April 2015 Android malware review from Doctor Web
April 30, 2015
PRINCIPAL TRENDS IN APRIL
- Distribution of Android.Toorch.1.origin, which is a very dangerous Trojan and is able to get root access for hidden installation and removal of various applications.
- Detection of applications with aggressive advertising module on Google Play.
- High activity of banking Trojans.
Number of entries for malicious and unwanted software targeting Android OS in Dr.Web virus database
| March 2015 | April 2015 | Growth |
|---|---|---|
| 7103 | 7971 | +12,22% |
Mobile threat of the month
Last month Doctor Web security researches examined Android.Toorch.1.origin, which is a dangerous Trojan and is able to stealthily download, install, and remove applications, as well as display annoying advertisements on the screen of infected devices. Trojan's features are as follows:
- Distributed under the guise of a harmless torch application, which, in fact, performs the malicious functions mentioned above.
- Sends cybercriminals confidential data, including GPS coordinates of the infected device.
- Gets root access and performs hidden installation and removal of the applications specified in cybercriminals' commands.
- Adds other malicious components to the system directory.
- Optionally displays annoying advertisements.
If Android.Toorch.1.origin is detected on a mobile device, we strongly recommend to run a full scan of the system by Dr.Web for Android in order to detect all additional modules of the Trojan. To permanently delete all modules installed by the malware, download and install the tool specially designed by Doctor Web experts. Once installation is complete, start the tool and follow the steps displayed on the screen. Find out more about the Trojan in this news item.
Aggressive advertising modules
In April, applications containing aggressive advertising modules, including Adware.MobiDash.2.origin, were detected on Google Play. Doctor Web security researched discovered several suchlike applications; at that, the total number of downloads was more than 2,500,000. Adware.MobiDash.2.origin is used by free software developers to monetize the application and, thus, displays various advertisements. The application can execute the following unwanted actions:
- Display on the mobile device’s screen different advertisements that can appear on top of other windows.
- Load advertising webpages in the browser.
- Show advertising and other messages on the status bar.
 |
 |
The number of entries for adware in Dr.Web virus database:
| March 2015 | April 2015 | Growth |
|---|---|---|
| 123 | 144 | +17,1% |
Banking Trojans
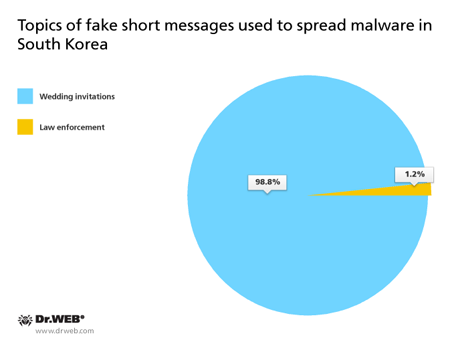
April was marked by high activity of banking Trojans targeting Android mobile devices and posing a threat to users worldwide. In particular, cybercriminals used SMS spam messages to distribute a banking Trojan in South Korea. The messages contained a link to download one or another malicious application. Doctor Web security researchers registered more than 80 spam mailings; at that, cybercriminals used the following topics for the messages:
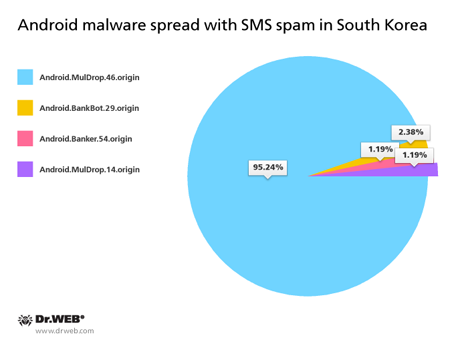
Malicious applications that performed the attacks
Android.MulDrop.46.origin
This is a banking Trojan designed for installing and running other malware, including banking Trojans, on the infected device. It can be distributed under the guise of a popular web browser or another legitimate program.
Android.BankBot.29.origin
The banking Trojan steals authentication information used by the clients of some South Korean financial organizations. Once a popular online banking application is launched, the Trojan replaces its interface with a fake one that prompts the user to enter all confidential data necessary to control their bank account. The entered data is then forwarded to cybercriminals. Under the pretext of subscribing the user to a banking service, it attempts to install the malicious program Android.Banker.32.origin.
Android.MulDrop.14.origin
This Trojan is designed to distribute and install other malware, including various banking Trojans, on Android mobile devices. It is primarily spread in South Korea.
Last month security researchers also registered high activity of Android.BankBot-family banking Trojans, which target customers of credit organizations worldwide. At the beginning of the month, the cybercriminals got arrested; however, distribution of this malware continues by other virus makers.
The number of entries for Android.BankBot Trojans in Dr.Web virus database:
| March 2015 | April 2015 | Growth |
|---|---|---|
| 94 | 110 | +17,02% |
Many of Android.BankBot Trojans can both automatically steal money from users' accounts and block operation of popular anti-virus malware, which makes the malware highly dangerous. Doctor Web experts have issued a special update for their anti-virus products protecting Android devices. The update delivers mechanisms to withstand such attacks; thus, users of Dr.Web for Android and Dr.Web for Android Light are under reliable protection.
[% END %]