Doctor Web’s overview of malware detected on mobile devices in August 2017
August 31, 2017
In August, numerous malicious Android applications were detected on Google Play. Among them were Trojans that mounted DDoS attacks. Other malicious programs covertly loaded websites specified by cybercriminals and independently tapped on their banners, bringing profits to the virus writers who created them. Yet another Android Trojan detected on Google Play in August displayed fake input forms over launched programs and stole login credentials and other confidential information. The last summer month was also marked by the detection on Google Play of a dropper Trojan designed to install other malicious applications.
PRINCIPAL TRENDS IN AUGUST
- The detection of malicious Android programs mounting DDoS attacks on websites;
- The detection on Google Play of an Android banker being distributed under the guise of a benign program;
- The infiltration of Google Play by a Trojan designed to install other malicious applications.
Mobile threat of the month
In August, several new Android.Click Trojans were detected on Google Play. Two of them were dubbed Android.Click.268 and Android.Click.274, respectively. Once launched on mobile devices, they imperceptibly mount DDoS (“Denial of service”) attacks on websites specified by cybercriminals by opening multiple copies of them. When commanded, they can also send scores of network packets to targeted servers. As a result, the Android smartphone and tablet users who downloaded these programs and thus infected their devices unintentionally became accomplices to cybercrimes.
Another Trojan, which was added to the Dr.Web database as Android.Click.269, covertly opened websites specified in the commands of cybercriminals and tapped on the banners located on them. Such actions brought profits to the malicious application’s authors. In addition, Android.Click.269 displayed advertisements once the screen of an infected Android device was unlocked.
All the aforementioned Trojans were embedded in software designed to stream YouTube videos.
Features of Android.Click.268 and Android.Click.274:
- Mount DDoS attacks on websites via the covert loading of 20 copies of a web resource specified by cybercriminals;
- Can mount DDoS attacks on remote hosts via the UDP protocol by sending 10 million packets to a server port specified in a command.
Features of Android.Click.269:
- Covertly opens websites specified in the commands of cybercriminals and automatically taps on advertising banners, thus bringing profits to the Trojan’s authors;
- Displays advertisements once the screen of an infected Android device has been unlocked.
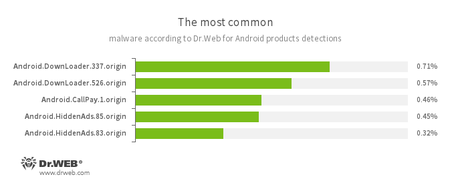
According to statistics collected by Dr.Web for Android
- Android.DownLoader.337.origin
- Android.DownLoader.526.origin
- Trojan programs designed to download other applications.
- Android.CallPay.1.origin
- A Trojan that provides access to adult content while covertly making phone calls to premium numbers as a payment for this service.
- Android.HiddenAds.85.origin
- Android.HiddenAds.83.origin
- Trojans designed to display unwanted ads on mobile devices. They are distributed under the guise of popular apps by other malicious programs that sometimes covertly install them in the system directory.
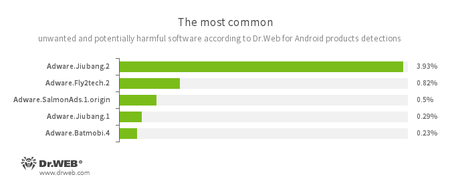
- Adware.Jiubang.2
- Adware.Fly2tech.2
- Adware.SalmonAds.1.origin
- Adware.Jiubang.1
- Adware.Batmobi.4
- Unwanted program modules incorporated into Android applications and designed to display annoying ads on mobile devices.
Trojan on Google Play
During the last summer month, a banking Trojan named Android.BankBot.225.origin was added to the Dr.Web virus database. The Trojan was being distributed via Google Play. It was hidden in an application called “Earn Real Money Gift Cards” which garners users money gift certificates for installing advertising programs.
Android.BankBot.225.origin tracks the launch of banking and other applications and displays on top of their windows fake forms for inputting confidential information. In addition, when commanded by cybercriminals, it can download other programs to infected devices and then try to install them.
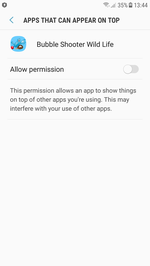
Yet another Trojan detected on Google Play in August was added to the Dr.Web virus database as Android.MulDrop.1067. It was hidden in a game called “Bubble Shooter Wild Life”. Each time it starts up, this malicious program asks for permission to display interface elements on top of other applications.
Sometime after its launch, it attempts to gain access to the Accessibility Service by displaying the respective notification. If a device owner agrees to grant the Trojan such privileges, Android.MulDrop.1067 can independently install other Android applications by automatically tapping buttons in dialogs and confirming all actions. The Trojan checks whether an APK file is available on a memory card. It must install this file; however, the current version of Android.MulDrop.1067 doesn’t contain any hidden files and cannot download them from the Internet. This could be a sign that the Trojan is still under development.
Cybercriminals are using every possible way to distribute Android Trojans via Google Play. To increase the likelihood of mobile device infection, they embed malicious programs in fully functioning applications and use different mechanisms to bypass security checks so the Trojans go unnoticed for as long as possible. Doctor Web recommends that Android smartphone and tablet users install Dr.Web anti-virus products to protect them from current Android threats.
Your Android needs protection
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 100 million downloads on Google Play alone
- Free for users of Dr.Web home products