Doctor Web’s overview of malware detected on mobile devices in November 2018
November 30, 2018
In the last month of autumn 2018, Doctor Web’s malware analysts detected a new Android-targeting banking Trojan. It was being spread via Google Play and was attacking the customers of European financial institutions. Other Trojans were detected on Google Play in November, as were unwanted software programs.
PRINCIPAL TRENDS IN NOVEMBER
- The distribution of malicious and unwanted programs on Google Play
Mobile threat of the month
In mid-November, Doctor Web’s experts discovered the banking Trojan Android.Banker.2876, which was attacking the customers of several European financial organizations. It was stealing confidential information and was also intercepting and sending SMS.
Features of Android.Banker.2876:
- Distributed via Google Play;
- imitated the banking applications of Spanish, French, and German financial organizations;
- hid its icon from the app list on the home screen;
- contained an embedded game that would launch after users closed its window.
For more information regarding this Trojan, refer to this news article on our website.
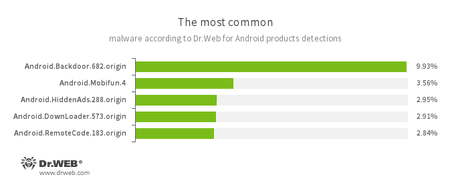
According to statistics collected by Dr.Web for Android
- Android.Backdoor.682.origin
- A Trojan that executes cybercriminals’ commands and helps them control infected mobile devices.
- Android.Mobifun.4
- A Trojan that downloads various applications.
- Android.HiddenAds.288.origin
- A Trojan designed to display advertisements. It is distributed under the guise of popular apps by other malicious programs that in some instances covertly install it in the system directory.
- Android.DownLoader.573.origin
- A Trojan that downloads other malware applications.
- Android.RemoteCode.183.origin
- A malicious program designed to download and execute arbitrary code.
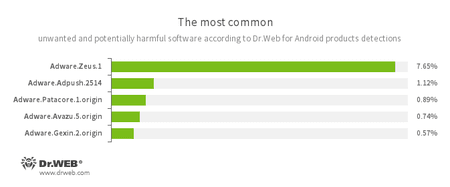
- Adware.Zeus.1
- Adware.Adpush.2514
- Adware.Patacore.1.origin
- Adware.Avazu.5.origin
- Adware.Gexin.2.origin
- Unwanted program modules incorporated into Android applications and designed to display obnoxious ads on mobile devices.
Threats on Google Play
In early November, on Google Play, Doctor Web’s virus analysts detected applications containing the unwanted adware modules Adware.HiddenAds.7.origin and Adware.HiddenAds.8.origin. They displayed ads independently of the programs in which they had been embedded.
Later in the month, Doctor Web’s experts identified on Google Play other Android.FakeApp family Trojans which were added to the Dr.Web virus database as Android.FakeApp.138, Android.FakeApp.139, and Android.FakeApp.144. They were hidden in applications that allegedly paid people to participate in polls. When launched, the malware loaded fraudulent websites where potential victims were asked to answer a few questions. After that, in order to receive a “reward”, the user was required to pay a fee for a wire transfer, currency conversion, or any other procedure named by the attackers. If the owner of an affected mobile device agreed to pay, the requested amount was transferred to the pockets of cybercriminals, while the fraud victim got nothing.
In addition, attackers distributed the Trojan downloader Android.DownLoader.832.origin under the guise of various utilities. It downloaded and tried to install other malicious applications.
Google Play remains the most secure Android app resource. However, cybercriminals are still managing to use it to distribute malicious software. To protect their Android mobile devices, users are recommend to install Dr.Web for Android antivirus products.
Your Android needs protection
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 135 million downloads on Google Play alone
- Free for users of Dr.Web home products