Doctor Web’s Q2 2025 virus activity review
July 1, 2025
Users whose files were affected by encoder trojans had mostly encountered Trojan.Encoder.35534, Trojan.Encoder.35209, and Trojan.Encoder.29750.
In April, Doctor Web’s virus analysts reported on a trojan found in the firmware of a number of Android smartphone models. Cybercriminals used this malware to steal cryptocurrency from their victims. In addition, our specialists discovered a trojan that malicious actors embedded into a version of a popular mapping program; it was used to spy on Russian military personnel.
Over the course of the second quarter, our Internet analysts uncovered many new fraudulent websites. Among them were websites of non-existent educational platforms that supposedly allowed potential victims to undergo online training and improve their qualifications. There were also more investment-themed websites promising quick and easy money.
The detection statistics on mobile devices showed a decrease in activity of the part of Android.HiddenAds ad-displaying trojans. However, this malware family remains the most widespread Android threat. At the same time, our virus laboratory detected many new threats on Google Play.
Principal trends in Q2 2025
- The number of threats detected on protected devices decreased
- Unique threats used in attacks were detected in decreased numbers
- Many fraudulent websites, allegedly related to the education sector and finances, emerged
- A spyware trojan attack targeting Russian military personnel was detected; the attack exploited popular mapping software for Android devices
- A trojan designed to steal cryptocurrency was found in the firmware of a variety of Android smartphones
- Android.HiddenAds adware trojans remain among the most widespread Android threats
- More malicious and unwanted programs were detected on Google Play
According to Doctor Web’s statistics service
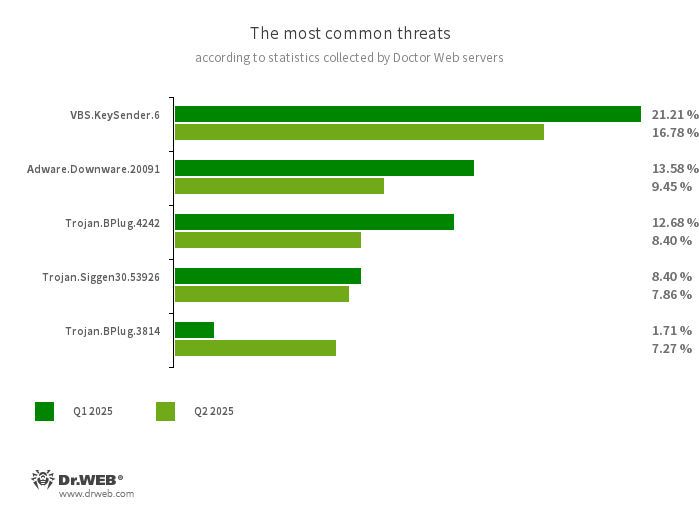
The most common threats in Q2 2025:
- VBS.KeySender.6
- A malicious script that, in an infinite loop, searches for windows containing the text mode extensions, разработчика, and розробника and sends them an Escape key press event, forcibly closing them.
- Adware.Downware.20091
- Adware that often serves as an intermediary installer of pirated software.
- Trojan.BPlug.4242
- Trojan.BPlug.3814
- The detection name for malicious components of the WinSafe browser extension. These components are JavaScript files that display intrusive ads in browsers.
- Trojan.Siggen30.53926
- The detection name of an Electron framework host process modified by threat actors. It mimics a Steam application component (Steam Client WebHelper) and loads a JavaScript backdoor.
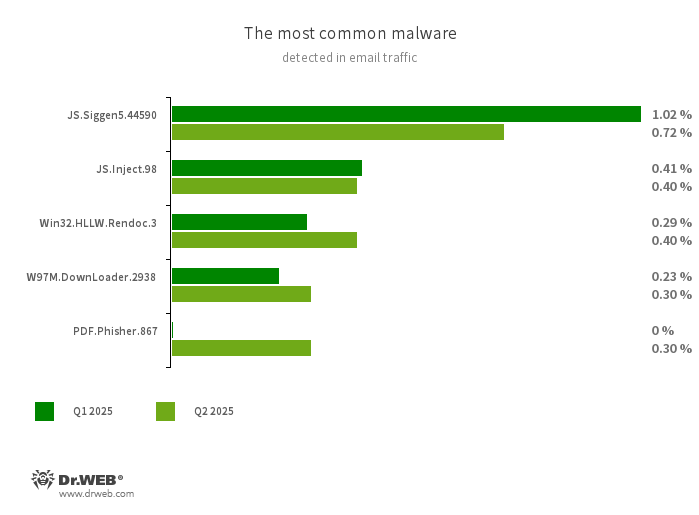
Statistics for malware discovered in email traffic
- JS.Siggen5.44590
- Malicious code added to the es5-ext-main public JavaScript library. It shows a specific message if the package is installed on a server with the time zone of a Russian city.
- JS.Inject
- A family of malicious JavaScripts that inject a malicious script into the HTML code of webpages.
- Win32.HLLW.Rendoc.3
- A network worm that spreads via removeable storage media and other channels.
- W97M.DownLoader.2938
- A family of downloader trojans that exploit vulnerabilities in Microsoft Office documents. They can also download other malicious programs to a compromised computer.
