April 2017 mobile malware review from Doctor Web
April 2017 mobile malware review from Doctor Web
[% DEFAULT FILE_REVIEW = ''; NAME_SOME_ARRAY_IN_MACROSNAME = [ { box => "Overview" }, { box => "Threat of the month" }, { box => "Statistics" } ] #FILE_REVIEW = ‘https://st.drweb.com/static/new-www/news/2017/_mob_review_april_2017_en.pdf' %] [% BLOCK global.tpl_blueprint.content %]April 28, 2017
In April an Android Trojan designed to engage in cyber espionage was detected. Also several new banking Trojans that were created to steal confidential information and account funds were detected on Google Play. One Trojan was embedded in programs for watching videos on the Internet; another was a flashlight program.
Principal Trends In April
- The detection of a spyware Trojan for Android
- The injection of banking Trojans into Google Play
Mobile threat of the month
In April an Android Trojan designed to engage in cyber espionage was detected. Android.Chrysaor.1.origin was detected; cybercriminals used it for spying purposes. This malicious program stole correspondence from a myriad of online communication programs, such as Skype, Viber, WhatsApp and others; it stole the web browser history, SMS messages, and other confidential data. Moreover, it tracked the operation of mobile device keyboards and intercepted all input information, made screenshots and eavesdropped on the environment via covert responses to calls made by cybercriminals.
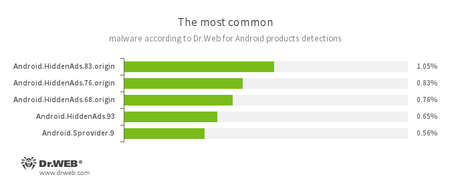
According to statistics collected by Dr.Web for Android
-
- Android.HiddenAds.83.origin
- Android.HiddenAds.76.origin
- Android.HiddenAds.68.origin
- Android.HiddenAds.93
- Trojans designed to display unwanted ads on mobile devices. They are distributed under the guise of popular apps by other malicious programs that, in some instances, covertly install them in the system directory.
- Android.Sprovider.9
- A Trojan for Android that is designed to display advertisements in the status bar and download and install other applications including malicious ones.
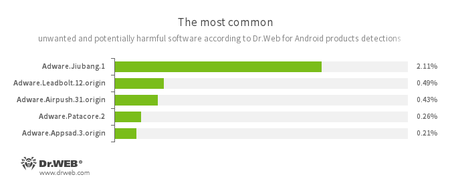
-
- Adware.Jiubang.1
- Adware.Leadbolt.12.origin
- Adware.Airpush.31.origin
- Adware.Patacore.2
- Adware.Appsad.3.origin
- Unwanted program modules that are incorporated into Android applications and are designed to display annoying ads on mobile devices.
Banking Trojans
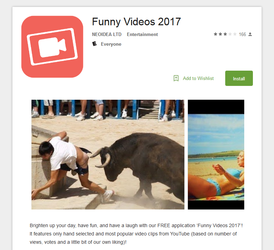
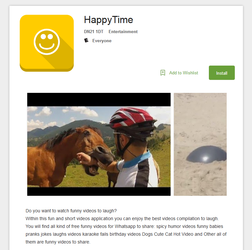
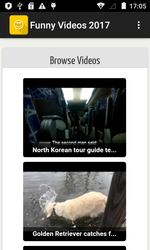
In April, several new banking Trojans for Android were detected on Google Play. One of them was added to the Dr.Web virus database as Android.BankBot.179.origin. It was hidden in the applications Funny Videos 2017 and HappyTime, which show comic videos. This Trojan is a modified version of another Android banker which was described by Doctor Web in this article. It is based on source codes published by cybercriminals and made openly accessible.
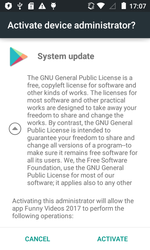
Android.BankBot.179.origin receives from the command and control server a configuration file with a list of banking and other software programs so that it can track their operation. After any of the listed programs is launched, the Trojan displays a fake authorization window for entering login and password information. If a user launches Google Play, Android.BankBot.179.origin displays a fraudulent service payment form and requests bank card details. In addition, this Trojan tracks incoming SMS messages and intercepts incoming confirmation codes.
Features of Android.BankBot.179.origin:
- Created on the basis of banking Trojan source code published online by cybercriminals;
- Distributed via Google Play;
- Embedded into a fully functional video player;
- Requests administrative privileges to make its removal from the system difficult;
- Can attack hundreds of banking programs and other popular software—cybercriminals just have to update the configuration file.
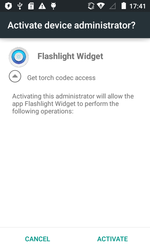
Another Android banker detected in April was dubbed Android.BankBot.180.origin. It was embedded in the flashlight application Flashlight LED Widget. Once launched, this Trojan deletes its icon from the home screen and requests administrator privileges on the mobile device. After that the flashlight’s operation is controlled via the malicious program’s widget.
Android.BankBot.180.origin tracks the launch of banking programs and displays a fake window over them for login and password input. Similar to Android.BankBot.179.origin, this malicious application tries to steal bank card details from the user by displaying a fraudulent form when Google Play is launched.
Android bankers are among the most dangerous malicious programs because they help cybercriminals steal money from accounts. Even greater danger is posed by banking Trojans distributed via Google Play. This catalog is considered to be the most reliable source of software for Android mobile devices so smartphone and tablet owners are less cautious when downloading applications from it. To protect your mobile device from banking Trojans and other malicious programs, we recommend that you install Dr.Web for Android.