Doctor Web’s annual virus activity review
December 29, 2016
The past year was quite eventful in terms of information security. It was marked by a considerable growth of Linux Trojans, which happened due to wide spread of various Linux devices such as routers, network storages, IP cameras with a web interface, and others. Users often connect them to the Internet without changing their default settings—therefore, it allows virus makers to hack these devices by obtaining a password via a brute force attack and install Trojans on them.
In spring 2016, Doctor Web’s specialists found the first ransomware Trojan for macOS (OS X) and developed a decryption technique for files compromised by this Trojan.
In addition, the year 2016 is remembered by the detection of several malware programs targeted the 1C accounting software popular in Russia. Among them, there was discovered the first full-featured Trojan written in the Russian language—in fact, in the incorporated 1C language—which launched a ransomware program. Another Trojan was specially created for well-known accounting applications and mail clients. Apart from the non-standard 1C language, virus makers also contrived Trojans, using the languages Rust and Go.
Yet another Trojan that performed targeted attacks cannot be omitted—it infected computers belonging to several Russian companies producing construction cranes.
During the year, a large number of new banking Trojans including those capable of creating decentralized botnets and selectively infecting machines belonging to residents of different world regions.
Trojans for Android found in 2016 could infiltrate system libraries and running processes. During the part 12 months, Doctor Web’s specialists regularly discovered malware programs preinstalled in the firmware of Android smartphones and tablets. In addition, such Trojans were also detected in the Google Play store.
PRINCIPAL TRENDS OF THE YEAR
- The number of Linux Trojan has increased.
- The first ransomware Trojan for macOS (OS X) was discovered.
- Trojans written in uncommon programming languages were widely spread.
- Trojans for Android capable of infecting system processes and libraries were found.
Most notable events of 2016
In 2016, banking Trojans still posed a serious threat to bank customers. Among them, there are not only simple Trojans, like Trojan.Proxy2.102, but also sophisticated ones—for example, Trojan.Gozi. This malware, which runs on 32- and 64-bit Windows, is able to carry out a wide range of malicious activities. Thus, it can steal information entered by the user into web data forms and perform web injections and keylogging functions. In addition, the Trojan is also designed to get remote access to the user’s machine. Moreover, upon a command, the Trojan can run the SOCKS proxy server, download and install various plug-ins, and steal information used for accessing online banking services.
Trojan.Gozi can join infected computers into botnets. Trojan.Gozi downloads a text file from the NASA server, used as a glossary, so that the malware can then generate domain names of its control servers. In addition, it can create P2P botnets.
However, the most dangerous Trojan of 2016 is a polymorphic banking Trojan—Bolik—that is a successor of such well-known malware programs as Zeus and Carberp. Unlike them, Bolik can be distributed without user interference and infect executable files.
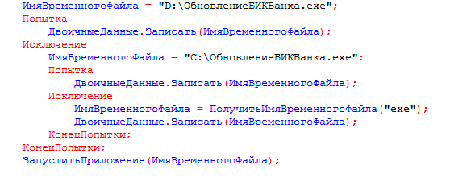
Virus makers rarely use non-standard and rare methods when contriving malware programs. 1C.Drop.1 is one of such Trojans because it was written in the incorporated 1C language, and its code contains Cyrillic characters.
The Trojan was distributed via an email that contains an external data processor for 1C:Enterprise. If the user opened the file in 1C:Enterprise, 1C.Drop.1 sent out its copy to all contractors whose email addresses were specified in the database. Then it retrieved a ransomware program, saved it on disk and runs the ransomware Trojan.
In addition, in 2016, Doctor Web’s specialists examined the backdoor Linux.BackDoor.Irc.16 written in Rust whose first stable version was registered in 2015. In October, they found the encryption Trojan Trojan.Encoder.6491, written in the Go language, and promptly developed a decryption method for compromised files. The Go language became rather popular among cybercriminals—soon after that, Doctor Web’s analysts found yet another Trojan written in the Go language for Linux machines, which was subsequently named Linux.Lady.1. It was is designed to download and run cryptocurrency mining software on a computer and to attack other devices.
