Doctor Web’s Q3 2025 virus activity review
October 1, 2025
Users whose files were affected by encoder trojans had mostly encountered Trojan.Encoder.35534, Trojan.Encoder.35209, and Trojan.Encoder.35067.
In July, Doctor Web’s experts informed users about the Trojan.Scavenger malware family whose trojans are designed to steal cryptocurrency and passwords. Threat actors distributed these trojans under the guise of mods, cheats, and patches for games. This malware was launched using legitimate apps, including through the exploitation of the DLL Search Order Hijacking vulnerabilities in them.
In August, our malware analysts warned about the spread of Android.Backdoor.916.origin, a multifunctional backdoor for mobile devices that was targeting representatives of Russian business. Cybercriminals remotely controlled this malware and used it to steel confidential data and spy on victims.
That same month, Doctor Web's anti-virus laboratory released a study of a targeted attack committed against a Russian engineering enterprise by the Scaly Wolf hacker group. The threat actors used a variety of malicious instruments, one of the main ones being the Updatar modular backdoor. With its help, the attackers tried to obtain confidential data from infected computers.
In Q3 2025, our Internet analysts detected more fake Telegram messenger websites and a number of fraudulent finance-themed online resources. In addition, over the past three months, our specialists have recorded the emergence of dozens of malicious and unwanted apps on Google Play. Among these were Android.Joker trojans, which subscribe users to paid services, and Android.FakeApp fake programs.
Principal trends in Q3 2025
- The number of threats detected on protected devices decreased
- The number of unique threats attacking users were detected in increased numbers
- More fake Telegram messenger and fraudulent finance-themed websites emerged
- Password- and cryptocurrency-stealing Trojan.Scavenger malware was spotted in the wild
- The backdoor Android.Backdoor.916.origin was used to spy on Russian business representatives and steal confidential data
- Android.MobiDash ad-displaying trojans became the most widespread threat for Android devices
- The activity of Android.HiddenAds adware trojans decreased for the second quarter in a row
- Many threats were detected on Google Play
According to Doctor Web’s statistics service
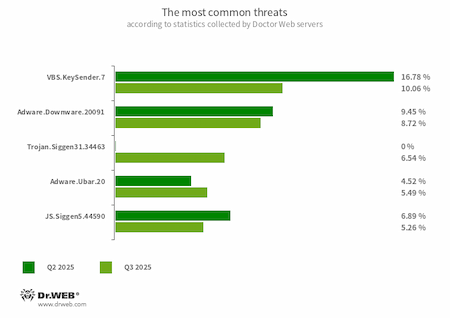
The most common threats in Q3 2025:
- VBS.KeySender.7
- A malicious script that, in an infinite loop, searches for windows containing the text mode extensions, разработчика, and розробника and sends them an Escape key press event, forcibly closing them.
- Adware.Downware.20091
- Adware that often serves as an intermediary installer of pirated software.
- Trojan.Siggen31.34463
- A trojan written in the Go programming language and designed to download various miner trojans and adware into infected systems. This malware is a DLL file located at %appdata%\utorrent\lib.dll. To launch, it exploits a DLL Search Order Hijacking vulnerability in the uTorrent torrent client.
- Adware.Ubar.20
- A torrent client designed to install unwanted programs on a user’s device.
- JS.Siggen5.44590
- Malicious code added to the es5-ext-main public JavaScript library. It shows a specific message if the package is installed on a server with the time zone of a Russian city.
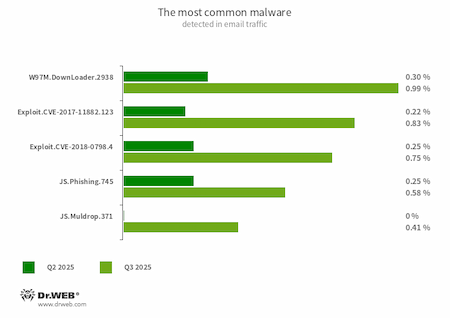
Statistics for malware discovered in email traffic
- W97M.DownLoader.2938
- A family of downloader trojans that exploit vulnerabilities in Microsoft Office documents. They can also download other malicious programs to a compromised computer.
- Exploit.CVE-2017-11882.123
- Exploit.CVE-2018-0798.4
- Exploits designed to take advantage of Microsoft Office software vulnerabilities and allow an attacker to run arbitrary code.