- PDF.Phisher.867
- PDF documents used in phishing newsletters.
Encryption ransomware
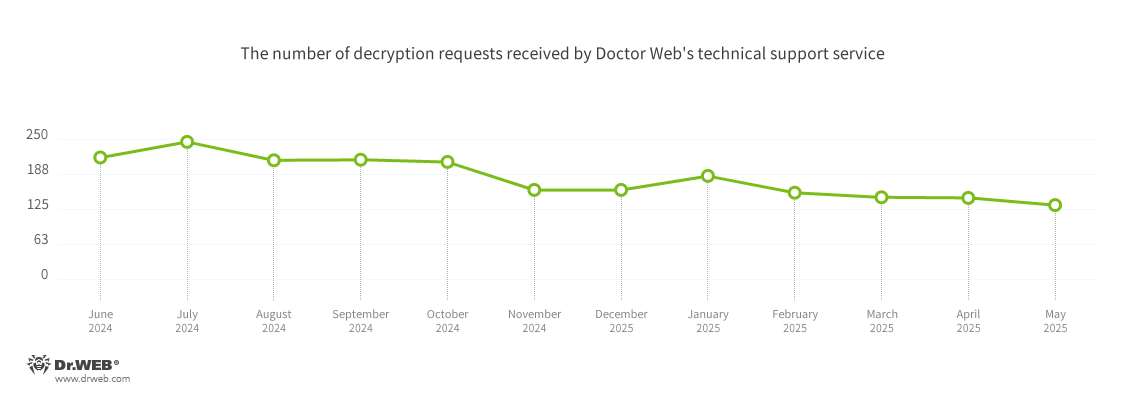
In Q2 2025, the number of requests made to decrypt files affected by encoder trojans decreased by 14.65%, compared to Q1 2025.
The dynamics of the decryption requests received by Doctor Web’s technical support service:
The most common encoders of Q2 2025:
- Trojan.Encoder.35534 — 24.41% of user requests
- Trojan.Encoder.35209 — 4.41% of user requests
- Trojan.Encoder.29750 — 2.71% of user requests
- Trojan.Encoder.35067 — 2.71% of user requests
- Trojan.Encoder.41868 — 2.71% of user requests
Network fraud
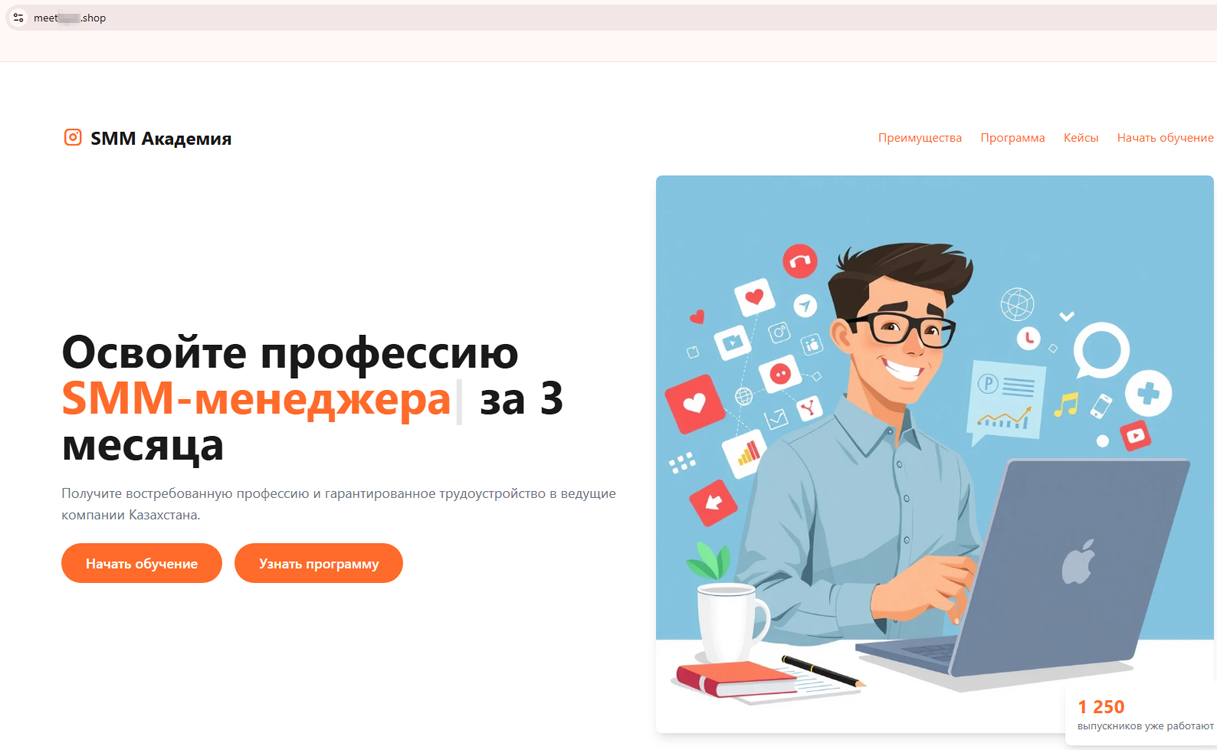
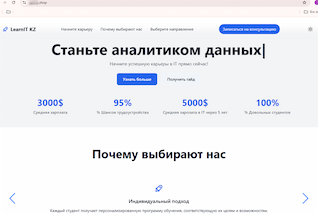
Over the course of the second quarter, Doctor Web’s Internet analysts detected many fraudulent websites supposedly related to the education sector. Online resources offering training in various professions became widespread. For example, the SMM Академия (“SMM Academy”) and LearnIT KZ platforms, designed for Kazakhstani users, supposedly allowed them to “master the SMM manager profession in 3 months” and “become a data analyst”.
