April 2017 virus activity review from Doctor Web
April 28, 2017
April proved to be quite busy in terms of information security events. At the beginning of the month, cybercriminals arranged for a malicious mailing that was used to spread a multi-component Trojan. It is designed to steal confidential information from infected computers. In mid-April, Doctor Web’s specialists examined a fraudulent scheme involving a malicious program being used by cybercriminals to trick users. At the end of the month, a vulnerability in Microsoft Office was detected; it was used to spread a Trojan that steals passwords from infected computers.
Principal Trends in April
- The distribution of a malicious mailing containing a multi-component Trojan
- The detection of a vulnerability in Microsoft Office
- The distribution of new Trojans for Windows
Threat of the month
A multi-component Trojan, dubbed Trojan.MulDrop7.24844, was spread as an archived email attachment.
This archive contains a packed container that was created using the capabilities of the Autoit language. One of the components launched by Trojan.MulDrop7.24844 on infected computers is an application for remote administration. Dr.Web Anti-virus detects it as Program.RemoteAdmin.753. In addition, the Trojan saves two other applications on a disk. These programs are 32-bit and 64-bit versions of the Mimikatz tool. It is designed to intercept the passwords of open Windows sessions. Trojan.MulDrop7.24844 activates a keylogger that records to the file any information about the keys pressed by a user. It also performs several other functions defined by a parameter that is set at the moment of launch. The Trojan gives criminals access via RDP (Remote Desktop Protocol), allowing them to control the infected computer. More information about this malicious program can be found in the corresponding review published by Doctor Web.
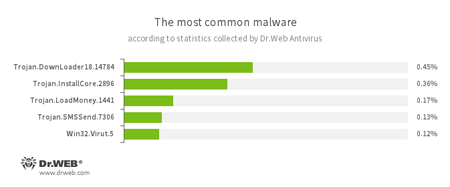
According to Dr.Web Anti-virus statistics
- Trojan.DownLoader
A family of malicious programs designed to download other malware to the compromised computer. - Trojan.InstallCore
A family of installers of unwanted and malicious applications. - Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on the victim's computer. - Trojan.SMSSend.7306
A representative of a family of malicious programs that take the form of an archive with an embedded installer. The malware prompts the user to either send a message to a short premium service number in order to proceed with the installation and gain access to the contents of the archive, or indicate a phone number and enter a code received in an incoming message, thus confirming their agreement to the terms of a paid subscription. The main “specialization” of Trojan.SMSSend is ransom. - Win32.Virut.5
A complex polymorphic virus that infects executable files and contains functions that allow infected computers to be controlled remotely.
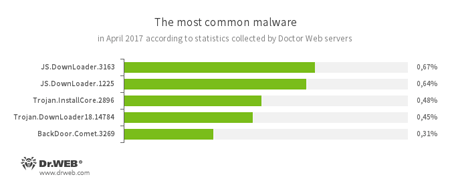
According to Doctor Web’s statistics servers
- JS.DownLoader
A family of malicious JavaScripts. Download and install malicious software. - Trojan.InstallCore
A family of installers of unwanted and malicious applications. - Trojan.DownLoader
A family of malicious programs designed to download other malware to the compromised computer. - BackDoor.Comet.3269
A representative of the malware family that executes commands received from cybercriminals on an infected device and provides them with unauthorized access to it.
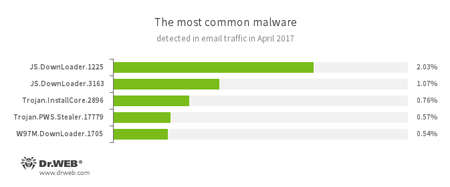
Statistics concerning malicious programs discovered in email traffic
- JS.DownLoader
A family of malicious JavaScripts. Download and install malicious software. - Trojan.InstallCore
A family of installers of unwanted and malicious applications. - Trojan.PWS.Stealer
A family of Trojans designed to steal passwords and other confidential information stored on an infected computer. - W97M.DownLoader
A family of downloader Trojans that exploit vulnerabilities in office applications. Designed for downloading other malware to a compromised computer.
