Doctor Web’s November 2016 virus activity review
November 30, 2016
November was quite eventful in terms of information security. Doctor Web’s specialists found a botnet targeting Russian banks and a Trojan carrying out targeted attacks on companies producing construction cranes. In addition, more than one million users downloaded a malware program embedded in a Google Play application.
PRINCIPAL TRENDS IN NOVEMBER
- The emergence of a botnet attacking Russian banks
- A targeted attack on companies producing construction cranes
- The detection of an Android Trojan on Google Play
Threat of the month
Malicious programs for specialty or so-called targeted attacks are detected quite rarely. In 2011, Doctor Web published a news article about the Trojan BackDoor.Dande, which was designed to steal information from drugstores and pharmaceutical companies. Four years later, Doctor Web specialists found BackDoor.Hser.1, which was intended for use against defense companies. Later that month, they discovered a new backdoor—BackDoor.Crane.1— that stole important documentation and internal business correspondence from computers belonging to Russian companies engaged in the production of construction cranes. In addition, these Trojans periodically made screenshots and sent them to the command and control (C&C) server.
Doctor Web’s specialists have surmised that the authors of BackDoor.Crane.1 took part of the code from various sources—in particular, from the website rsdn.org. This is evidenced by the “RSDN HTTP Reader” value of the User-Agent parameter used by the Trojan when accessing web resources, and by the invisible window “About the Bot project” which appears to have been overlooked in its resources.
BackDoor.Crane.1 has several modules. Each of them is responsible for performing one particular function:
- A received command can be executed using the command interpreter cmd;
- A file can be downloaded from a specified link and saved to a certain folder on a computer;
- A list of folder content can be generated and sent to the C&C server;
- A screenshot can be taken and sent to the C&C server;
- A file can be loaded to a specified server over the FTP protocol;
- A file can be loaded to a specified server over the HTTP protocol.
In addition, the backdoor can download and run two other Trojans written in Python—Python.BackDoor.Crane.1 and Python.BackDoor.Crane.2. To learn more about these malicious programs, please refer to our previously published review.
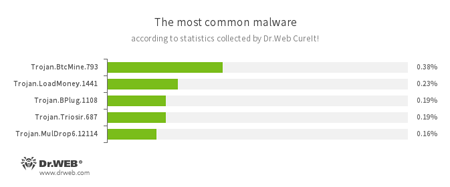
According to statistics collected by Dr.Web CureIt!
- Trojan.BtcMine.793
A Trojan designed to covertly use an infected computer’s resources in order to generate cryptocurrency—for example, Bitcoin. - Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on a victim’s computer. - Trojan.BPlug
These plug-ins for popular browsers display annoying advertisements to users browsing webpages. - Trojan.Triosir.687
A plug-in for web browsers that is designed to display annoying advertisements to users as they browse webpages. - Trojan.MulDrop6.12114
А Trojan that can install other malicious programs on a computer.
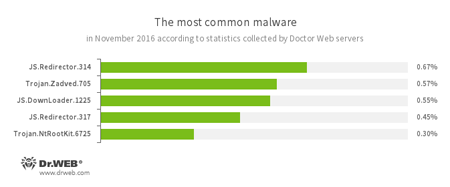
According to Doctor Web’s statistics servers
- JS.Redirector
A family of malicious scripts written in JavaScript and designed to automatically redirect users to other webpages. - Trojan.Zadved
This Trojan displays fake search results in a browser window and imitates pop-up messages from social networking sites. In addition, the malware can replace advertisements displayed on different Internet resources. - JS.DownLoader
A family of malicious scripts written in JavaScript and designed to download and install other malware programs on a computer. - Trojan.NtRootKit.6725
A rootkit Trojan that hides itself in the infected system. To execute its malicious functions, the Trojan injects its code into other running processes.
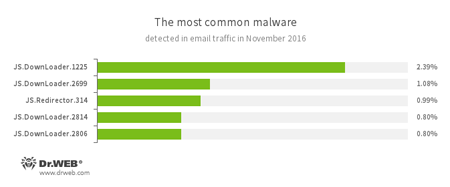
Statistics on malicious programs discovered in email traffic
- JS.DownLoader
A family of malicious scripts written in JavaScript and designed to download and install other malware programs on a computer. - JS.Redirector
A family of malicious scripts written in JavaScript and designed to automatically redirect users to other webpages.
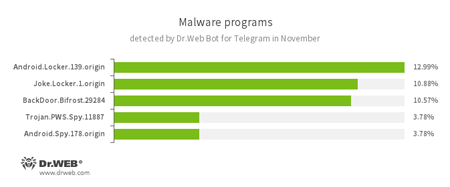
According to statistics collected by Dr.Web Bot for Telegram
- Android.Locker.139.origin
A ransomware Trojan for Android. Its different modifications can lock a device after displaying a warning to the device’s owner that they have done something illegal. To unlock the device, the owner has to pay a ransom. - Joke.Locker.1.origin
A joke program for Android that locks the home screen of a device and displays a Microsoft Windows BSOD (Blue Screen of Death) error. - BackDoor.Bifrost.29284
A backdoor Trojan that executes commands received from cybercriminals. - Trojan.PWS.Spy.11887
A Trojan for Windows that steals private information including user passwords. - Android.Spy
A family of multifunctional Trojans for Android that are designed to read and save contacts, receive and send SMS messages, determine GPS coordinates, read and save bookmarks in a browser, and get a device’s IMEI and telephone number.