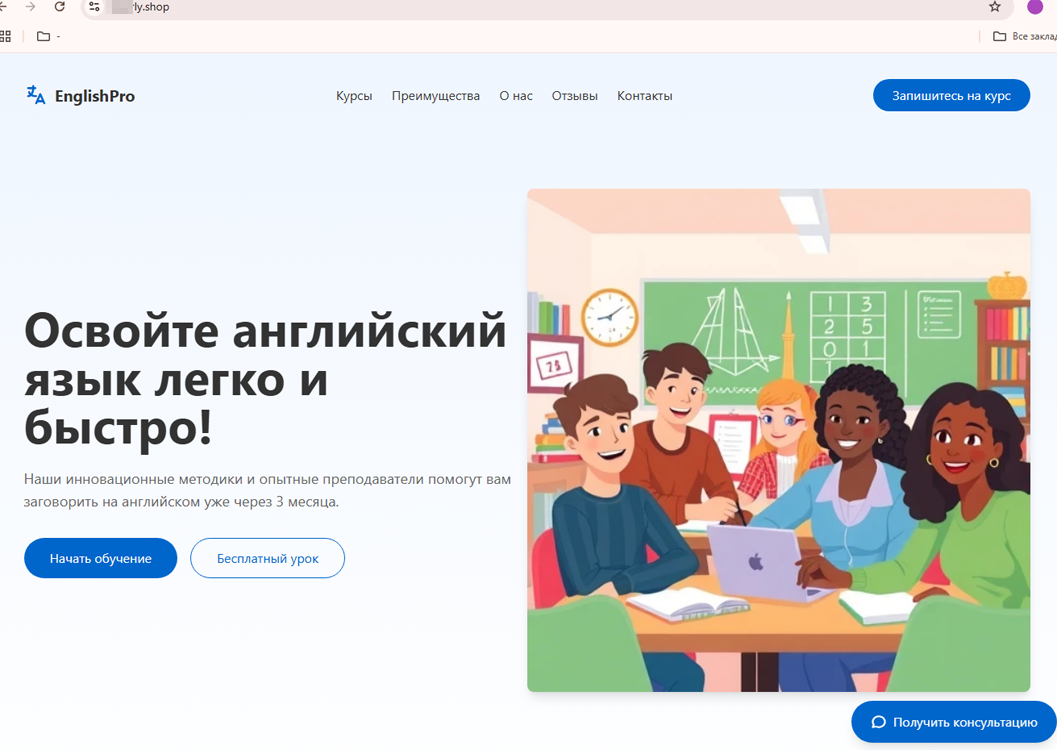
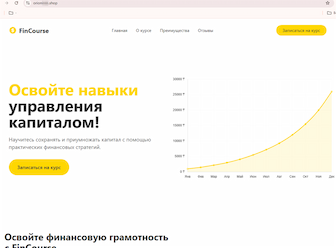
On other websites, potential victims were allegedly able to access various courses. Among them were courses for learning English and for gaining capital management skills—from the EnglishPro and FinCourse “platforms”, respectively:
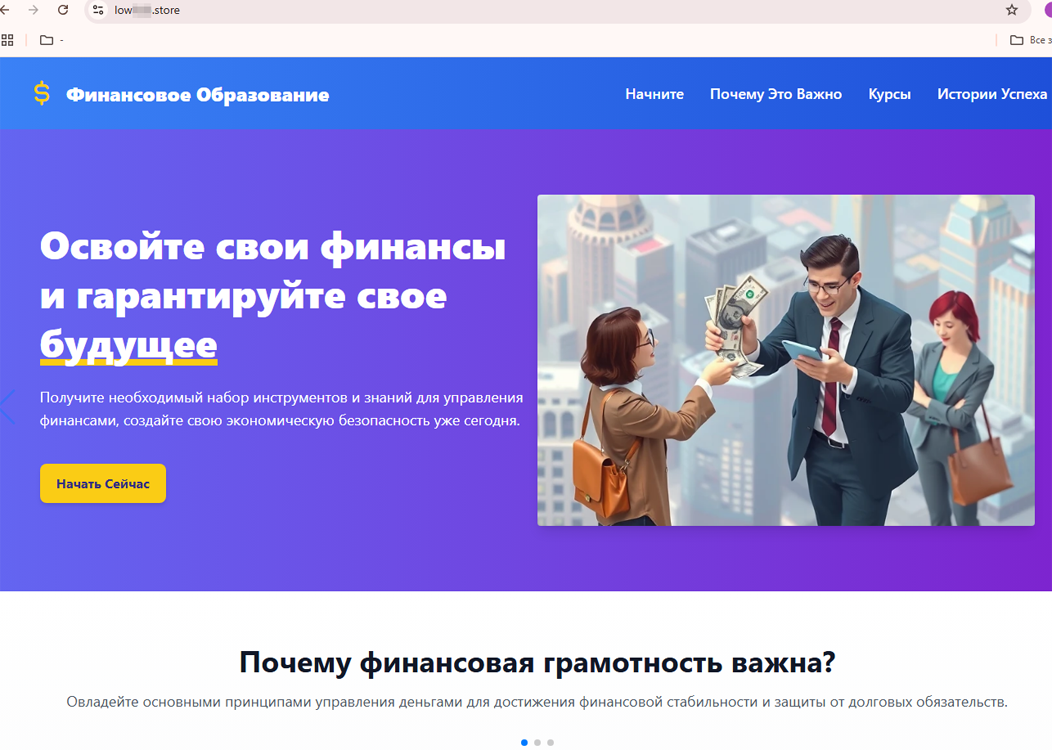
And the fraudulent website of a certain service called Финансовое Образование (“Financial Education”) could supposedly help users improve their financial literacy. It offered visitors the chance to “master their finances and guarantee their future”:
To “access” their advertised services, such websites ask users to register an account by providing personal data, like their name, mobile phone