January 2016 virus activity review from Doctor Web
January 29, 2016
The first month of 2016 saw the emergence of new various Trojans for Linux including yet another modification of a ransomware Trojan and a dangerous backdoor capable of screenshot taking, keylogging, and executing commands from cybercriminals. Besides, in January, security researchers detected a Trojan for Android pre-installed on the firmware of a smartphone produced by a well-known electronics manufacturer. Moreover, at the end of the month, Doctor Web security researchers detected various malware programs on Google Play.
Principal trends in January
- Emergence of new malicious programs for Linux
- Appearance of new encryption ransomware for Linux
- Distribution of a dangerous Trojan in Android firmware
Threat of the month
At the end of January, Doctor Web specialists examined a multipurpose backdoor Trojan for Linux devices. It consists of a dropper and a payload that is responsible for executing main malicious functions. Once launched, the dropper displays the following dialog:
If the Trojan is successfully run, it extracts the backdoor—its main malicious component—from its body and saves it into some folder on the infected computer’s hard drive. In total, this module is capable to execute more than 40 commands. Among them are keylogging—recording of keystrokes on the infected device—and downloading and running of different software. Besides, it can also send file names in a specified directory and upload selected files to the server. In addition to this, the Trojan creates, removes, and renames files and folders, takes screenshots, executes the bash commands; and performs many other malicious functions. For more information about this dangerous Trojan, refer to the news article published by Doctor Web.
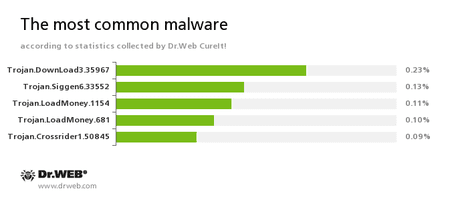
According to statistics collected by Dr.Web CureIt!
Trojan.DownLoad3.35967
A Trojan that can download other malicious programs from the Internet and install them on the infected computer.Trojan.Siggen6.33552
This malicious program is designed for installation of other malware.Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on the victim's computer.Trojan.Crossrider1.50845
Trojans designed to display various advertisements.
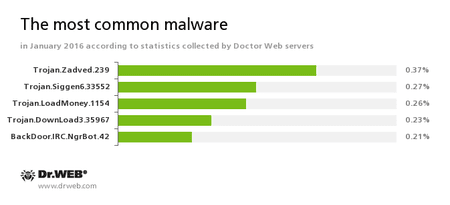
According to Doctor Web statistics servers
Trojan.Zadved
This Trojan displays fake search results in the browser window and imitates pop-up messages from social networking sites. In addition to this, the malware can replace advertisements displayed on different Internet resources.Trojan.Siggen6.33552
This malicious program is designed for installation of other malware.Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on the victim's computer.Trojan.DownLoad3.35967
A Trojan that can download other malicious programs from the Internet and install them on the infected computer.BackDoor.IRC.NgrBot.42
A fairly common Trojan, which is known to information security researchers since 2011. Malicious programs of this family are able to execute intruder-issued commands on infected machine controlled by cybercriminals via the IRC (Internet Relay Chat) text-messaging protocol.
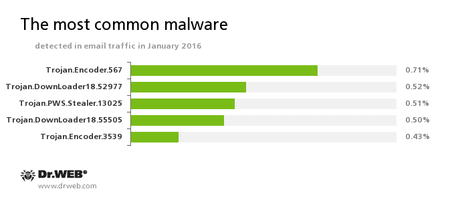
Statistics concerning malicious programs discovered in email traffic
Trojan.Encoder.567
A malicious program belonging to the family of encryption ransomware Trojans that encrypt files and demand a ransom for decryption of compromised data. This program can encrypt important user files, for example, of the following types: .jpg, .jpeg, .doc, .docx, .xls, xlsx, .dbf, .1cd, .psd, .dwg, .xml, .zip, .rar, .db3, .pdf, .rtf, .7z, .kwm, .arj, .xlsm, .key, .cer, .accdb, .odt, .ppt, .mdb, .dt, .gsf, .ppsx, .pptx.Trojan.DownLoader
A family of malicious programs designed to download other malware to the compromised computer.Trojan.PWS.Stealer
A family of Trojans designed to steal passwords and other confidential information stored on the infected computer.Trojan.Encoder.3539
A malicious program belonging to the family of encryption ransomware Trojans that encrypt files and demand a ransom for decryption of compromised data.
Botnets
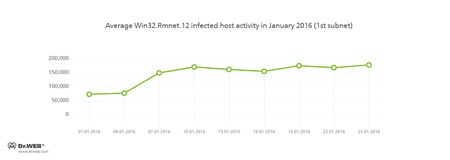
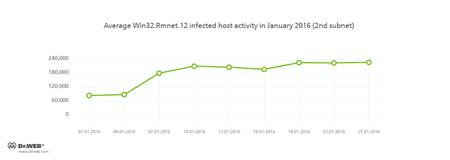
Doctor Web's security researchers continue to monitor the botnets created by criminals with the file infector Win32.Rmnet.12.
