Doctor Web’s August 2016 virus activity review
August 31, 2016
The last summer month was quite eventful for Doctor Web’s analysts. At the beginning of August, they detected a Trojan capable of infecting POS (Point-Of-Sale) terminals. Shortly thereafter, they discovered two Linux Trojans written in Go, one of which is capable of creating peer-to-peer (P2P) botnets. Also found during the past month were another Trojan using the TeamViewer program and a Trojan designed to install a fake web browser.
PRINCIPAL TRENDS IN AUGUST
- New Trojan infecting POS terminals
- New malicious programs for Windows
- New Linux Trojans written in Go
Threat of the month
Malware programs that use the TeamViewer program are detected quite frequently by security researchers—one such Trojan was described in a news article published in May 2016. In the past month, its counterpart BackDoor.TeamViewerENT.1, which is also known as Spy-Agent, was examined by Doctor Web. However, unlike its predecessors, this Trojan uses TeamViewer specifically to spy on users.
In addition, this backdoor can download the necessary TeamViewer components from the command and control (C&C) server and execute the following commands:
- Restart the computer
- Turn off the computer
- Remove TeamViewer
- Relaunch TeamViewer
- Start listening through the microphone
- Stop listening through the microphone
- Identify the web camera
- Start viewing via the web camera
- Stop viewing via the web camera
- Download a file; then save it to a temporary folder and run it
- Update a configuration file or the backdoor’s executable file
- Connect to the specified remote server; and then run cmd.exe and execute input/output redirection to a remote server
Doctor Web’s security researchers found that the backdoor was targeting residents of particular countries and regions at different times. For more information about this Trojan, refer to the news article.
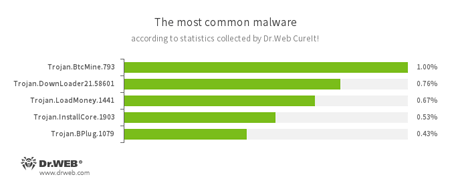
According to statistics collected by Dr.Web CureIt!
- Trojan.BtcMine.793
A Trojan designed to covertly use the infected computer’s resources in order to generate cryptocurrency—for example, Bitcoin. - Trojan.DownLoader
A family of malicious programs designed to download other malware to the compromised computer. - Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on the victim's computer. - Trojan.InstallCore.1903
A Trojan that can install unwanted and malicious applications. - Trojan.BPlug
These plug-ins for popular browsers display annoying advertisements to users browsing webpages.
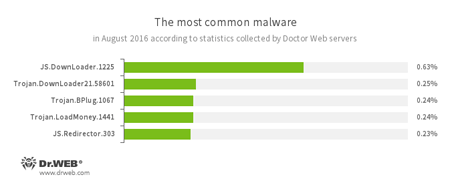
According to Doctor Web’s statistics servers
- JS.Downloader
A family of malicious scripts written in JavaScript and designed to download and install other malware programs on a computer. - Trojan.DownLoader
A family of malicious programs designed to download other malware to the compromised computer. - Trojan.BPlug
These plug-ins for popular browsers display annoying advertisements to users browsing webpages. - Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on the victim's computer. - JS.Redirector
A family of malicious scripts written in JavaScript and designed to automatically redirect users to other webpages.
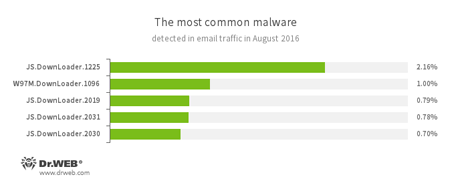
Statistics concerning malicious programs discovered in email traffic
- JS.Downloader
A family of malicious scripts written in JavaScript and designed to download and install other malware programs on a computer. - W97M.DownLoader
A family of downloader Trojans that exploit vulnerabilities in office applications and can download other malicious programs to a compromised computer.
According to statistics collected by Dr.Web Bot for Telegram
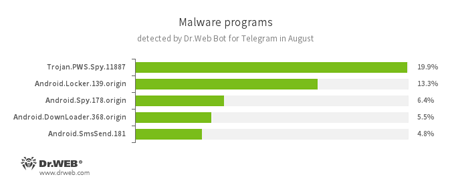
In March 2016, Dr.Web Bot for Telegram was released. It checks links and files on the fly and informs users if any threats have been detected. For example, it can warn that a virus is present in an email attachment or warn against visiting a malicious website. Since March, tens of thousands of people have already used the bot. The statistics collected by Doctor Web’s specialists show that the bot is used to detect Trojans not only for Microsoft Windows but also for the Android platform. In addition, in August 2016, 5.9% of users used the EICAR test file to check the bot’s operation. Below is the list of the five Trojans that were most frequently detected by Dr.Web Bot for Telegram in August:
- Trojan.PWS.Spy
A family of Trojans designed to steal personal information, including passwords, from Windows users. - Android.Locker
A family of ransomware Trojans for Android. Different modifications of these malicious programs can lock a device and display a warning that the user has done something illegal. To unlock the device, the user must pay a ransom. - Android.Spy
A family of multifunctional Trojans for Android that are designed to read and save contacts, receive and send SMS messages, determine GPS coordinates, read and save bookmarks in a browser, and get a device’s IMEI and telephone number. - Android.DownLoader
Trojans that are designed to download and install other malicious programs on Android mobile devices. - Android.SmsSend
A family of Trojans for Android that are designed to send SMS messages to premium numbers.