number, email address, etc. Such data accumulates in the criminals’ hands and can later be used in various fraudulent schemes.
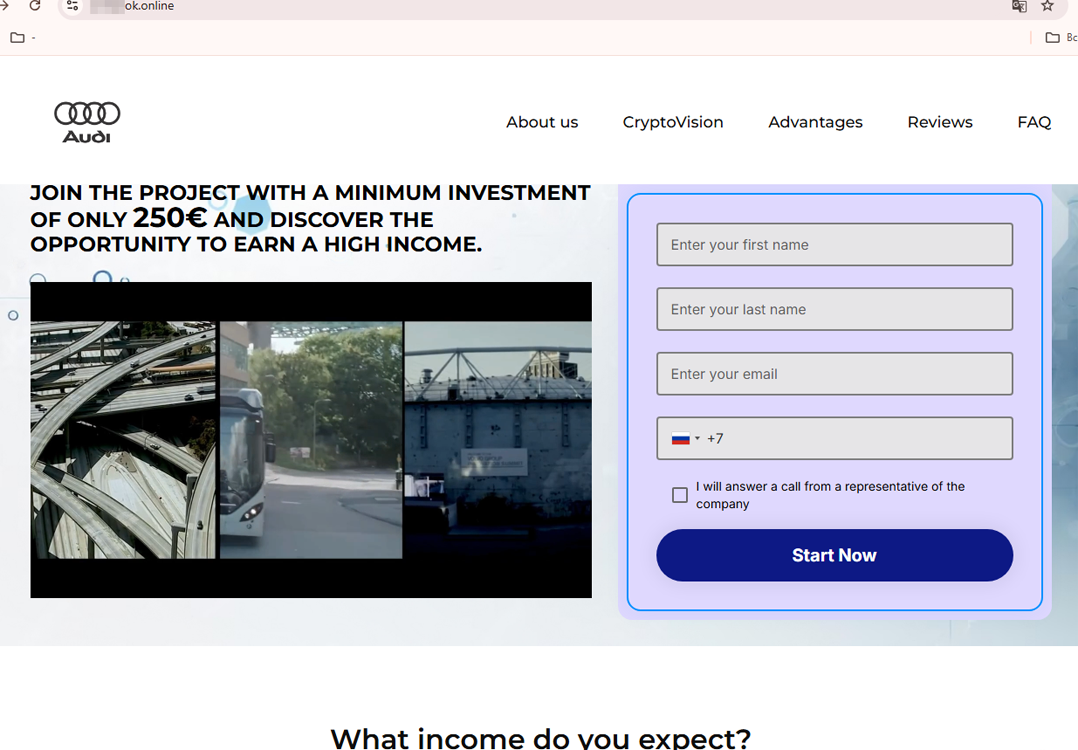
At the same time, new fraudulent websites appeared for pseudo-investment projects that cybercriminals often presented as allegedly being related to well-known companies and services. For instance, one offered users the opportunity to become participants in an innovative project based on AI (artificial intelligence) technologies. This “project” was passed off as a service from the Audi automobile concern and supposedly allowed cryptocurrencies to be traded automatically and a guaranteed high income to be received. For “accessing” the service, a starting sum of €250 was required.
