April 2019 mobile malware review from Doctor Web
April 30, 2019
In April Doctor Web reported on the Android.InfectionAds.1 trojan that exploited several critical Android OS vulnerabilities. These vulnerabilities allowed the trojan to infect programs, as well as install and uninstall software independently from users. In addition, virus analysts found new modifications of the banking trojan Android.Banker.180.origin designed to steal money from clients of Japanese credit organizations. Other malicious programs distributed via Google Play were detected. The downloader trojans Android.DownLoader that downloaded banking trojans on mobile devices, clickers from the Android.Click family, the stealers Android.PWS.Instagram that stole Instagram users’ logins and passwords. Aside from that, the Dr.Web virus database was updated with new entries to detect additional malware.
PRINCIPAL TRENDS IN APRIL
- The detection of new malicious applications on Google Play
- Distribution of banking trojans
Mobile threat of the month
In early April Doctor Web reported on a dangerous trojan, Android.InfectionAds.1. Hackers embed it into initially benign programs and use popular third-party Android stores for its distribution. This trojan exploits critical vulnerabilities of Android OS to infect APK files (the CVE-2017-13156 vulnerability), as well as to install and uninstall programs (the CVE-2017-13315 vulnerability). Android.InfectionAds.1 also shows annoying banner ads, making it difficult to work with infected devices. See detailed information about the trojan in our virus library.
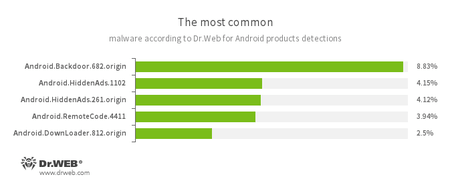
According to statistics collected by Dr.Web for Android
- Android.Backdoor.682.origin
- A trojan that executes cybercriminals’ commands and helps them control infected mobile devices.
- Android.HiddenAds.1102
- Android.HiddenAds.261.origin
- Trojans designed to display intrusive advertisements. They are distributed as popular applications by other malicious programs; which in some cases, covertly install them in the system catalog.
- Android.RemoteCode.4411
- A malicious application designed to download and execute arbitrary code.
- Android.DownLoader.812.origin
- A Trojan that downloads other malicious applications.
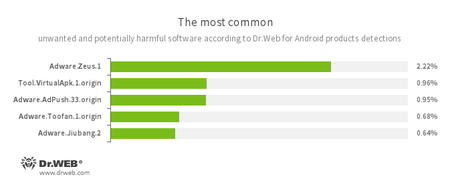
- Adware.Zeus.1
- Adware.AdPush.33.origin
- Adware.Toofan.1.origin
- Adware.Jiubang.2
- Unwanted program modules that incorporate themselves into Android applications and display obnoxious ads on mobile devices.
- Tool.VirtualApk.1.origin
- A riskware platform that allows applications to launch APK files without installing them.
Banking trojans for Android
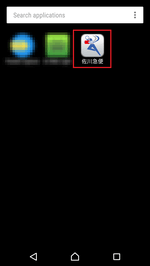
Over the past month, banking trojans threatened users of Android devices. In late April Doctor Web virus analysts detected new modifications of the Android.Banker.180.origin malware. These modifications were distributed under the guise of package tracking apps (for example, an app titled “佐川急便”) targeting Japanese users. Once installed, these trojans delete their own icons and hide themselves from users.
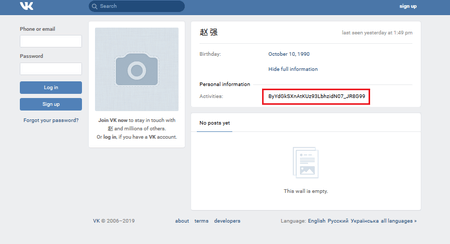
These modifications of Android.Banker.180.origin are controlled via specially created pages in the Russian social network, Vkontakte. On such pages, the encrypted address of one of the trojan command and control servers is specified in the “Activities” field. The malware looks for this field using a regular expression, decrypts the address, and connects to the server.
These trojan modifications are able to intercept and send SMS on hackers’ command, show phishing windows, make calls, and listen to the surrounding environment using the device’s built-in microphone. On top of that, they can control smartphones and tablets; for example, they can turn on Wi-Fi, connect to the Internet via a mobile network, block the screen, and so on.
In addition, new downloaders from the Android.DownLoader family, such as Android.DownLoader.4303, downloaded Android bankers on mobile devices. They were distributed under the guise of financial applications.
Trojans on Google Play
Aside from downloaders, other trojans, such as Android.Click.303.origin and Android.Click.304.origin were detected on Google Play. They were distributed under the guise of benign applications such as games and programs for watching TV channels. Doctor Web virus analysts detected 36 of theses trojans. More than 151,000 people installed them.
This malicious software opens hidden activity with several WebView elements. A website is loaded on one of them to get commands. Hackers use other WebViews to load different JavaScript and specified websites where they simulate user actions. On these websites, they click links and banner ads to drive up hit and click counters. Hackers can also subscribe mobile device owners to paid services by clicking on special buttons if service providers support the Wap-Click technology of fast subscription. To make themselves more difficult to delete, trojans hide their icons from the operating system’s main screen.
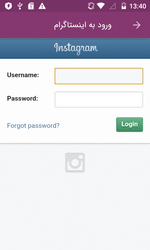
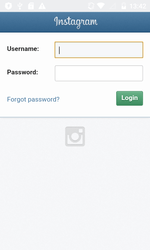
In late April, new entries were added to the Dr.Web virus database to detect the trojans Android.PWS.Instagram.4 and Android.PWS.Instagram.5. Hackers guised them as useful programs for Instagram users, for instance, those intended to drive up the number of likes or followers, as well as to increase the account security. Once launched, trojans asked victims to enter their login and password and then sent that data to the hackers’ server.
Other threats
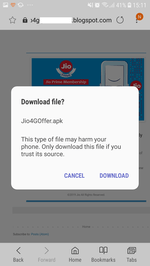
The Android.FakeApp.2.origin trojan was one of the malicious apps that threatened Android smartphone and tablet owners in April. It was hidden in a program that allegedly provided free 25 GB of Internet traffic to Indian users of the Jio service provider.
To distribute itself among a greater number of users, the trojan sent SMS with a link to the download page of its copy to all contacts of the infected device. The main goal of Android.FakeApp.2.origin was showing banner ads.
Users of Android devices are threatened by different trojan applications that are distributed not only via malicious websites, but also via the official Google Play store. To protect smartphones and tablets, we recommend that you install Dr.Web for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products