February 2016 mobile malware review from Doctor Web
February 29, 2016
PRINCIPAL TRENDS IN FEBRUARY
- New multicomponent Trojan capable to inject itself into system processes and to perform a wide variety of functions
- New cases of mobile devices being infected with banking Trojans
Mobile threat of the month
In February, Doctor Web specialists examined a group of associated Trojans belonging to the Android.Loki family, whose purpose was to execute a wide range of functions. One of them has been added to the Dr.Web virus database under the name of Android.Loki.3. This Trojan incorporates the liblokih.so library, which is named Android.Loki.6, into an Android system process. As a result, other components of this group are able to operate using the system privileges. The Trojans of this family are mainly designed to
- Download and delete applications.
- Enable and disable applications and their components.
- Kill processes.
- Display notifications.
- Register any application as the Accessibility Service application.
- Update their components and download plug-ins from the server.
- Gather information regarding the infected device.
Also, they send the following data to the command and control server:
- List of installed applications
- Browser history
- List of contacts
- Call history
- Current location
For more information, refer to the news article.
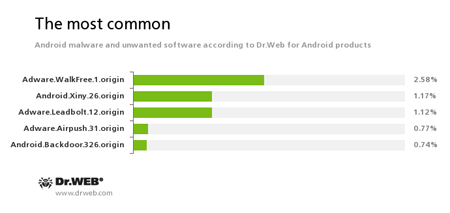
According to statistics collected by Dr.Web for Android
- Adware.WalkFree.1.origin
An unwanted program module that is incorporated into the Android applications and is responsible for advertising on mobile devices. - Android.Xiny.26.origin
A Trojan designed to download and install applications and to display advertisements. - Adware.Leadbolt.12.origin
An unwanted program module that is incorporated into the Android applications and is responsible for advertising on mobile devices. - Adware.Airpush.31.origin
An unwanted program module that is incorporated into the Android applications and is responsible for advertising on mobile devices. - Android.Backdoor.326.origin
A Trojan that performs different malicious functions upon cybercriminals’ command.
Banking Trojans
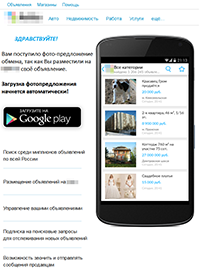
Virus makers keep distributing various banking Trojans for Android devices. In particular, they are still trying to trick users of popular classified sites by sending bogus SMS messages. At receiving a such-like text message, potential victims, who have previously posted some announcement on the Web, are offered some exchange. At that, the message contains a link that allegedly leads to a photo of the offered product. If the user follows the link, they are redirected to one of fraudulent webpages that is, in fact, the source of infection. For instance, Android.BankBot.97.origin can be mentioned among Trojans distributed this way.
 |
 |
The past month showed that attackers are not going to stop contriving malware for Android mobile devices. Therefore, Doctor Web specialists will be keeping a close watch on Android malware landscape and will timely inform users about new threats.