Among especially dangerous Trojan, we can mention a category of so called fileless malware programs. Their key feature lies in the fact that their payload is located not in a file but directly in the computer’s memory. Necessary files needed for their operation are stored in various containers—for example, the Windows system registry. In June 2016, Doctor Web’s specialists examined one of their representatives, named Trojan.Kovter.297, which was hidden in the Windows system registry and designed to show advertisements on the infected computer.
The most notable event of 2016 was the discovery of BackDoor.Crane.1, which was used to attack Russia’s manufacturers of construction cranes. This is one of the few cases involving malware being used to engage in targeted attacks that Doctor Web’s specialists have registered in the recent past. The backdoor Trojan and the two other malware programs it has been downloading on infected machines have been stealing confidential information for some time. The cybercriminals involved were interested in obtaining financial documentation, agreements, and internal business correspondence. In addition, these Trojans periodically made screenshots and sent them to the command and control (C&C) server. You can learn more about the Trojan’s operation in the review published by Doctor Web.
Malware landscape
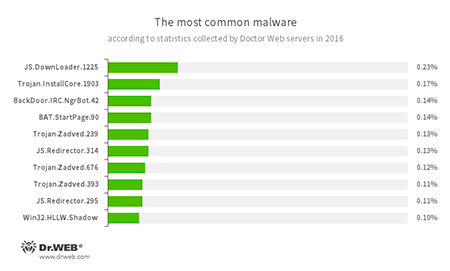
Statistics collected with Dr.Web servers shows that, in 2016, scripts and applications designed for covert download and installation of malware programs were the most frequently detected threats together with a large number of adware Trojans found on user computers.
- JS.DownLoader
A family of malicious scripts written in JavaScript and designed to download and install other malware programs on a computer. - Trojan.InstallCore
A Trojan family that can install unwanted and malicious applications. - BackDoor.IRC.NgrBot.42
A fairly common Trojan, which is known to information security researchers since 2011. Malicious programs of this family are able to execute intruder-issued commands on infected machine controlled by cybercriminals via the IRC (Internet Relay Chat) text-messaging protocol. - BAT.StartPage.90
A malware script that can modify the home page in the browser settings. - Trojan.Zadved
This Trojan displays fake search results in a browser window and imitates pop-up messages from social networking sites. In addition, the malware can replace advertisements displayed on different Internet resources. - JS.Redirector
A family of malicious scripts written in JavaScript and designed to automatically redirect users to other webpages. - Win32.HLLW.Shadow
A worm that replicates itself through removable media and network drives. In addition, it can be spread via a network using a standard SMB protocol. It is designed to download executable files from the C&C server and run them.
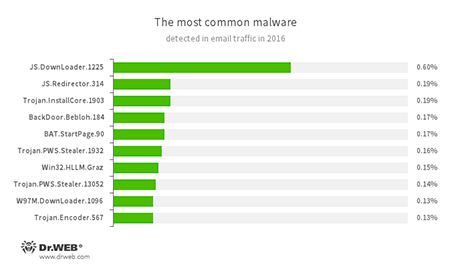
Statistics on email threats found in 2016 displays almost the same situation: downloader scripts and adware Trojans were the actively being spread via email traffic. Among dangerous attachments, we can mention spyware programs, encryption ransomware, backdoors, and programs designed to replace browser home pages. The histogram below shows top 10 common threats according to statistics collected by Dr.Web mail anti-virus:
- JS.DownLoader
A family of malicious scripts written in JavaScript and designed to download and install other malware programs on a computer. - JS.Redirector
A family of malicious scripts written in JavaScript and designed to automatically redirect users to other webpages. - Trojan.InstallCore
A Trojan family that can install unwanted and malicious applications. - BackDoor.Bebloh.184
A backdoor Trojan that is capable of performing injections into other applications and executing cybercriminals’ commands. - BAT.StartPage.90
A malware script that can modify the home page in the browser settings. - Trojan.PWS.Stealer
A family of Trojans designed to steal passwords and other confidential information stored on the infected computer. - Win32.HLLM.Graz
An worm that is distributed via mass mailing. It monitors traffic of the specified ports and parses transmitted data according to protocols for password retrieving. This data is then used to spread the worm. - W97M.DownLoader
A family of downloader Trojans that exploit vulnerabilities in office applications and can download other malicious programs to a compromised computer. - Trojan.Encoder.567
A ransomware Trojan that encrypts files and demands a ransom for decryption of compromised data. This program can encrypt files of the following types: .jpg, .jpeg, .doc, .docx, .xls, xlsx, .dbf, .1cd, .psd, .dwg, .xml, .zip, .rar, .db3, .pdf, .rtf, .7z, .kwm, .arj, .xlsm, .key, .cer, .accdb, .odt, .ppt, .mdb, .dt, .gsf, .ppsx, .pptx.
