November 2015 virus activity review from Doctor Web
November 30, 2015
November 2015 will be memorable due to the spread of Linux.Encoder.1, the encryption ransomware for Linux systems. This encoder is far from being the first that posed a threat to Linux users. Already in August 2014, Doctor Web announced about Trojan.Encoder.737 capable to encrypt files stored on Synology NAS servers. What is more, before the spread of Linux.Encoder.1, at least two modifications of this malware were found. Nevertheless, it was Linux.Encoder.1 whose malicious activity was more widespread. According to Google data, this encoder has managed to infect more than 3,000 websites worldwide.
PRINCIPAL TRENDS IN NOVEMBER
- More than 3,000 computers infected by the hazardous Linux.Encoder.1
- Spread of malware that gets unauthorized access to a compromised computer
- New malware for Microsoft Windows and Android
Threat of the month
The Linux.Encoder.1 distributors` main targets were the owners of websites created using WordPress and Magento content management systems (CMS). During attacks, virus makers exploited an unidentified vulnerability. Experts say that the encoder does not need root privileges—www-data privileges (that is, it is run under the same user as Apache itself runs) are quite enough. As of November 12, Linux.Encoder.1 has presumably infected more than 2,000 websites, which can be judged from search results if the name of the file with cybercriminals` demands is entered into the Google search bar. However, by the 24th of November the number of compromised websites exceeded 3,000.
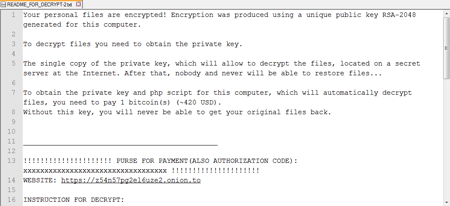
The encoder runs on the server with an attacked website, using a shell script previously injected in the CMS. With the help of the same script, hackers plant another file, which is, in fact, a dropper for Linux.Encoder.1, on the server. It is assumed that upon a command from cybercriminals, the dropper identifies the operating system architecture (32-bit or 64-bit), extracts from the body a corresponding sample of encryption ransomware, runs it, and then initiates its own removal. Once launched on the attacked server, the Trojan encrypts all files in directories for which it has write-access permissions. After that, the malicious program saves the README_FOR_DECRYPT.txt file containing decryption instructions and cybercriminals' demands on the server disk. If, by some chance, the Trojan acquires more elevated privileges, its malicious activities will not be limited to the web server directory only.
A website can be infected because of several reasons: incorrect settings by the website administrators, late installation of CMS security updates, and usage of outdated CMS versions and hacked commercial WordPress and Magento commercial elements and modules, etc.
Due to the fact that the code of Linux.Encoder.1 has a number of significant flaws, data encrypted by the Trojan can be decrypted. You can get more familiar with the features of this malware by referring to the review or detailed research of this Trojan published by Doctor Web.
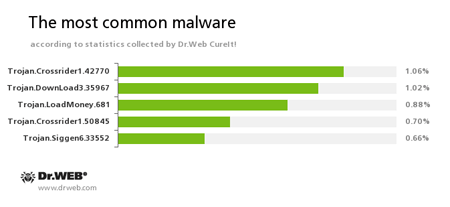
According to the statistics gathered by Dr.Web CureIt!
Trojan.Crossrider1.42770, Trojan.Crossrider1.50845
Trojans designed to display various advertisements.Trojan.DownLoad3.35967
A Trojan that can download other malicious programs from the Internet and install them on the infected computer.Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on the victim's computer.Trojan.Siggen6.33552
This malicious program is designed for installation of other malware.
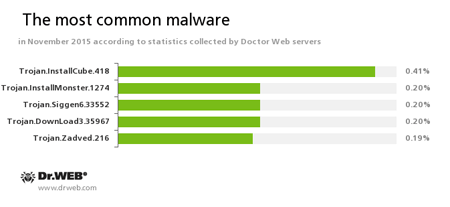
According to Doctor Web statistics servers
Trojan.InstallCube
A family of downloader programs designed to install unwanted and useless applications on the user’s computer.Trojan.Installmonster
A family of malicious programs created using the Installmonster affiliate program. These programs install various unwanted software on the victim's computer.Trojan.Siggen6.33552
A malicious program designed to install other dangerous software on the infected computer.Trojan.DownLoad3.35967
A Trojan that can download other malicious programs from the Internet and install them on the infected computer.Trojan.Zadved
This Trojan displays fake search results in the browser window and imitates pop-up messages from social networking sites.
