Doctor Web’s September 2017 virus activity review
September 29, 2017
In September, numerous media outlets reported that cybercriminals had actively started exploiting user browsers to illegally mine cryptocurrencies. The most popular cryptocurrency among cybercriminals is Monero (XMR).
The miner, written in JavaScript, was added to the Dr.Web virus databases under the name Tool.BtcMine.1046. When users visited certain websites, the JavaScript integrated into the webpage code would start mining the cryptocurrency. According to user reports, at that moment the CPU load reached 100% and went back to normal values only after they shut down the browser window. It is hard to say whether this incident is the result of a website hacking or website owners deliberately injecting the miner into their sites. Currently, when users try to visit webpages containing such scripts, Dr.Web Anti-virus warns them that it has detected potentially dangerous content.
Soon thereafter one more similar instrument, this one dubbed Tool.BtcMine.1048, was added to the virus database. This miner was also written in JavaScript. Perhaps, it was supposed to be an alternative to monetization via advertising. However, it was used without the explicit consent of website visitors. In other words, this technology can be used either legally or for criminal earnings. Such scripts can be injected into a website’s code not only by website owners but also with the assistance of unscrupulous advertisers or as a result of hacking. In addition, the function for mining cryptocurrency can also be implemented in plugins installed by users on their browsers.
Also in September, security specialists detected vulnerabilities in the Bluetooth protocol stack, and Doctor Web analysts discovered that cybercriminals were using the Internet of things (Iot) for mass spam mailings.
Principal trends in September
- The mining programs written in JavaScript
- Cybercriminals using the IoT to distribute spam messages
- The dangerous vulnerabilities in the Bluetooth protocol protocol
Threat of the month
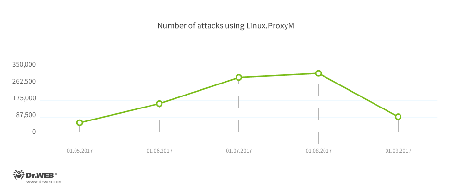
Doctor Web has already published an article about the malicious program Linux.ProxyM, which launches a SOCKS proxy server on the Linux devices it infects. Builds of this Trojan exist for devices possessing the following architectures: x86, MIPS, MIPSEL, PowerPC, ARM, Superh, Motorola 68000, and SPARC. This means the Trojan is capable of operating on numerous “smart” devices, such as routers, set-top boxes, etc. Virus analysts have established that cybercriminals are using infected devices to distribute spam that advertises adult content resources. A device infected with Linux.ProxyM sends on average about 400 emails per day. The activity of this botnet is illustrated in the graph below:
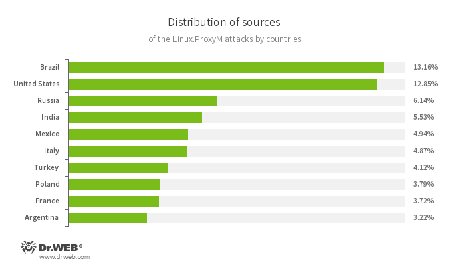
Most of the devices infected with Linux.ProxyM that are being used to carry out the attacks are from Brazil. The United States and Russia were ranked second and third respectively.
More information about Linux.ProxyM can be found in an article published by Doctor Web.
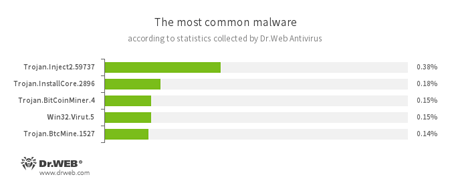
According to Dr.Web Anti-virus statistics
- Trojan.Inject
- A family of malicious programs that inject malicious code into the processes of other programs.
- Trojan.InstallCore
- A family of installers of unwanted and malicious applications.
- Trojan.BitCoinMiner.4
- A Trojan from a family of malicious programs designed to stealthily mine BitCoin electronic currency.
- Win32.Virut.5
- A polymorphic virus that infects executable files. It functions for managing infected computers through the use of IRC channel.
- Trojan.BtcMine
- A family of malicious programs that stealthily uses the computing resources of an infected computer to mine a variety of electronic currencies, e.g., Bitcoin.