Encryption ransomware
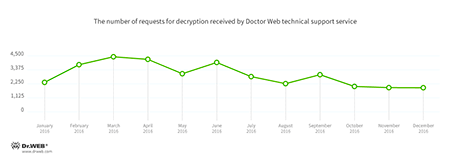
Like before, in 2016, encryption ransomware programs posed a serious threat to users. During the past year, Doctor Web technical support received over 34,000 tickets from users whose files were compromised by encoders. A peak of requests was registered in February, March, and April, and a singular spike—in July. By the end of the year, activity of ransomware Trojans had slowly decreased, which is illustrated on the diagram below.
According to the statistics, the most frequently detected ransomware Trojan was Trojan.Encoder.858; the second place went to Trojan.Encoder.761; and the third place—to Trojan.Encoder.3953.
The most common ransomware programs in 2016:
- Trojan.Encoder.858 — 23% of requests;
- Trojan.Encoder.761 — 17.44% of requests;
- Trojan.Encoder.3953 — 4.76% of requests;
- Trojan.Encoder.567 — 4.58% of requests;
- Trojan.Encoder.3976 — 4.26% of requests.
Encryption ransomware programs were found not only for Microsoft Windows but also for Linux—thus, in January, a new Linux encoder, dubbed Linux.Encoder.3 was discovered. A key feature of Linux.Encoder.3 lied in its capability to remember dates of files creation or modification that were then replaced with dates specified before the encryption. Compromised files were appended with the .encrypted extension.
In March, the first ransomware Trojan for Apple devices was discovered—Mac.Trojan.KeRanger.2. It was first detected in a compromised version of the installer for a popular macOS (OS X) torrent client that was distributed as a DMG file. The malicious application was signed with a valid Mac app development certificate. Thus, this program successfully bypassed Apple’s Gatekeeper protection.
Doctor Web’s specialists promptly developed decryption techniques for files compromised by both of those Trojans.
Dr.Web Security Space 11.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows
| Data Loss Prevention | |
|---|---|
 |  |
Linux
One of the most notable trends in 2016 is the spread of Linux Trojans targeting the Internet of Things, i.e. devices connected to the Web: routers, network storages, set-top boxes, IP cameras, and other smart devices. The main reason why virus makers are so interested in attacking the IoT is user carelessness because they often prefer not to change the default settings of the manufacturer. Therefore, attackers can easily get access to these gadgets by using standard login credentials and then upload malicious software.
As a rule, virus makers install three types of malware on Linux devices—Trojans which perform DDoS attacks, applications which allow to launch a proxy server in the system (it is used by attackers to stay anonymous), and Trojans and scripts designed to download other programs. To connect to the attacked devices, the protocols SSH and Telnet are used.
