June 2016 virus activity review from Doctor Web
June 30, 2016
The first summer month was quite eventful in terms of information security. At the beginning of June, Doctor Web specialists finished the research of the Bolik banking Trojan and soon after that, they found a fileless advertising Trojan named Trojan.Kovter.297. Besides, the number of Trojans for accounting software has increased: first, a dangerous ransomware Trojan, which was spread by a dropper written in 1C incorporated programming languages, was registered. Then our security researchers found a spyware Trojan—Trojan.PWS.Spy.19338—able to log keystrokes in different applications including accounting ones. In addition, virus makers continued to attack Google Play: our analytics detected Trojans in Android applications twice this month.
PRINCIPAL TRENDS IN JUNE
- New polymorphic banking Trojan
- Spread of a Trojan for 1C software
- New fileless advertising Trojan—Trojan.Kovter
- Spread of a dangerous spyware Trojan—Trojan.PWS.Spy.19338
Threat of the month
Most of Russian companies choose 1C accounting programs. Virus makers also follow this trend to contrive new threats. Therefore, Doctor Web analytics have already encountered applications written in 1C programming language. Yet, 1C.Drop.1 differs from its counterparts by its architecture and purpose—this Trojan is designed as a fully-featured dropper that saves the Trojan.Encoder.567 ransomware Trojan on disk and runs it.
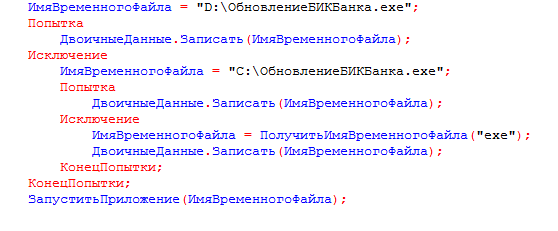
The Trojan is distributed via email titled “Our BIC code has been changed” that contains an external data processor for 1C:Enterprise. If the user opens the file in 1C:Enterprise, the Trojan sends out its copy to all contractors whose email addresses are specified in the database. Then it retrieves Trojan.Encoder.567, saves it on disk and runs the ransomware program. This dangerous encoder encrypts files on the computer’s disks and demands a ransom for their decryption. 1C.Drop.1 supports the following 1C databases:
- Trade Management 11.1
- Trade Management (basic) 11.1
- Trade Management 11.2
- Trade Management (basic) 11.2
- Accounting 3.0
- Accounting (basic) 3.0
- 1C:Comprehensive Automation 2.0
For more information about this incident, refer to the news article.
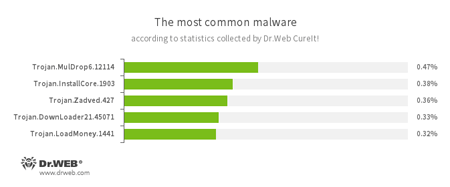
According to statistics collected by Dr.Web CureIt!
Trojan.MulDrop
А Trojan that can install other malicious programs on the computer.Trojan.InstallCore.1903
A Trojan that can install unwanted and malicious applications.Trojan.Zadved
This Trojan displays fake search results in the browser window and imitates pop-up messages from social networking sites. In addition to this, the malware can replace advertisements displayed on different Internet resources.Trojan.DownLoader
A family of malicious programs designed to download other malware to the compromised computer.Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on the victim's computer.
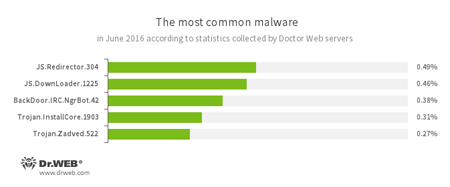
According to Doctor Web statistics servers
JS.Redirector
A family of malicious scripts that are written in JavaScript and designed to automatically redirect users to another webpages.JS.Downloader
A family of malicious scripts that are written in JavaScript and designed to download and install other malware programs on the computer.BackDoor.IRC.NgrBot.42
A fairly common Trojan, which is known to information security researchers since 2011. Malicious programs of this family are able to execute intruder-issued commands on infected machine controlled by cybercriminals via the IRC (Internet Relay Chat) text-messaging protocol.Trojan.InstallCore.1903
A Trojan that can install unwanted and malicious applications.Trojan.Zadved
This Trojan displays fake search results in the browser window and imitates pop-up messages from social networking sites.
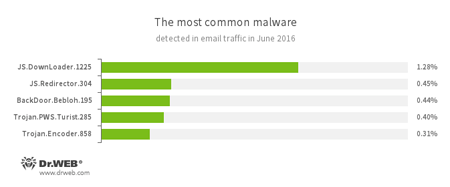
Statistics concerning malicious programs discovered in email traffic
JS.Redirector
A family of malicious scripts that are written in JavaScript and designed to automatically redirect users to another webpages.JS.Downloader
A family of malicious scripts that are written in JavaScript and designed to download and install other malware programs on the computer.A malicious program belonging to the family of banking Trojans. This application poses a threat to users of e-banking services (RBS), because it allows cybercriminals to steal confidential information by intercepting data submitted through forms in the browser window and by embedding the malicious code into bank webpages.