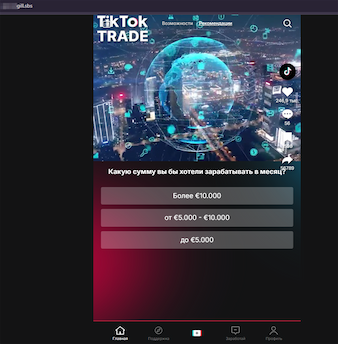
Another “investment project” was allegedly related to the TikTok social network. Visitors to the fraudulent website were asked to complete a short survey and then provide personal information for registering and accessing the promised service:
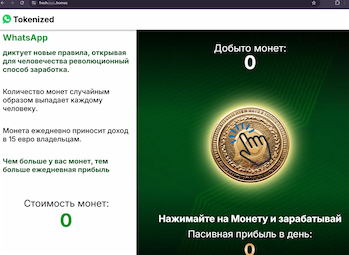
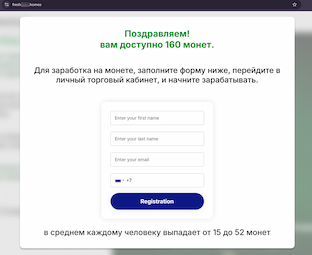
Moreover, other fraudulent websites were discovered that were camouflaged as official online resources for the WhatsApp messenger. One of them offered visitors the opportunity to receive digital coins, each of which “brings the owner €15 a day”. The user supposedly received 160 of these coins, but to begin “earning money on them”, they were asked to register an account by providing personal data. In reality, the potential victim did not get any digital assets, and their data ended up in the hands of the scammers.
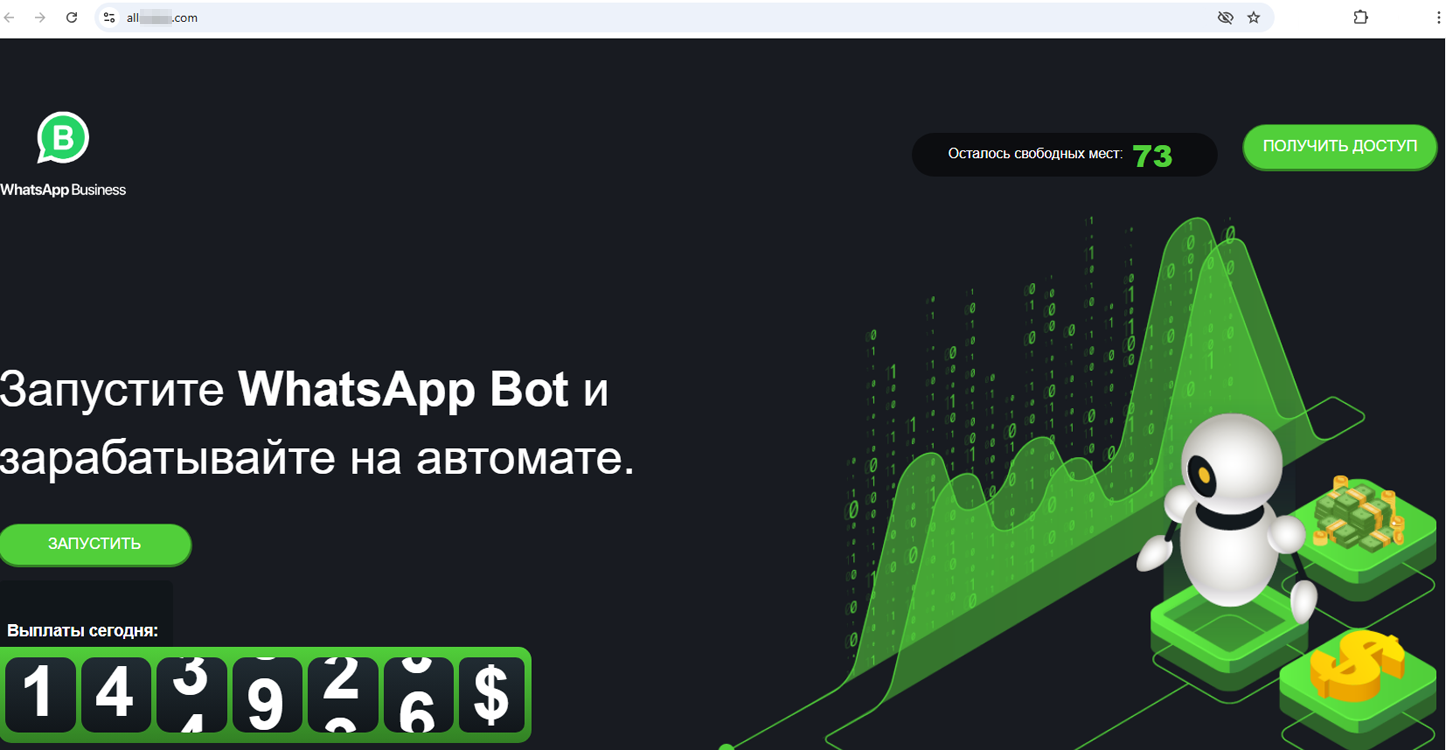
Another fake WhatsApp website supposedly granted access to yet another trading bot, based on some so-called unique developments. Users were asked to “run the WhatsApp Bot and make money automatically”. For this, they were traditionally required to register by indicating their personal data, which was then transferred to the threat actors.
Fraudsters also targeted users from specific countries. For example, Russian citizens could encounter websites offering them the opportunity to “make their dreams come true” with the help of this or that investment service. Malicious actors utilized the same template to design such websites, only changing the appearance and the names of the non-existent projects.