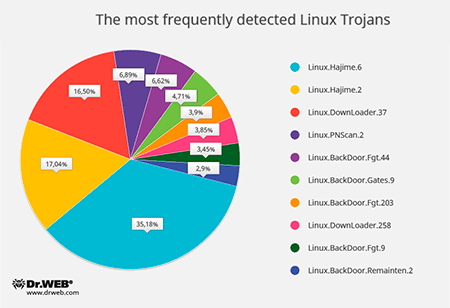
Since autumn 2016, Doctor Web’s specialists have started monitoring activity of such-like Linux Trojans by using a specially configured network nodes—so called honeypots. From month to month, the number of attacks on such nodes was continuously increasing: in October, 40,756 cases were registered; however, in November, their number was already 389,285. In addition, their proportion has changed: in October, 35,423 of attacks were performed over the SSH protocol and 5,333 of them over the Telnet protocol; however, in November, the situation dramatically changed: Doctor Web’s specialists registered that 79,447 of attacks were performed over the SSH protocol and 309,838 of them over the Telnet protocol. This can be explained by the popularity growth of Linux.Mirai whose source codes became publicly known. The first version of Linux.Mirai appeared in May 2016. This Trojan, designed to carry out DDoS attacks, can work with the SPARC, ARM, MIPS, SH-4, M68K architectures and Intel x86 computers. To attack invulnerable devices, the Trojan used the Telnet protocol. The round diagram below shows the proportional relationship between the most frequently detected Linux Trojans in autumn 2016:
- Linux.Hajime
A family of worms for Linux which are distributed over the Telnet protocol. After obtaining a password via a brute force attack and logging in successfully, a malicious module saves to the machine a loader for MIPS/ARM architectures that is written in the Assembler language. The loader downloads the Trojan’s main module which subsequently connects the computer to a decentralized P2P botnet. - Linux.DownLoader
A family of malicious programs and scripts for Linux designed to download and install other malware applications on an infected computer. - Linux.PNScan.2
A network worm designed to infect Linux routers. The worm can infect devices by itself, open ports 9000 and 1337, process requests received over these ports, and connect to a C&C server. - Linux.BackDoor.Fgt
A family of Trojans for Linux designed to carry out DDoS attacks. Numerous versions of Trojans exist for different Linux distributions, including for the MIPS and SPARC architectures. - Linux.BackDoor.Gates
A family of Linux Trojans that performs backdoor functions and carries out DDoS attacks. These Trojans also execute commands from cybercriminals. - Linux.BackDoor.Remaiten
A family of Linux Trojans designed to carry out DDoS attacks. The Trojan can hack a device by using the Telnet protocol and obtaining the password via a brute force attack. If successful, it saves a loader written in Assembler to the computer. The loader downloads and installs other Trojans.
Apart from the above-mentioned malware for IoT, Doctor Web’s specialists examined other threats intended to infect Linux computers. In January, they found Linux.Ekoms.1 capable of taking screen shots on the compromised machine and the multicomponent backdoor Linux.BackDoor.Xunpes.1. Soon after that, they registered the spread of a hacker utility, which infected a computer with a dangerous Trojan, the Linux.Rex.1 Trojan able to unite computers into botnets, and the backdoor Linux.BackDoor.FakeFile.1 that could perform commands received from the cybercriminals.
macOS
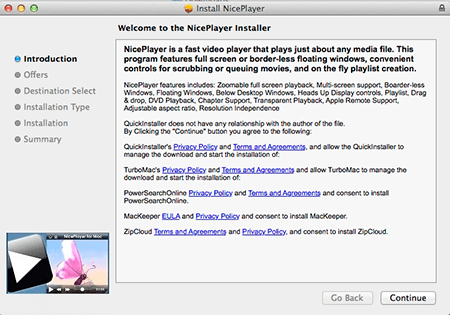
In 2016, Doctor Web security researchers detected a large number of new malware programs for Apple computers. Among them, there is the Mac.Trojan.VSearch Trojan family designed to display advertisements on the infected machine.
These Trojans are spread as various utilities—for example, as the Nice Player application. Users can download it from different websites offering free OS X software. One of the family representatives, Mac.Trojan.VSearch.2, installs several unwanted applications, among which—Mac.Trojan.VSearch.4. the Trojan downloads a script from the server. This script is used to set another default search engine. In addition, applying this script, Mac.Trojan.VSearch.4 can download and install a search plug-in for Safari, Google Chrome, and Mozilla Firefox together with the Trojan Mac.Trojan.VSearch.7. Once Mac.Trojan.VSearch.7 is on the computer, the very first thing it does is create a new user account, which is not displayed in the OS X Welcome dialog. Then it launches a special proxy server that is used to inject a JavaScript script in all opened webpages. This script is responsible for display of advertisements in the browser window and collects the user’s Web search queries of several search engines.
Doctor Web specialists found that 1,735,730 malicious programs were downloaded from the cybercriminals’ servers. In addition, they also registered 478,099 unique IP addresses that requested these servers.
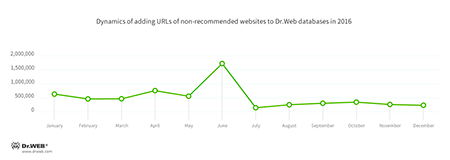
Dangerous and non-recommended sites
A large number of dangerous websites can harm not only computers but even users. Among them, there are phishing and fraudulent websites and sites which distribute malware programs. To protect the machine from such-like web resources, the Dr.Web anti-virus contains the modules SpIDer Gate and Parental Control, whose databases are regularly updated with new links to malicious and non-recommended websites. The dynamics of database update in 2016 is shown below:
Network fraud
In 2016, scammers continued taking advantage of gullible users. In April, Doctor Web specialists published a news article about fraudulent online stores that deceived their customers.