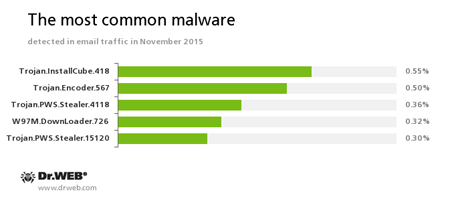
Statistics concerning malicious programs discovered in email traffic
Trojan.InstallCube
A family of downloader programs designed to install unwanted and useless applications on the user’s computer.Trojan.Encoder.567
A malicious program belonging to the family of encryption ransomware Trojans that encrypt files and demand a ransom for decryption of compromised data. This program can encrypt important user files, for example, of the following types: .jpg, .jpeg, .doc, .docx, .xls, xlsx, .dbf, .1cd, .psd, .dwg, .xml, .zip, .rar, .db3, .pdf, .rtf, .7z, .kwm, .arj, .xlsm, .key, .cer, .accdb, .odt, .ppt, .mdb, .dt, .gsf, .ppsx, .pptx.Trojan.PWS.Stealer
A family of Trojans designed to steal passwords and other confidential information stored on the infected computer.W97M.DownLoader.726
A downloader Trojan that exploits vulnerabilities in office applications and can download other malicious programs to the compromised computer.
Botnets
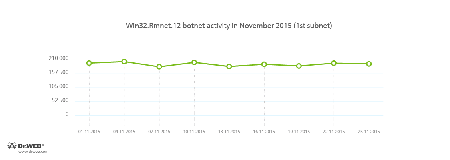
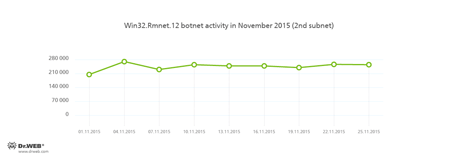
Doctor Web security researchers continue to monitor a botnet created by cybercriminals using the Win32.Rmnet.12 file infector. The average daily activity of the botnet`s two subnets in November is shown in the following graphs:
Rmnet is a family of viruses spread without any user intervention. They can embed content into loaded webpages (this theoretically allows cybercriminals to get access to the victim's bank account information), steal cookies and passwords stored by popular FTP clients, and execute other commands issued by cybercriminals.
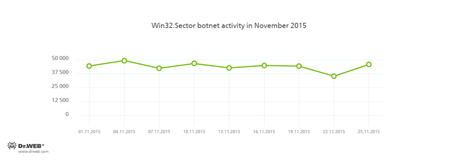
The botnet, which was created using the Win32.Sector file injector, is still active. Its average daily activity can be seen in the following picture:
The malware can perform the following actions:
- Download various executable files via P2P networks and run them on infected machines.
- Inject its code into running processes.
- Prevent some anti-viruses from operating and block access to the websites of their respective developers.
- Infect files on local disks, removable media (where the malware creates the autorun.inf file during the infection process), and in shared folders.
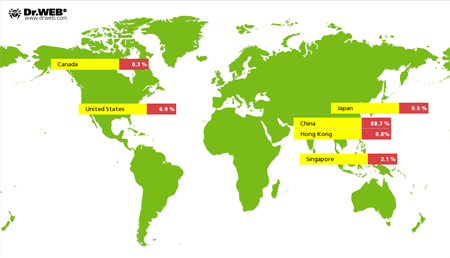
Last month, DDoS attacks mounted using Linux.BackDoor.Gates.5 In November, the number of such attacks continued to go down. The amount of compromised websites decreased by 27.9% and was estimated 3,641. Thus, China was ranked first, while the United States took the second place.