Trojan.PWS.Turist
A Trojan designed to steal login credentials and other private information necessary to access online banking applications (including ones that require Smart Cards for authorization)Trojan.Encoder.858
A malicious program belonging to the family of encryption ransomware Trojans that encrypt files and demand a ransom for decryption of compromised data.
Encryption ransomware
The most common ransomware programs in June 2016:
- Trojan.Encoder.858
- Trojan.Encoder.2843
- Trojan.Encoder.4860
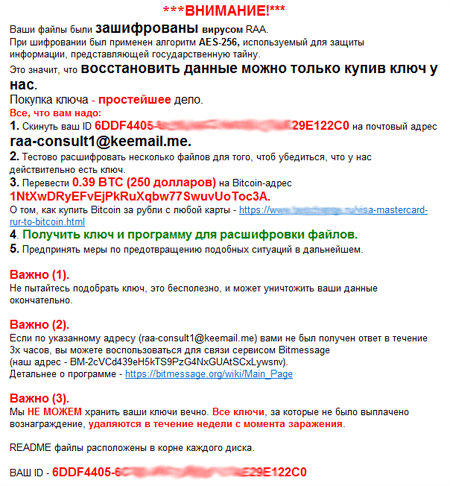
In June, Trojan.Encoder.4860, also known as JS.Crypt, has become more popular among attackers. Its key feature lies in the fact that the Trojan is written in JScript. It is distributed under the name of “RAA virus”, and all locked files are appended with the *.locked extension. When Trojan.Encoder.4860 finishes to encrypt all files on the computer, it locates the following RTF document in root folders:
At present, Doctor Web specialists have not yet developed a new technique that will help to encrypt files corrupted by this malware.
Dr.Web Security Space 11.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows.
| Data Loss Prevention | |
|---|---|
 |  |
Other threats
In June, Doctor Web security researchers examined Trojan.Bolik.1, a dangerous virus targeting Russian bank clients. The virus is designed to steal money from bank accounts and to monitor user activity. It also steals private information and can spy on the user. The Trojan has borrowed a lot of features from its predecessors Zeus (Trojan.PWS.Panda) and Carberp.
Upon cybercriminals’ command, Trojan.Bolik.1 checks open-for-write folders for the presence of executable files in the Windows system or on connected USB devices and then infects them. Dr.Web Anti-virus detects programs infected by this virus as Win32.Bolik.1. Every such program contains Trojan.Bolik.1 in encrypted form and other necessary information.
Trojan.Bolik.1 controls data transmitted by Microsoft Internet Explorer, Chrome, Opera, and Mozilla Firefox to steal information entered into input forms. Besides, the malware program can take screenshots and perform the keylogger functions. Trojan.Bolik.1 is also able to create its own proxy server and web server for file sharing with virus makers. To learn more about this Trojan, read our review.
Yet another Trojan was detected by our specialists—Trojan.Kovter.297. It can run several windows of Microsoft Internet Explorer simultaneously, visits websites specified by virus makers and generates traffic for them by following advertising links and banners. Therefore, attackers make money on affiliate programs and advertisers. Their key feature lies in the fact that their payload is located not in a file but directly in the computer’s memory. Necessary files needed for their operation are stored in the Windows system registry.
For more details about Trojan.Kovter.297, refer to the article.
In the end of June, Doctor Web specialists discovered a group of malicious programs that included Trojan.PWS.Spy.19338, a spyware Trojan for accounting software. This Trojan is mainly designed to log keystrokes in such applications as 1C of various versions and SBIS++. It also collects information about the system and sends clipboard data to attackers. you can learn more about Trojan.PWS.Spy.19338 in the news article.
In June, our security researchers detected a Trojan for Linux—Linux.BackDoor.Irc.13—which a modification of Linux.BackDoor.Tsunami; yet, it cannot carry out DDoS attacks. This Trojan executes commands recieved via the IRC (Internet Relay Chat) text-messaging protocol.
Virus makers continued to target Apple users in June: Doctor Web specialists discovered new Trojan for OS X—Mac.BackDoor.SynCloud.1. Once launched, it extracts logins and passwords of all users authorized in the system at the moment. Then it sends this information to the server. Mac.BackDoor.SynCloud.1 downloads an executable file or a script written in Python and executes them. It can also perform other functions—for example, update itself. All transmitted information is encrypted.
Dangerous websites
During June 2016, 1,716,920 URLs of non-recommended sites were added to Dr.Web database.
| May 2016 | June 2016 | Dynamics |
|---|---|---|
| +550,258 | +1,716,920 | +212% |
Malicious and unwanted programs for mobile devices
In June, Doctor web security researchers detected several malicious applications being spread via Google Play—Android.Valeriy.1.origin is one of them. This Trojan is able to load dubious websites and display them as advertisements in order to get users’ mobile phone number and subscribe them to chargeable services. Then a certain subscription fee is written off from the user’s mobile account every day. The Trojan can also download malicious programs and execute JavaScript scripts.
Yet another malware program—Android.PWS.Vk.3—was discovered on Google Play as well. This Trojan was represented as a media player for VK music. It prompted the user to enter their login and password for the VK user account and then sent this private information to cybercriminals.
Among the most noticeable June events related to mobile malware, we can mention
- Detection of a Trojan that opens suspicious websites as advertisements on Google Play.
- Detection of a Trojan that steals logins and passwords from VK user profiles.