Rmnet is a family of viruses spread without any user intervention. They can embed content into loaded webpages (this theoretically allows cybercriminals to get access to the victim's bank account information), steal cookies and passwords stored by popular FTP clients, and execute other commands issued by cybercriminals.
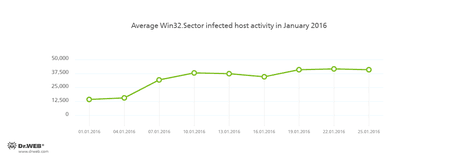
The botnet consisting of computers infected with the Win32.Sector file virus is still active. This malicious program can perform the following actions:
- Download various executable files via P2P networks and run them on infected machines.
- Inject its code into running processes.
- Prevent some anti-viruses from operating and block access to the websites of their respective developers.
- Infect files on local disks, removable media (where the malware creates the autorun.inf file during the infection process), and in shared folders.
Its average daily activity can be seen in the following picture:
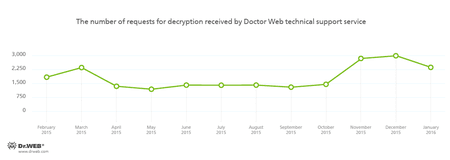
Encryption ransomware
The most common ransomware programs in January 2016
Dr.Web Security Space 11.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows
| Data Loss Prevention | |
|---|---|
 |  |
Linux
January 2016 turned out to be rather fruitful due to a record-breaking number of Trojans for Linux detected during this month. At the beginning of January, Doctor Web security researchers examined a new modification of Linux.Encoder.3. Virus makers have improved this version of the ransomware Trojan by fixing code mistakes that had been made previously. Nevertheless, some architectural features of Linux.Encoder.3 make it possible to decrypt corrupted files.
Linux.Encoder.3 does not require root privileges—web server privileges are enough for the Trojan to encrypt all files in the home directory of a website. A key feature of Linux.Encoder.3 lies in its capability to remember dates of files creation or modification that are then replaced with dates specified before the encryption. Moreover, cybercriminals have changed encryption algorithms used by the Trojan: every sample of this malicious program uses its unique encryption key created based on parameters of encrypted files and values generated randomly. For more information about this Trojan, refer to the review published by Doctor Web.
Shortly after that, Doctor Web specialists detected Linux.Ekoms.1, about which you can read in our news article. Every 30 seconds, Linux.Ekoms.1 takes a screenshot and saves it into a temporal folder in the JPEG format. The temporary folder is uploaded to the server in specified intervals. This malicious program can also send files from the infected machine to cybercriminals and download and save files received from them.
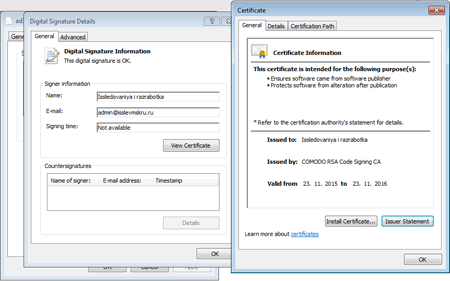
It should be noted that Trojan.Ekoms.1, a Windows version of Linux.Ekoms.1, was registered by Doctor Web in January. Once launched, it checks the %appdata% folder for specified executable files in order to prevent infections by other Trojans. Apart from screenshot taking, Trojan.Ekoms.1 creates a file with the .kkt extension that stores information on key strokes and a file that is appended with the .ddt extension and contains a list of files in folders. These two files are then sent to the server. It is noteworthy that these files are also mentioned in Linux.Ekoms.1, but the similar Trojan for Linux does not have a code responsible for their processing. Like the Trojan for Linux, Trojan.Ekoms.1 can record sound and save it in the WAV format. However, this function is not used in this modification as well. The Trojan has a valid digital signature registered to some company named “Issledovaniya i razrabotka”, and a root certificate is issued by Comodo.
At the end of January, several popular websites and blogs published information about an allegedly brand new Trojan for Linux—“TheMoon”. However, this Trojan dubbed Linux.Themoon.2 has been detected by Dr.Web for Linux since December 14, 2015. To learn more about technical details of this malicious program, refer to the review.
Dangerous websites
During January 2016, 625,588 URLs of non-recommended websites were added to Dr.Web database.
| December 2015 | January 2016 | Dynamics |
|---|---|---|
| +210,987 | +625,588 | +196% |
Find out more about Dr. Web non-recommended sites
Malicious and unwanted programs for mobile devices
The previous month showed once again that cybercriminals do not intend to lose their interest in Android mobile devices. In particular, in mid-January, Doctor Web security researchers detected Android.Cooee.1, a dangerous Trojan designed to download and install various applications, on the Philips s307 firmware. At the end of the month, Doctor Web analysts found that more than 60 games on Google Play were affected by Android.Xiny.19.origin. This Trojan can covertly run apk files received from the server, download applications, and prompt a user to install various software. It also displays annoying advertisements.
Among the most noticeable January events related to mobile malware we can mention
- Detection of a Trojan incorporated into a large number of games on Google Play
- Distribution of a Trojan pre-installed on the Philips s307 firmware
Find out more about malicious and unwanted programs for mobile devices in our special overview.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live
[% END %]