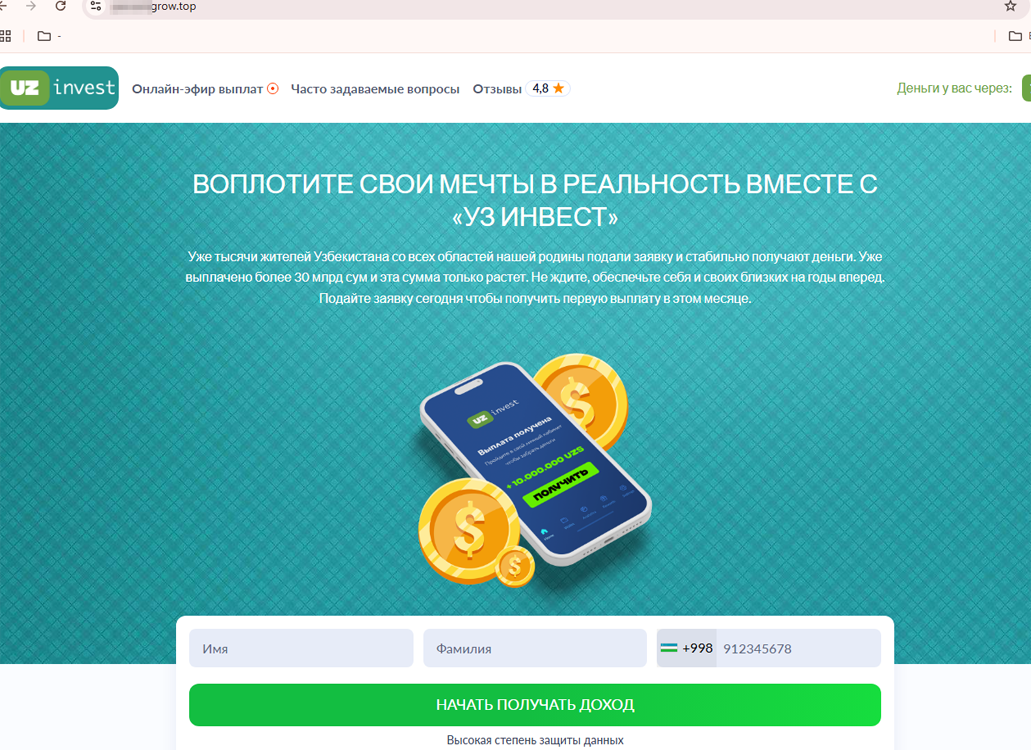
It is noteworthy that websites based on the same template were also created for residents of other countries, for example, Uzbekistan:
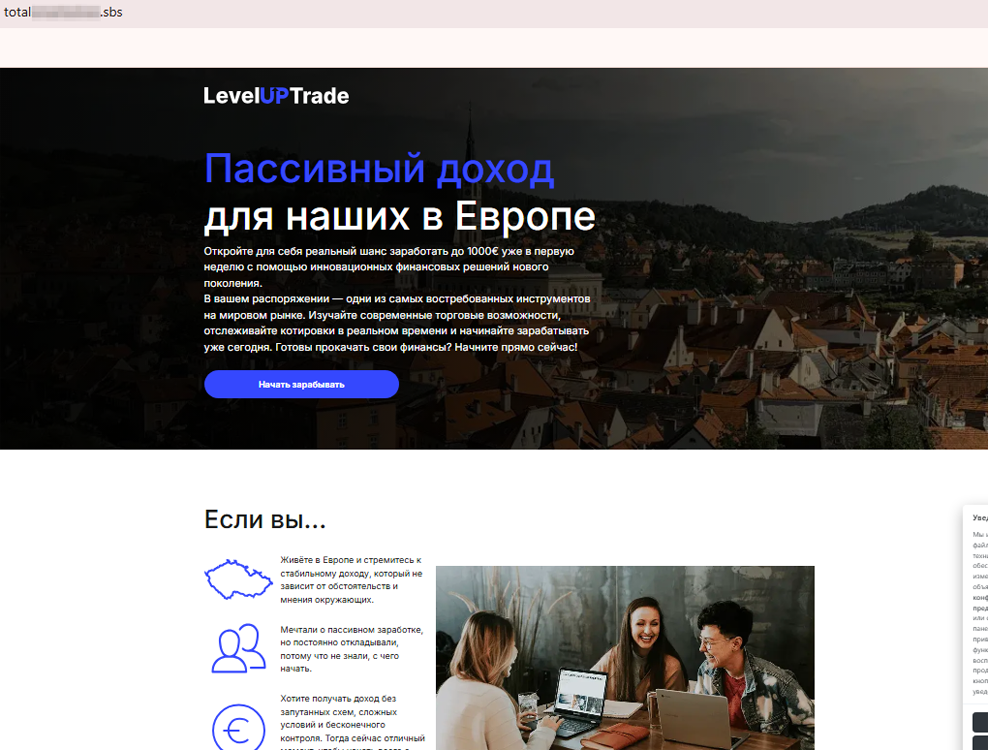
One fraudulent website that was discovered lured Russian-speaking users living in Europe. On this website, cybercriminals promised potential victims a passive income of up to €1000 per week “with the help of innovative, new-generation financial solutions” from some platform called LevelUPTrade:
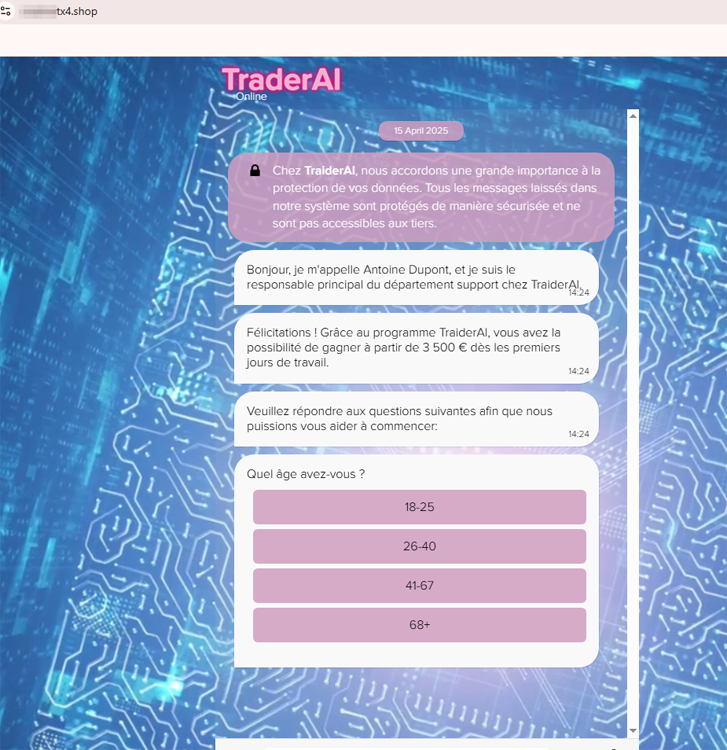