- JS.Phishing.745
- A malicious JavaScript script that generates a phishing web page.
- JS.Muldrop.371
- A malicious JavaScript script that installs a payload into the system.
Encryption ransomware
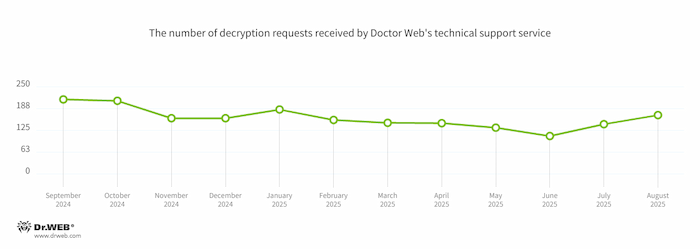
In Q3 2025, the number of requests made to decrypt files affected by encoder trojans increased by 3.02%, compared to Q2 2025.
The dynamics of the decryption requests received by Doctor Web’s technical support service:
The most common encoders of Q3 2025:
- Trojan.Encoder.35534 — 26.99% of user requests
- Trojan.Encoder.35209 — 3.07% of user requests
- Trojan.Encoder.35067 — 2.76% of user requests
- Trojan.Encoder.41542 — 2.15% of user requests
- Trojan.Encoder.29750 — 1.84% of user requests
Network fraud
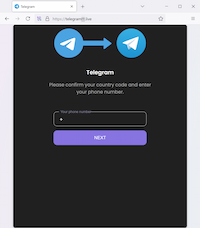
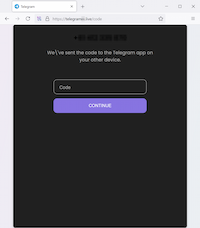
In Q3 2025, Doctor Web’s Internet analysts continued to detect new fake Telegram messenger websites, including those that fraudsters used to try to gain access to user accounts:
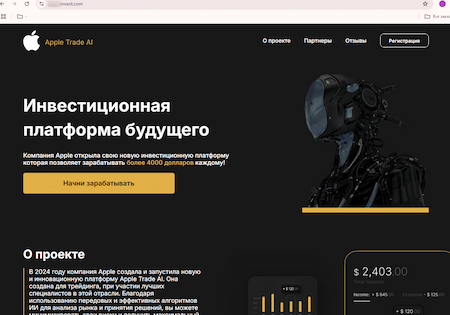
In addition, finance-themed fraudulent sites continued to emerge. One of them lured users to an “investment platform of the future” called Apple Trade AI, which supposedly had been created by the Apple Corporation. Cybercriminals promised potential victims the opportunity to make more than $4,000 a month. To “access” the platform, they were required to register by providing personal information.
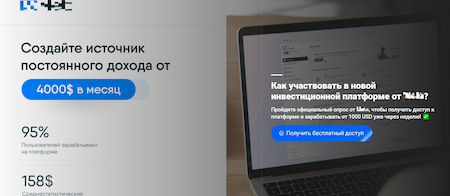
Other Internet resources offered visitors a chance to join a “new investment platform from Meta” and “create a source of constant income, starting from $4,000 a month”. To access the “platform”, users were asked to take a survey and then register.
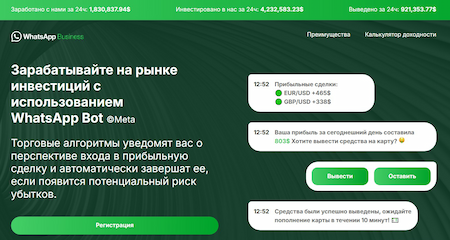
Our experts also discovered more variants of fake investing platforms that allegedly allowed users to make money with the help of trading bots in WhatsApp.
To “work” with the promised services, potential victims had to provide personal data:
A number of fraudulent websites were designed for audiences in specific countries. Some of them were targeting CIS-based users, to whom fraudsters offered the chance to “open a closed investment market” and access some exclusive investments through the INSIDER X financial service. To do so, visitors had to “leave a request” by providing personal data.