Encryption ransomware
The most common ransomware programs in November 2015
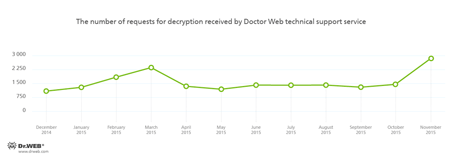
Doctor Web technical support receives decryption requests not only from Russian users but also from foreign ones. Doctor Web helps users from European countries decrypt information. In November, Doctor Web technical support received a number of decryption requests from website owners who encountered Linux.Encoder.1. It should be noted that all the known utilities, used to decrypt files compromised by Linux.Encoder.1, do not delete the shell script from the infected server—thus, cybercriminals can use it later to reinfect the system. That is why Doctor Web technical support specialists help all website owners remove additional malicious programs from their systems and protect their machines from future possible attacks carried out using this script.
Dr.Web Security Space 11.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows
| Data Loss Prevention | |
|---|---|
 |  |
Linux
Linux.Encoder.1 is far from being the only encoder that poses a threat to Linux users. Information security researchers detected at least two representatives of this malware family that came into light before Linux.Encoder.1. However, for a long time this particular modification did not fall under the scrutiny of security researchers.
In particular, the new Trojan named Linux.Encoder.2 differs from its counterparts by employing another pseudorandom number generator and encrypts files using the OpenSSL library (not PolarSSL, like Linux.Encoder.1). Moreover, encryption is performed in the AES-OFB-128 mode with context reinitialization every 128 bytes, that is every 8 AES blocks. Also in Linux.Encoder.2 there are a number of other significant changes from the alternative execution of this encoder. For more details about this malware, refer to the review.
Moreover, in November Doctor Web security researchers detected Linux.Sshcrack.1 that cracks a login and password combination using a special dictionary (brute-force technique) to get unauthorized access to various devices.
Other malicious applications
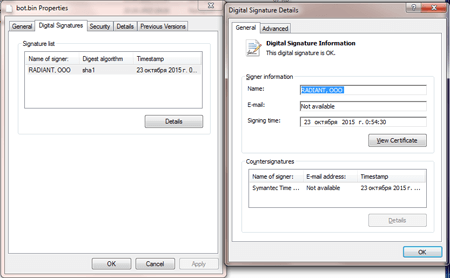
In mid-November Doctor Web specialists examined a whole pack of malicious programs distributed by cybercriminals. The pack disguised as an RTF document was named BackDoor.RatPack. Once the document was opened, a malicious file was decrypted and saved to the victim's computer. It should be noted that the file, which is, in fact, an installer, has a valid digital signature (like almost any other file from BackDoor.RatPack).
Once launched, the installer scans the system for virtual machines, monitoring programs, and debuggers. Then it initiates a search for online banking applications of several Russian financial organizations. The installer payload bears a modification of a shareware program called Remote Office Manager—Doctor Web security researchers have detected at least three versions of this program that differ in configuration settings. By intercepting a number of system functions, the malicious program is able to conceal the tool's shortcuts in the Windows taskbar and notification area preventing the user from detecting the presence of the program. One can assume that cybercriminals employ BackDoor.RatPack to steal banking information and other confidential data by remotely controlling the compromised machine. For more information about this incident refer to the review published by Doctor Web.
Dangerous websites
During November 2015, 670,545 URLs of non-recommended websites were added to Dr.Web database.
| October 2015 | November 2015 | Dynamics |
|---|---|---|
| + 264,970 | + 670,545 | + 153 % |
Malicious and unwanted programs for Android
November appeared to be rather calm for mobile devices users. Nevertheless, in November cybercriminals were still trying to infect tablets and smartphones. However, all the detected malicious and unwanted programs were immediately added to Dr.Web virus database. In particular, Doctor Web security researchers detected the Android adware that was installed by a Trojan and showed annoying notifications on top of applications launched by a user. Moreover, during the whole month, Android devices were attacked by ransomware programs, banking Trojans, SMS Trojans and other dangerous applications. Besides, in November security researchers detected yet another Trojan modification which infected iOS devices.
Among the most noticeable November events related to mobile malware we can mention
- Detection of an unwanted Android application which displayed advertisements on top of applications launched by a user
- Detection of new Trojans for iOS systems
Find out more about malicious and unwanted programs for mobile devices in our special overview.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live
[% END %]