October 2015 mobile malware review from Doctor Web
October 30, 2015
PRINCIPAL TRENDS IN OCTOBER
- Detection of a dangerous Trojan targeting iOS devices
- Detection of yet another malicious program on Google Play
- New cases of Android firmware being infected with malicious applications
- Emergence of new banking Trojans
Number of entries for malicious and unwanted software targeting Android OS in Dr.Web virus database
| September 2015 | October 2015 | Dynamics |
|---|---|---|
| 14,033 | 15,135 | +7.85% |
Mobile threat of the month
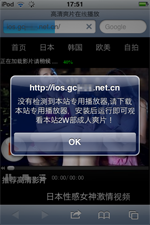
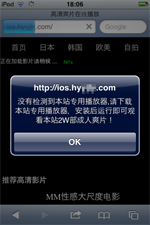
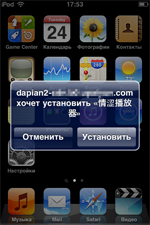
At the beginning of October, security researchers detected a new Trojan targeting iOS. The program, dubbed IPhoneOS.Trojan.YiSpecter.2, was distributed as a harmless application mainly among users in China. In particular, if the user visited a website with adult content to view some videos, they were prompted to install a special video player that, although it had all the necessary features to play those videos, contained a Trojan. To spread this malicious program, cybercriminals employed a corporate software distribution method that allows iOS devices' owners to get applications from sources other than the App Store—at that, IPhoneOS.Trojan.YiSpecter.2 got installed on all smartphones and tablets regardless of whether they were “jailbroken” or not.
IPhoneOS.Trojan.YiSpecter.2 has the following features:
- Sends the command and control server information about the compromised mobile device.
- Installs additional Trojan modules necessary for its operation.
- Can uninstall programs or replace them with fake copies upon a command from the command and control server.
- Can display advertisements on iOS devices.
- If the user removes the Trojan or one of its components, a malicious module will reinstall them.
Trojans on Google Play
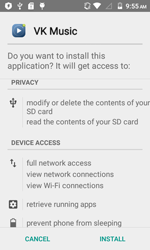
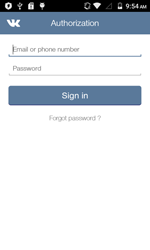
In October, security researchers detected yet another Trojan on Google Play. The Trojan, dubbed as Android.PWS.3, was disguised as an audio player that enabled Vkontakte (“ВКонтакте”) users to listen to audio content. Once launched, Android.PWS.3 prompted the potential victim to log in to their Vkontakte account displaying an appropriate authorization form. Once the user entered their login and password, the Trojan forwarded that information to cybercriminals. Moreover, after a connection to the command and control server was established, the Trojan received a list of Vkontakte groups where it automatically added users of compromised devices promoting the communities.
Firmware Trojans
Almost every month Doctor Web security researchers register new cases of Android firmware being infected with malicious applications—the second autumn month did not become an exception. This time, several mobile devices had a preinstalled malicious program dubbed Android.Cooee.1. The malware is incorporated in a launching application (Android graphical shell) and contains a number of special modules responsible for showing advertisements. Moreover, the malware can download and run not only additional advertising packages but also other applications, including malicious ones—in particular, Android.DownLoader.225 designed to stealthily download various programs on the compromised device.
If the user removes the launching application containing Android.Cooee.1, next time the device is turned on, the operating system will not load. Therefore, before uninstalling the malicious program, users are recommended to install some other launching application and set it as default.
Banking Trojans
In October, a large number of various banking Trojans continued to target Android devices. One of such Trojans is Android.BankBot.80.origin that was detected at the end of the month and was disguised as an official banking application of a Russian financial organization. Once Android.BankBot.80.origin is installed and run, it prompts the user to grant it administrator privileges. After the consent is given, the malware scans the user's contact list sending all numbers SMS messages that look as follows: Hi! Vote for me http://******konkurs.ru/ (“Привет, проголосуй за меня http://******konkurs.ru/”). The link from such a message leads to a fraudulent website supposedly related to some photo contest. From this website, a modification of the Trojan detected by Dr.Web as Android.SmsBot.472.origin gets downloaded to the victim's device. Moreover, the website offers owners of smartphones and tablets to install a special program for voting which is, in fact, another version of Android.BankBot.80.origin.
The Trojan's features are as follows:
- Is disguised as legitimate software, for example, as an official online banking application or a voting program.
- Constantly asks the user to grant it administrator privileges displaying an appropriate prompt that prevents the victim from operating the device in a usual way.
- Sends all user's contacts SMS messages with a link to a fraudulent website from which a modification of the Trojan gets downloaded to the victim's device.
- Can steal money from mobile accounts, bank accounts, and payment system accounts.
- Enables call forwarding to a specified number preventing the user from receiving incoming calls.
For more information about Android.BankBot.80.origin, refer to the news article published on our website.
The number of entries for banking Trojans of the Android.BankBot family in Dr.Web virus database:
| September 2015 | October 2015 | Dynamics |
|---|---|---|
| 142 | 148 | +4.2% |
The number of entries for multicomponent Trojans of the Android.SmsSend family in Dr.Web virus database:
| September 2015 | October 2015 | Dynamics |
|---|---|---|
| 520 | 550 | +5.8% |