June 2017 mobile malware review from Doctor Web
July 3, 2017
In June, Doctor Web security researchers detected an Android Trojan that attacked Iranian mobile device users and executed the commands of cybercriminals. Also in the past month, several new malicious applications were detected on Google Play. One of them tried to gain root access, infiltrated system libraries, and could covertly install software. Other applications sent SMS messages to premium numbers and subscribed users to expensive services. Also distributed on Google Play was riskware that, if used, could lead to the leak of confidential information. In addition, a new encryption Trojan for Android was detected in June.
PRINCIPAL TRENDS IN JUNE
- The detection of an Android Trojan designed to engage in cyber espionage
- The detection of threats on Google Play
- The distribution of an encryption ransomware program for Android
Mobile threat of the month
In June, Doctor Web security researchers detected Android.Spy.377.origin, which was spreading among Iranian mobile device users. This malicious program would steal confidential information and send it to cybercriminals. In addition, it could execute their commands.
Features of Android.Spy.377.origin:
- It is distributed under the guise of benign programs;
- It steals SMS correspondence, contacts from the contact list, and Google account data;
- It can take photos with a device’s front camera;
- Cybercriminals control it via the Telegram protocol.
For more information regarding this Trojan, refer to this news article.
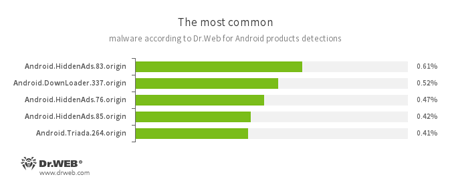
According to statistics collected by Dr.Web for Android
- Android.HiddenAds.83.origin
- Android.HiddenAds.76.origin
- Android.HiddenAds.85.origin
- Trojans designed to display unwanted ads on mobile devices. They are distributed under the guise of popular apps by other malicious programs that sometimes covertly install them in the system directory.
- Android.DownLoader.337.origin
- A Trojan designed to download other applications.
- Android.Triada.264.origin
- A multi-component Trojan that performs different malicious functions.
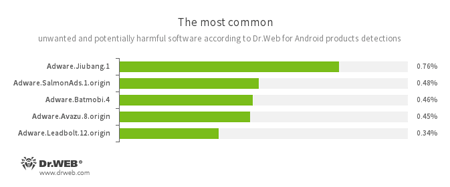
According to statistics collected by Dr.Web for Android
- Adware.Jiubang.1
- Adware.SalmonAds.1.origin
- Adware.Batmobi.4
- Adware.Avazu.8.origin
- Adware.Leadbolt.12.origin
- Unwanted program modules that are incorporated into Android applications and are designed to display annoying ads on mobile devices.
Threats on Google Play
In the past month, Doctor Web specialists detected riskware on Google Play that allowed users to access the social networking sites “VK” and “Odnoklassniki” which have been blocked in Ukraine. These applications, added to the Dr.Web virus database as Program.PWS.1, used an anonymizing server to bypass access restrictions and didn’t encrypt login, password and other confidential user information. For more information about this incident, refer to this news article published by Doctor Web.
Also in June, Trojans from the Android.Dvmap family were detected on Google Play. Once launched, these malicious programs try to get root privileges on mobile devices. If successful, they infect some system libraries and install additional components. These Trojans can execute commands of cybercriminals and also download and run other applications without any user involvement.
Other Android Trojans distributed via Google Play in June were added to the Dr.Web virus database as Android.SmsSend.1907.origin and Android.SmsSend.1908.origin. Cybercriminals injected them into benign programs. These malicious applications sent SMS messages to premium numbers, thus subscribing service provider customers to chargeable services. After that, the Trojans started deleting all incoming messages so users wouldn’t receive notifications informing them that they had successfully been subscribed to unwanted premium services.
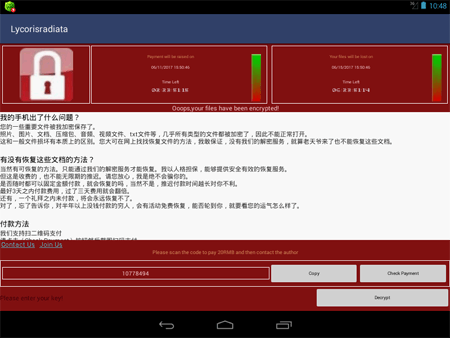
A ransomware Trojan
In June, the ransomware Trojan Android.Encoder.3.origin was detected. It attacked Chinese Android users and encrypted files on SD cards. The authors of this encoder were inspired by the encryption ransomware WannaCry, which infected hundreds of thousands of computers throughout the world in May 2017. The virus writers created ransom demand messages in a similar style.
Cybercriminals demanded a ransom of 20 yuan, and every three days the amount doubled. If the cybercriminals didn’t get their ransom within one week after Android.Encoder.3.origin infected a mobile device, the ransomware would delete the encrypted files.
Malicious programs and riskware for Android infect mobile devices not only via downloads from various websites but also via downloads from Google Play. Doctor Web recommends that device owners be cautious when installing unknown applications and install and use Dr.Web for Android.
Your Android needs protection
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 100 million downloads on Google Play alone
- Free for users of Dr.Web home products