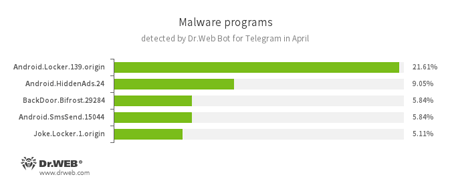
According to Dr.Web Bot for Telegram data
- Android.Locker.139.origin
A ransomware Trojan for Android. It can lock a device after alleging via an on-screen warning that the device owner has done something illegal. To unlock the device, the owner has to pay a ransom. - Android.HiddenAds.24
A Trojan designed to display unwanted ads on mobile devices. - BackDoor.Bifrost.29284
A backdoor Trojan that executes commands received from cybercriminals. - Android.SmsSend.15044
A Trojan belonging to the family of malicious programs that are designed to send SMS messages to premium numbers and subscribe users to chargeable services and services providing paid content. - Joke.Locker.1.origin
A joke program for Android that blocks a mobile device’s screen and displays the Windows BSOD (“Blue Screen of Death”).
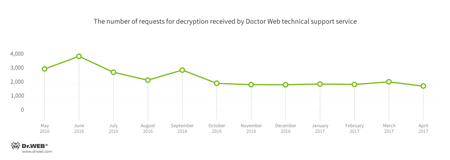
In April, cases involving the following ransomware modifications were registered by Doctor Web’s technical support service:
- Trojan.Encoder.858 — 33.57% requests;
- Trojan.Encoder.3953 — 8.97% requests;
- Trojan.Encoder.567 — 3.80% requests;
- Trojan.Encoder.10144 — 3.59% requests;
- Trojan.Encoder.761 — 2.58% requests.
Dr.Web Security Space 11.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows.
| Data Loss Prevention | |
|---|---|
 |  |
During April 2017, Doctor Web added 568,903 URLs into the Dr.Web database of non-recommended sites.
| March 2017 | April 2017 | Dynamics |
| + 223,173 | + 568,903 | + 154.91% |
In mid-April, Doctor Web described a fraudulent scheme that has been used for some time by cybercriminals who are engaged in “fixing matches”.
Usually cybercriminals sell unreliable information about the results of upcoming sports events. This information is supposed to be used for sure-win bets at bookmaker's offices. Now cybercriminals are offering their potential victims the opportunity to download a password-protected, self-unpacking RAR archive that supposedly contains a text file with the match results of an event. Cybercriminals send the password for this archive after the match is finished—that way the victim can be sure the forecast is valid. However, instead of the archive, the cybercriminals send their victims their own program, one that fully imitates the interface and behaviour of an SFX archive created with WinRAR. This fake “archive” contains the template of a text file that, with the help of a special algorithm, inserts the required match results which depend on what password is entered by the user. This program has been added to the Dr.Web virus databases under the name Trojan.Fraudster.2986, and the websites that have distributed it have been added to the list of non-recommended websites.
Find out more about Dr. Web non-recommended sitesOther information security events
At the end of April, a malicious program dubbed Trojan.DownLoader23.60762 was being distributed. It is designed to steal passwords from popular browsers and download different files without authorization. On the computer it has infected, the Trojan injects itself in browsers and intercepts the functions responsible for working with the network. It can execute the following commands:
- Launch a file from the temporary folder on the disk of the infected computer;
- Self inject in a running process;
- Delete the specified file;
- Launch the specified executable file;
- Save the SQLite database used by Google Chrome and send it to the cybercriminals;
- Change the command and control server to the one specified;
- Delete cookies;
- Restart the operating system;
- Turn off the computer.
More information about this malicious program can be found in the review published by Doctor Web.
Also in April, a vulnerability was found in the Microsoft Office Word text editor. Cybercriminals created the exploit Exploit.Ole2link.1 to take advantage of this vulnerability. This exploit is implemented as a Microsoft Word document with the DOCX extension. Once this document is opened, another file called doc.doc is loaded. It contains an embedded HTA script, detected by Dr.Web as PowerShell.DownLoader.72. This HTA script, written using Windows Script syntax, calls the command interpreter PowerShell. PowerShell processes another malicious script that downloads an executable file to the attacked computer. For more information regarding this vulnerability, refer to the following article.