These scan stores provide a fast delivery of goods to any Russian region. The only one important condition is that a potential victim has to make a full prepayment. Having made the prepayment, the victim waits for a purchase confirmation. However, after some time, the website and the phone number become unavailable, and all messages sent by the scammed user to the contact email address are returned. In several days, the same shop with similar range of goods but with a different name and URL emerges on the Internet. You can read this review to learn how to distinguish a real online store from a fake one.
One more popular network fraud scheme was used by the creators of the program “Detector Millionaire”.
This website, and others alike, represent the binary option system—a scam scheme known since 2014. It is no doubt that network fraudsters will continue using illegal ways of money making, so users should be very cautious and attentive.
Mobile devices
In 2016, cybercriminals continued attacking users of mobile devices. During the past year, numerous malicious and unwanted applications were found. As before, the main part of Trojans was designed for Android devices; however, the iOS system also suffered from malicious attacks.
The main goal of virus makers is to illegally generate income. They use several methods for money making—one of them is to design Trojans which install unwanted applications and display advertisements. In 2015, attackers were spreading such Trojans which tried to get root privileges by installing software without user knowledge. In 2016, this trend remained but cybercriminals developed new techniques and non-standard solutions. Thus, the year began with the discovery of the Android.Loki Trojan family. Those Trojans were incorporated into application processes (including system ones) and could covertly download and install any software. In the end of 2016, Doctor Web’s specialists found a new version of this Trojan capable of infecting not only system processes but also libraries. As a result, the Trojan also could obtain the root privileges to be able to install various applications.
Some virus makers incorporate downloaders and adware Trojans directly into the firmware of a device—therefore, official producers have often no idea that they sell infected devices. Several such-like cases were registered in 2016. For example, Doctor Web published a news article about the Trojan Android.Cooee.1 discovered in the firmware of one of popular smartphones.
Android.Cooee.1 was incorporated in a graphical shell and was designed for showing advertisements. Moreover, it was able to download and run other applications, including malicious ones.
In March, the Trojan Android.Gmobi.1 was discovered. It was preinstalled on several models of mobile devices. Later, in November, yet another such like Trojan, Android.Spy.332.origin, was found. Both those malware applications downloaded and installed applications, and performed other malicious functions.
Apart from adware Trojans, virus writers implement advertising modules which are not relatively malicious. In the past year, such modules took the first place in the statistics of potentially dangerous programs found on mobile devices by Dr.Web for Android.
Another popular money making method actively used by cybercriminals is creation of banking Trojans for Android devices. The number of cases involving banking Trojans has increased by 138% this year, comparing to 2015.
One of such Trojans was Android.SmsSpy.88.origin. It was known to Doctor Web security researchers since 2014. Its authors regularly improve its architecture so that now they can infect Android devices all over the world. Android.SmsSpy.88.origin tracks launch of dozens of applications. Upon detecting a launch, the Trojan downloaded a phishing input form from the server and displayed it on top of the running application. In fact, Android.SmsSpy.88.origin can attack a customer of any bank—virus makers should only generate an appropriate phishing form and load it to the command and control server.
Doctor Web specialists registered that since the beginning of 2016, the Trojan managed to infect about 40,000 mobile devices belonging to residents of more that 200 countries. For more details about this Trojan, refer to the news article.
The next Android banking Trojan detected in 2016 was named Android.BankBot.104.origin. It covertly checked balance of bank accounts and, if it detected available funds, the Trojan covertly transferred the money to cybercriminals’ bank accounts.
Ransomware Trojans belonging to the Android.Locker family are still posing a serious threat to Android users. They block devices demanding a ransom to unlock them. More dangerous versions can encrypt all available files including photos, documents, videos, music, and so on. The ransom is often exceeds several hundreds of dollars. In 2016, virus makers continued spreading these Trojans; however, a spike in their distribution was at the beginning of the year. During 2016, Dr.Web for Android products detected more than 540,000 cases involving Trojans of this family.
