January 2015 Android malware overview
February 3, 2015
PRINCIPAL TRENDS IN JANUARY
- Banking Trojans
- New spying Trojans
- Programs in the Google Play catalogue that feature aggressive advertising
- Further proliferation of malware embedded into Android firmware or deployed as pre-installed applications
New entries in the Dr.Web for Android virus database
| Malware | Spyware | Advertising modules | |
|---|---|---|---|
| January 2015 | 351 | 11 | 13 |
Mobile threat of the month
Trojan Android.CaPson.1
- Can spread in firmware modified by intruders.
- A Linux executable that extracts several modules, some of which are encrypted. Once the components are decrypted and loaded into the memory, the Trojan deletes the original files and commences with its malicious activities.
- It covertly sends and intercepts short messages, loads webpages in the browser, transmits information about the infected device to a remote server, and downloads other applications.
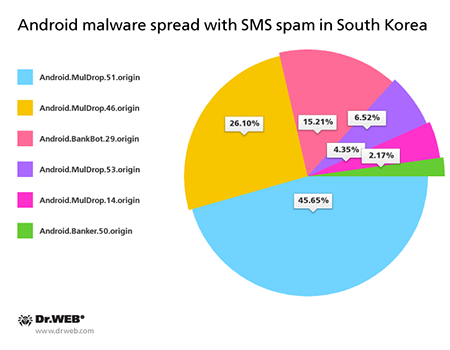
Banking Trojans for Android
In the past month Doctor Web registered the emergence of the latest group of banking Trojans for Android. These malicious applications were particularly active in South Korea where they are spread with unsolicited short messages containing their download links.
Over 40 spam campaigns involved in the spread of several malicious programs were registered
Android.MulDrop malware
Malicious programs designed to distribute and install other Android Trojans on Android-powered devices. South Korean virus makers use these malicious applications to spread various banking Trojans.
Android.BankBot.29.origin
The banking Trojan steals authentication information from customers of South Korean banks. Whenever a user runs a legitimate online banking application, the Trojan replaces its interface with a fake copy that prompts the user to enter all the sensitive information needed to access their bank account. The information entered by the user is transmitted to criminals. Under the pretext of subscribing the user to a banking service, Android.BankBot.29.origin attempts to install the malicious program Android.Banker.32.origin.
Android.Banker.50.origin
A banking Trojan that steals money from accounts associated with Android-powered devices.
Cyberespionage software
Cyberespionage remains a pressing issue for users of mobile devices. In January the Dr.Web virus database was updated with a large number of definitions for a variety of commercial spyware that was designed to spy on the owners of the Android smartphones and tablets it was running on. Along with discovering new species in the known spyware families Program.MobileSpy, Program.Tracer, Program.Highster, Program.OwnSpy, Program.MSpy, and numerous others, Doctor Web security researchers examined new programs of this kind, including Program.ZealSpy.1.origin, Program.LetMeSpy.1.origin and Program.CellSpy.1.origin.
- Program.ZealSpy.1.origin
- Intercepts SMS text and email messages
- Acquires information about phone calls and contacts
- Keeps track of GPS coordinates
- Reads the correspondence maintained via popular messaging programs
- Program.LetMeSpy.1.origin
This program monitors:
- SMS correspondence;
- Phone calls;
- GPS coordinates.
- Program.CellSpy.1.origin
- Intercepts text messages and phone calls
- Acquires the device's GPS coordinates.
- Covertly records audio input from the device's microphone
- Views browser history
Threats in the Google Play catalogue
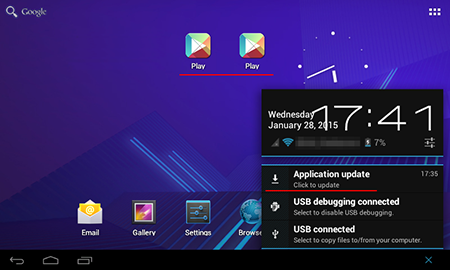
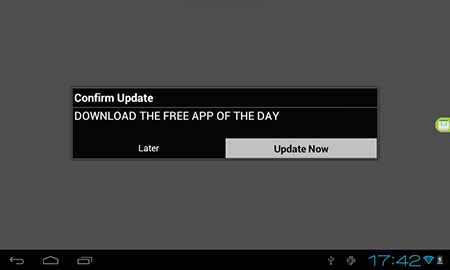
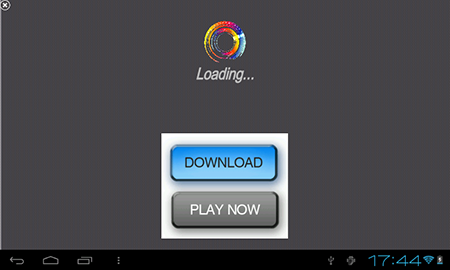
Applications available on Google Play frequently incorporate potentially dangerous and unwanted modules that display annoying ads. Another module of this sort, which was used by some developers of free software, was discovered in January. It entered the Dr.Web virus database as Adware.HideIcon.1.origin.
Adware.HideIcon.1.origin
Advertising module that generates a profit in Android freeware. Incorporates several harmful features.
- Can simulate the download of important files to lure the user into going to a site its makers have been paid to promote.
- Regularly prompts users to install updates that conceal adware.
- Displays annoying ads whenever users run certain applications.
- Deletes the original shortcut icons of the applications it is contained in which makes it hard for inexperienced users to determine the source of the annoying advertisements. The original icons on the home screen are replaced with new ones that lead to various sites that distribute adware.