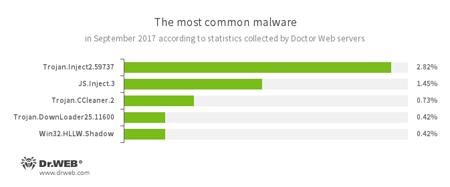
According to Doctor Web’s statistics servers
- Trojan.Inject
- A family of malicious programs that inject malicious code into the processes of other applications.
- JS.Inject.3
- A family of malicious JavaScripts. They inject a malicious script into the HTML code of webpages.
- Trojan.CCleaner.2
- A malicious program detected in CCleaner, an application used to optimize Microsoft Windows operating systems.
- Trojan.DownLoader
- A family of malicious programs designed to download other malware to the compromised computer.
- Win32.HLLW.Shadow
- A worm that replicates itself through removable media and network drives. In addition, it can be spread via a network through the use of the standard SMB protocol. It can download executable files from a command and control server and run them.
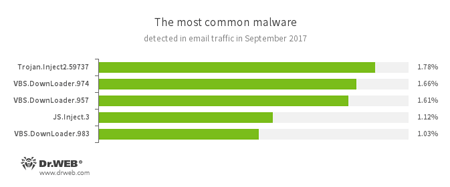
Statistics concerning malicious programs discovered in email traffic
- Trojan.Inject
- A family of Trojans that inject malicious code into the processes of other programs.
- VBS.DownLoader
- A family of malicious JavaScripts. They download and install malicious software on a computer.
- JS.Inject.3
- A family of malicious JavaScripts. They inject a malicious script into the HTML code of webpages.
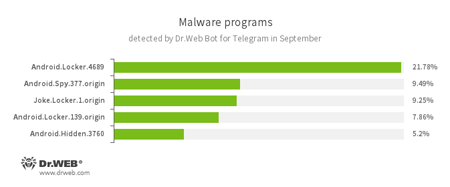
According to Dr.Web Bot for Telegram data
- Android.Locker
- A family of ransomware Trojans for Android. They can lock a device after alleging via an on-screen warning that the device owner has done something illegal. To unlock the device, the owner has to pay a ransom.
- Android.Spy.337.origin
- A Trojan for Android that steals confidential information, including user passwords.
- Joke.Locker.1.origin
- A joke program for Android that blocks a mobile device’s screen and displays the Windows BSOD (Blue Screen of Death).
- Android.Hidden
- Android Trojans capable of hiding their shortcuts in the list of applications on an infected device.
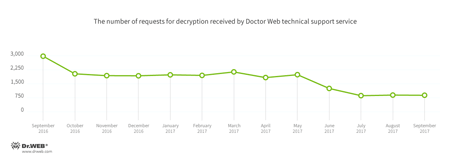
Encryption ransomware
In September, cases involving the following ransomware modifications were registered by Doctor Web’s technical support service:
- Trojan.Encoder.858 — 23.49% of requests;
- Trojan.Encoder.13671 — 5.33% requests;
- Trojan.Encoder.11464 — 3.89% of requests;
- Trojan.Encoder.761 — 2.74% of requests;
- Trojan.Encoder.5342 — 2.02% of requests;
- Trojan.Encoder.567 — 2.00% of requests.
Dr.Web Security Space for Windows protects against encryption ransomware
Dangerous websites
During September 2017, 298,324 URLs of non-recommended websites were added to the Dr.Web database.
| August 2017 | September 2017 | Dynamics |
|---|---|---|
| + 275,399 | + 298,324 | +8.32% |
Malicious and unwanted programs for mobile devices
In September, information surfaced that a group of dangerous BlueBorne vulnerabilities implemented with the Bluetooth protocol had been identified. Various devices, including Android smartphones and tablets, were affected. These vulnerabilities allow criminals to gain full control over attacked devices, execute arbitrary code, and steal confidential information. Also in the past month, Google Play was infiltrated by the Trojan Android.BankBot.234.origin which is designed to steal bank card information.
Among the most notable September events related to mobile malware:
- The emergence of details on previously detected vulnerabilities in the Bluetooth protocol stack;
- The discovery of a banking Trojan on Google Play.
Find out more about malicious and unwanted programs for mobile devices in our special overview.