French users could become victims of malicious actors offering the chance to access the non-existent TraderAI automated trading software. With its help, potential victims allegedly had the opportunity to earn a hefty sum, starting from €3500:
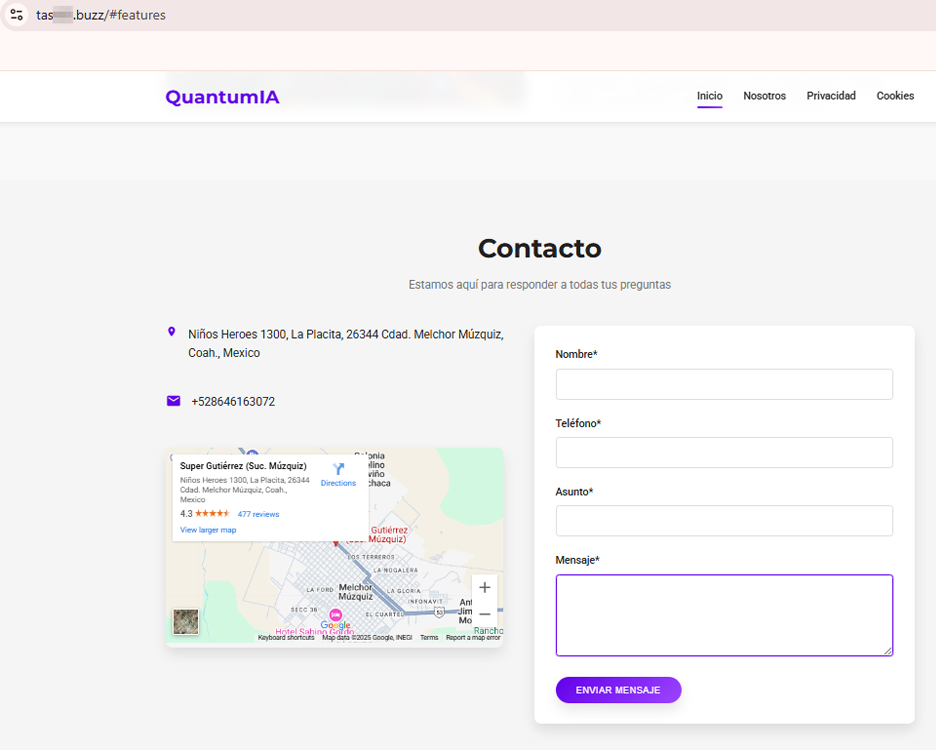
For Mexican citizens, scammers prepared an “intellectual trading system” called QuantumIA. This is one of many variants of the well-known pseudo-trading system known as Quantum System or QuantumAI, which supposedly allows automatic trading to take place in financial markets using quantum computing and artificial intelligence technologies.