Linux malware
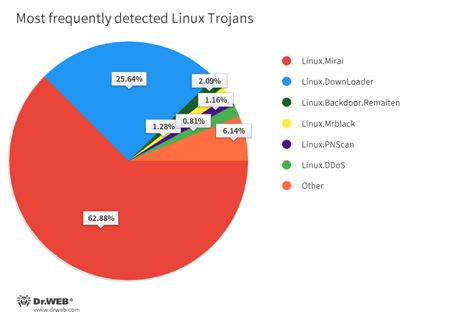
During the course of April, Doctor Web’s specialists registered 1,317,388 attacks on different Linux devices—147,401 of them were performed over the SSH protocol and 1,169,987 of them over the Telnet protocol. The below diagram shows the proportional relationship between the most frequently detected Linux Trojans:
- Linux.Mirai
Linux Trojan designed to carry out DDoS attacks. The Trojan can disable the watchdog timer, which prevents system hangs, to make it impossible to reboot the computer. - Linux.DownLoader
A family of malicious programs and scripts for Linux that are designed to download and install other malware applications on infected computers. - Linux.BackDoor.Remaiten
A family of Linux Trojans designed to carry out DDoS attacks. Trojans from this family can hack devices using the Telnet protocol via a brute force attack. If successful, it saves a loader written in Assembler to the computer. The loader downloads and installs other Trojans on the attacked device. - Linux.Mrblack
A Trojan designed to carry out DDoS attacks that is geared toward working with Linux distributions for ARM processors. The Trojan has an embedded command handler that allows it to execute instructions received from the C&C server. - Linux.DDoS
Linux malware. Designed to carry out DDoS attacks. - Linux.PNScan
A family of network worms designed to infect Linux routers. The worm can infect devices by itself, open ports 9000 and 1337, process requests received over these ports, and connect to a C&C server.
In April Doctor Web’s specialists examined an updated version of a malicious program from the Linux.UbntFM family. The program was dubbed Linux.UbntFM.2. Cybercriminals developed this Trojan for Linux operating systems, including Air OS, which Ubiquiti Networks produces and installs on its devices. It is implemented as bash scripts distributed in the archive tgz.
Linux.UbntFM.2 creates new accounts on the infected device and downloads and launches arbitrary files. Moreover, the Trojan can attack remote devices using a vulnerability in the web interface of Air OS, which allows it to download an arbitrary file through an arbitrary path without authorization. If the Trojan cannot define the protocol (or Air OS is not installed on the infected device), it can attempt to generate account details for the SSH connection using a special dictionary and the logins “root”, “admin”, and “ubnt” and the passwords stored in the “passlst” file. Details on this malicious program’s operating routines can be found in the technical description.
In addition, in April, a new version of a Trojan from the Fgt family was detected — Linux.BackDoor.Fgt.645. This modification of a malware program is distinguished from the previous one by a limited range of functions (only the module for cracking passwords to hack into remote network servers and the dropper remain); the new version can also send a request to download and launch an .sh script.
Malicious and unwanted programs for mobile devices
In April, the new spy Trojan Android.Chrysaor.1.origin was added to the Dr.Web virus database. Cybercriminals could use it for targeted attacks to steal confidential information from Android device users. In April, several new banking Trojans were detected on Google Play. One of them was given the name Android.BankBot.179.origin. It was distributed in the guise of programs that offer online videos, and in reality the programs actually did just that. Another Android banking Trojan found on Google Play was added to the virus database as Android.BankBot.180.origin. This Trojan presented itself as a flashlight program.
Among the most noticeable April events related to mobile malware, we can mention:
- The detection of an Android Trojan designed to engage in cyber espionage;
- The detection of banking Trojans on Google Play that stole confidential information and funds from Android users.
Find out more about malicious and unwanted programs for mobile devices in our special overview.