A large number of Trojans were found in the Google Play store during 2016. In March, Doctor Web specialists found the malware program Android.Spy.277.origin that displayed advertisements and scared users that the device’s battery is damaged. To repair the battery, the user was prompted to install some application. A similar Trojan, dubbed Android.Click.95, was discovered in April. Android.Click.95 checked whether an application specified by the Trojan was on the device. If the application was missing, Android.Click.95 opened a fraudulent website which prompted the user to choose another browser because the current one was allegedly not safe to use, or the Trojan showed another fake warning, for example, about battery malfunction. To solve those problems, the user was then prompted to install some application.
In June, the Trojan Android.PWS.Vk.3 was also discovered in Google Play. It allowed to listen to VK music by stealing user login credentials for their profiles and sent them to cybercriminals. Later that month, news about Android.Valeriy.1.origin were published by Doctor Web. This Trojan was able to load dubious websites and display them as advertisements in order to get users’ mobile phone number and subscribe them to chargeable services. Then a certain subscription fee was written off from the user’s mobile account every day. Android.Valeriy.1.origin intercepted and blocked all incoming confirmation messages. As a result, the victim did not have any idea that they were subscribed to some services. In addition, the Trojan could tap on advertisements, open links, and download unwanted applications including malicious ones.
In July, one more Trojan was found in Google Play—Android.Spy.305.origin. Its main goal was to show annoying advertisements. Another Trojan discovered in the same app store was Android.SockBot.1. Once installed, Android.SockBot.1 covertly connected to the Internet and transformed a mobile device into a proxy server. This technique helped cybercriminals anonymously connect to remote computers and other machines that had an Internet connection. In addition, they could intercept and redirect network traffic, steal private information, and perform DDoS attacks on web servers. November was marked by the discovery of Android.MulDrop.924. Part of its functionality was located in two auxiliary modules, which were encrypted and hidden inside a PNG image in the resource catalog of Android.MulDrop.924. One of those components not only performed benign functions but also contained several advertising plug-ins used by the Trojan’s authors to generate income. The malicious module Android.DownLoader.451.origin was one of them—it covertly downloaded applications and invited users to install them. In addition, it could display advertisements on the status bar of a device.
In 2016, iOS users also suffered from cybercriminals’ attacks. In February, the potentially dangerous program Program.IPhoneOS.Unwanted.ZergHelper found in App Store was added to the Dr.Web virus database. That program allowed users to download software including hacked versions of paid applications and programs which were not verified by Apple. In addition, it downloaded updates bypassing the App Store and requested user Apple ID and a password. In March, IPhoneOS.AceDeciever.6, which also asked a user for their password and Apple ID, was discovered. The Trojan was automatically installed on mobile devices after they were connected via a USB cable to computers running Windows which already had the application named 爱思助手 installed in the system. That application was spread as analog to iTunes and was added to the Dr.Web virus database as the Trojan Trojan.AceDeciever.2.
Prospects and possible trends
The analysis of malware landscape allows to make some forecasts about the future information security situation. First, it is likely that the number of Linux Trojans that infect the Internet of Things will increase. It can be also assumed that the number of attacks using either the protocols Telnet and SSH or currently known malware programs will also grow. New functions will be developed and added to the functionality of these Trojans. Consequently, DDoS attacks on various network servers and IT infrastructure of separate web resources will be more intense and performed more often than in 2016.
Encryption ransomware is still considered the most dangerous threat because it can attack not only windows users but also computers and devices running Linux, Android и macOS. Probably, its encryption algorithms will become more complicated, and the number of such Trojans will increase considerably.
The third trend of 2017 is a possible growth of the total number of Android Trojans—especially banking Trojans—and their new versions. It is common knowledge that online banking services are very popular among users due to their convenience. Thus, they are quite attractive for cybercriminals who strive to generate income using every possible illegal method. In spite the fact that Google is trying to protect the Android system against malware attacks, this system is still vulnerable to numerous Trojans.
The distribution methods will be also improved. Even now, we can see the growth in number of mass mailings using various scripts that install Trojans on system. These scripts are written in different script languages—in particular, JavaScript. Among email attachments, there are often files that use known vulnerabilities in office applications. It is no doubt that the range of infection methods implemented by virus makers will being extended during 2017.