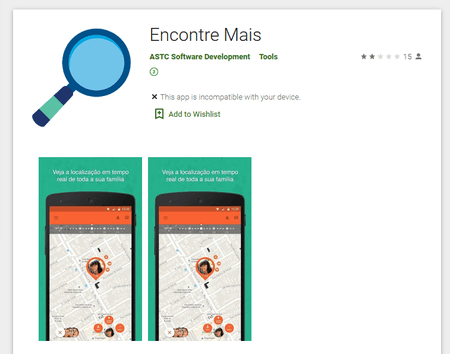
Attackers distributed Android.Banker.347.origin via Google Play under the guise of software that helped locate family members.
The banker used the Android Accessibility Service to steal information from text messages, such as confirmation codes and other sensitive data. Similarly to its previous modifications, it could also open phishing pages at the command of cybercriminals.
Last month, virus analysts detected several new adware trojans of the Android.HiddenAds family on Google Play, such as Android.HiddenAds.444.origin. This malware was embedded in harmless software and games. When launched, it hid its icon and started to display obnoxious advertising banners. At the command of the command and control server, it could download and try to install APK files.
Among the detected malware were trojan downloaders, such as Android.DownLoader.920.origin and Android.DownLoader.921.origin. They were spreading under the guise of games. The trojans downloaded and tried to install various software, as well as other malicious programs, at the server’s command.
In September, several modifications of the Android.Joker trojan family were found on Google Play. These malicious applications were embedded in seemingly harmless software, such as plug-ins for cameras, photo editors, image collections, various system utilities, and other software.
Trojans are able to load and run auxiliary DEX files, as well as execute arbitrary code. They can also automatically subscribe users to expensive services by loading websites with premium content and clicking the appropriate links without user’s knowledge. To confirm the subscription, they hook verification codes from text messages. The Android.Joker malware also transfers the data from victims’ contact lists to the command and control server.
Other trojans that subscribed users to expensive services were dubbed Android.Click.781 and Android.Click.325.origin. They also loaded websites to subscribe the victims to premium services. Besides, they could hook notifications of the operating system and other software at the server’s command. The cybercriminals were spreading these trojans under the guise of camera applications.
Spyware
In September, Doctor Web experts discovered several new versions of riskware, designed to spy on Android device users. The list included Program.Panspy.1.origin, Program.RealtimeSpy.1.origin, and Program.MonitorMinor. This spyware enables control of texting and phone calls, instant messaging, tracking the location of devices, and receiving other confidential information.
To protect your Android device from malware and unwanted programs, we recommend that you install Dr.Web for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products