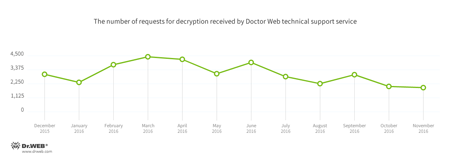
Encryption ransomware
In November, cases involving the following ransomware modifications were registered by Doctor Web’s technical support service:
- Trojan.Encoder.858 — 16.97% of requests
- Trojan.Encoder.761 — 14.54% of requests
- Trojan.Encoder.3953 — 5.55% of requests
- Trojan.Encoder.3976 — 3.79% of requests
- Trojan.Encoder.567 — 1.50% of requests
Dr.Web Security Space 11.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows
| Data Loss Prevention | |
|---|---|
 |  |
Dangerous websites
During November 2016, the URLs of 254,736 non-recommended websites were added to the Dr.Web database.
| October 2016 | November 2016 | Dynamics |
|---|---|---|
| +338,670 | +254,736 | -24.78% |
Some web resources are not actually fraudulent; however, they are made to resemble official government websites. They deceive users by implementing methods similar to those used by fraudsters who create phishing webpages. The owners of these sites are commercial organizations that have stooped to engaging in dishonest advertising.
Non-recommended websitesLinux
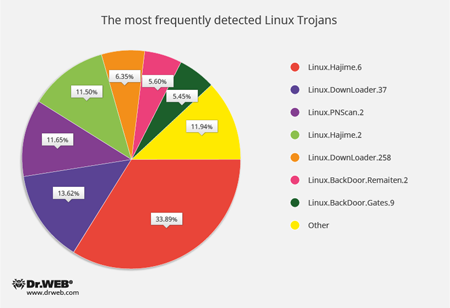
Since the beginning of November, Doctor Web’s specialists have registered 389,285 attacks by Linux Trojans—79,447 of them were performed over the SSH protocol and 309,838 of them over the Telnet protocol. The below diagram shows the proportional relationship between the most frequently detected Linux Trojans:
- Linux.Hajime
A family of worms for Linux which are distributed over the Telnet protocol. After obtaining a password via a brute force attack and logging in successfully, a malicious module saves to the machine a loader for MIPS/ARM architectures that is written in the Assembler language. The loader downloads the Trojan’s main module which subsequently connects the computer to a decentralized P2P botnet. - Linux.DownLoader
A family of malicious programs and scripts for Linux designed to download and install other malware applications on an infected computer. - Linux.PNScan.2
A network worm designed to infect Linux routers. The worm can infect devices by itself, open ports 9000 and 1337, process requests received over these ports, and connect to a C&C server. - Linux.BackDoor.Remaiten
A family of Linux Trojans designed to carry out DDoS attacks. The Trojan can hack a device by using the Telnet protocol and obtaining the password via a brute force attack. If successful, it saves a loader written in Assembler to the computer. The loader downloads and installs other Trojans. - Linux.BackDoor.Gates
A family of Linux Trojans that performs backdoor functions and carries out DDoS attacks. These Trojans also execute commands from cybercriminals.
Other threats
In November, Doctor Web’s security researchers discovered a botnet designed to carry out DDoS attacks. Its creators used the Trojan BackDoor.IRC.Medusa.1—a malicious IRC bot. While linked to a particular chat channel, the Trojan received commands over the IRC (Internet Relay Chat) protocol.
BackDoor.IRC.Medusa.1 performs several types of DDoS attacks and, when commanded by cybercriminals, downloads and runs executable files. Doctor Web’s specialists believe that this Trojan was involved in mass attacks on servers belonging to Sberbank of Russia. From November 11 to November 14, 2016, the cybercriminals attacked the following websites multiple times: rosbank.ru (Rosbank) and eximbank.ru (Eximbank of Russia). For more information about this incident, please refer to our previously published news article.
Malicious and unwanted programs for mobile devices
In November, Doctor Web’s security researchers found Android.MulDrop.924 which was being distributed as a benign Google Play application. The Trojan downloaded malicious programs and displayed annoying advertisements. In total, over one million downloads of this Trojan were registered. Later in the month, Android.Spy.332.origin—a Trojan preinstalled on some popular Android devices—was discovered. That malware program downloaded, installed, and removed applications, and sent private information to a criminal-owned server.
The most notable November events related to mobile malware were as follows:
- The detection of Android.MulDrop.924, a Trojan that downloaded Google Play applications and offered to install them. It also displayed advertisements.
- The emergence of Android.Spy.332.origin, a Trojan that was preinstalled on some mobile devices and could download, install, and remove software.
To learn more about the malicious and unwanted programs targeting mobile devices in November, please refer to our special overview.