In one of the schemes designed for Russian users, cybercriminals asked users to take a survey in order to gain access to an “investment platform” that was supposedly related to large oil and gas companies and the state-backed Gosuslugi (Госуслуги) portal:
Scammers passed off some other sites as legitimate Russian bank services and told users they could register in order to “earn at least 50,000 rubles a week”:
Once again, users from some other countries encountered similar fake websites. On one of them, fraudsters offered users from Kyrgyzstan the opportunity to become part of a people's program and invest in what they claimed was the country’s largest company:
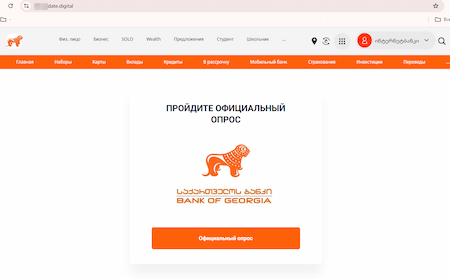
Another site was allegedly tied to a Georgian bank and allowed users to join its “investment platform”:
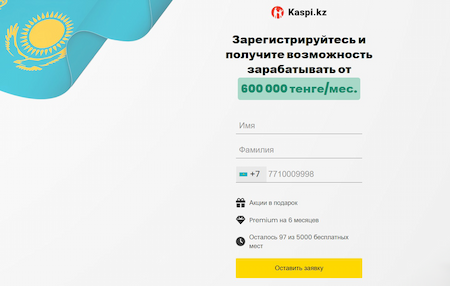
The scammers passed off a similar fake website as belonging to one of the Kazakhstan banks and promised users an income starting from 600,000 tenge per month:
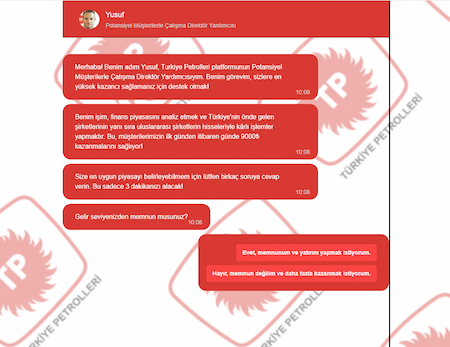
On another site, malicious actors, allegedly on behalf of a Turkish oil and gas company, offered potential victims the opportunity to join an investment platform and make “up to 9,000 Turkish lira a day”:
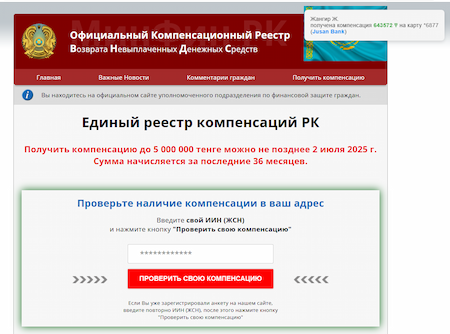
At the same time, fraudsters continued exploiting the topic of all kinds of government payments and compensations. On one of the unwanted sites targeting Kazakhstani users, visitors allegedly could check whether financial compensation was available to them and get up to 5,000,000 tenge:
Find out more about Dr.Web non-recommended sitesMalicious and unwanted programs for mobile devices
According to detection statistics collected by Dr.Web Security Space for mobile devices, in Q3 2025, users most often encountered Android.MobiDash ad-displaying trojans. At the same time, the previously leading Android.HiddenAds trojans dropped to second place, significantly reducing their activity. The third most common threat was Android.FakeApp fake programs.
Compared to the second quarter, the number of Android.BankBot banking trojan detections increased, while the banking trojans Android.Banker and Android.SpyMax were, to the contrary, detected less often.
In August, Doctor Web’s experts informed users about the Android.Backdoor.916.origin multifunctional backdoor that threat actors had used to spy on representatives of Russian business and steal confidential data from them.
Over the course of the last three months, more than 70 malicious and unwanted apps were discovered on Google Play. Among them were Android.Joker trojans, which subscribe users to paid services, Android.FakeApp fake programs, and Program.FakeMoney.16—a piece of software that allegedly allowed users to convert virtual rewards into real money.
The following Q3 2025 events involving mobile malware are the most noteworthy:
- Android.MobiDash adware trojans were more active.
- Android.HiddenAds ad-displaying trojan activity decreased.
- Users encountered Android.BankBot banking trojans more often.
- The number of Android.Banker and Android.SpyMax banking trojan attacks decreased.
- Malicious actors used a multifunctional backdoor Android.Backdoor.916.origin to spy on Russian business representatives.
- Many threats were distributed on Google Play.
To find out more about the security-threat landscape for mobile devices in Q3 2025, read our special overview.