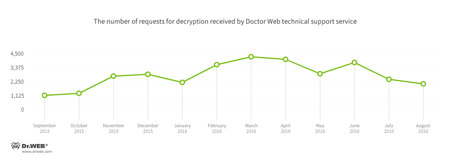
Encryption ransomware
In August, cases involving the following ransomware modifications were registered by Doctor Web’s technical support service:
- Trojan.Encoder.761 — 17.69% of requests
- Trojan.Encoder.858 — 15.40% of requests
- Trojan.Encoder.4860 — 12.56% of requests
- Trojan.Encoder.567 — 9.49% of requests
- Trojan.Encoder.567 — 6.08% of requests
Dr.Web Security Space 11.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows.
| Data Loss Prevention | |
|---|---|
 |  |
Dangerous websites
During August 2016, 245,394 URLs of non-recommended websites were added to Dr.Web database.
| July 2016 | August 2016 | Dynamics |
|---|---|---|
| +139,803 | +245,394 | +75.5% |
Linux
At the beginning of August, Doctor Web’s analysts found a new Trojan written in the Go language. This Trojan, which was subsequently named Linux.Lady.1, is designed to download and run cryptocurrency mining software on a computer. Once Linux.Lady.1 is launched, it sends the following information to the C&C server: the current Linux version and the name of the operating system family it belongs to, the number of CPUs, the names and number of running processes, and so on. In return, the Trojan gets the configuration file it needs to download and launch a cryptocurrency mining program. The income generated is then transferred to an e-wallet belonging to cybercriminals.
For more information about Linux.Lady.1, please refer to the news article.
Another dangerous Linux Trojan—Linux.Rex.1—was discovered in mid August. Like Linux.Lady.1, it was written in Go, however, it can perform a wider variety of functions. Linux.Rex.1 is mainly designed to create P2P (peer-to-peer) botnets and to attack websites built with popular CMSs. In addition, it can send threatening emails to website owners, carry out DDoS attacks, and steal confidential information such as user lists, private SSH keys, logins, and passwords. When commanded by cybercriminals, the Trojan can also launch various applications.
Other threats
August began with the detection of Trojan.Kasidet.1 which is capable of infecting POS (Point-Of-Sale) terminals. In addition, it can steal passwords for the Outlook, Foxmail, and Thunderbird email applications and can be incorporated into Mozilla Firefox, Google Chrome, Microsoft Internet Explorer, and Maxthon browsers for the purpose of intercepting GET and POST requests. This malware program can also download and run another application or a malicious library on an infected computer, find a particular file on a disk, or generate a list of running processes and transmit it to the C&C server. You can find more information about Trojan.Kasidet.1 in this news article.
At the end of August, Doctor Web specialists discovered Trojan.Mutabaha.1, a Trojan that installs a fake Chrome browser on computers.
Although the browser is known under the name Outfire, the creators of Trojan.Mutabaha.1 distributed 56 similar browsers with different names. Outfire modifies the installed Google Chrome browser by removing or creating new shortcuts and copying current Chrome user account information into the new browser. The fake browser displays a home page that cannot be changed in the browser’s settings. In addition, it has a fixed extension designed to replace advertisements in browsed webpages. For more information about this malware program, refer to the review published by Doctor Web.
Malicious and unwanted programs for mobile devices
In August, Doctor Web’s specialists detected a Trojan for Android that displays advertisements on top of running applications and the operating system interface. The Trojan can also buy software on Google Play and download it onto a device. In addition, bogus Dr.Web for iOS products were found on Apple iTunes in the past month.
Among the most notable August events related to mobile malware, we can mention:
- A new Android Trojan designed to display advertisements, and to buy apps on Google Play and download them onto a device;
- The detection of fake Dr.Web for iOS applications on Apple iTunes.
Learn more about malicious and unwanted programs for mobile devices in our special August overview.