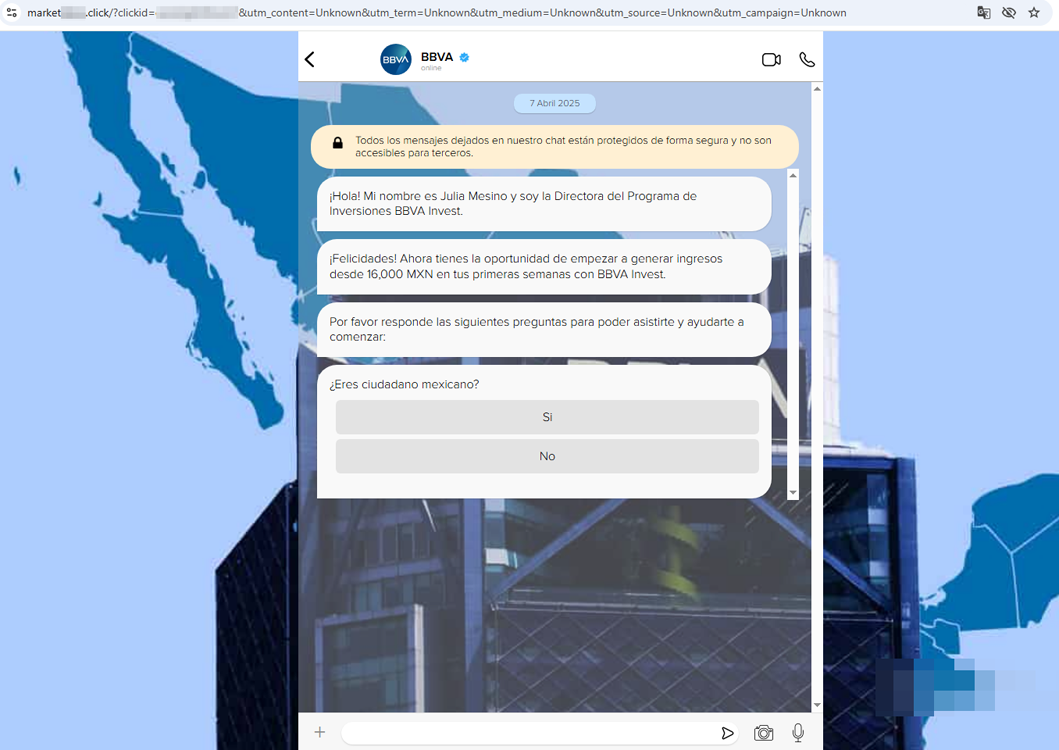
On another website, fraudsters, allegedly on behalf of a large bank, offered Mexican users some investment services. Potential victims were promised that they could make 16,000 Mexican pesos within a short period of time after registering. For this, they were asked to provide their personal data.
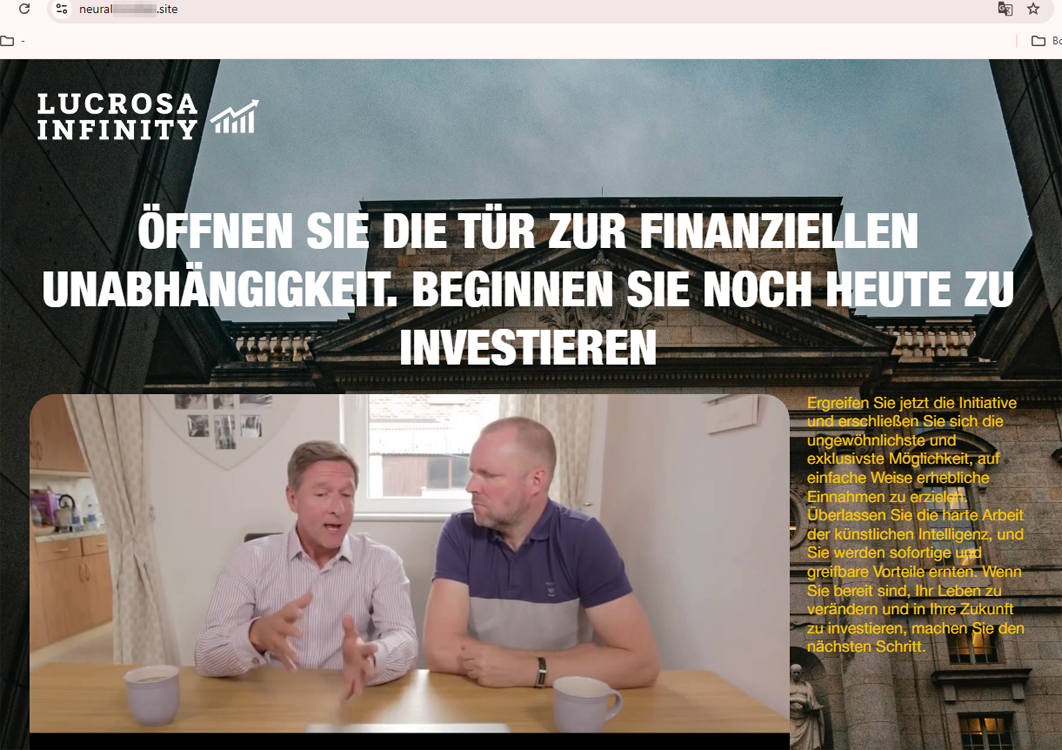
German users risked falling victim to the fake trading platform Lucrosa Infinity. Its image has been exploited in one form or another by cybercriminals for several years. On one fraudulent website, threat actors offered users the opportunity to “start investing and open the door to financial independence”.
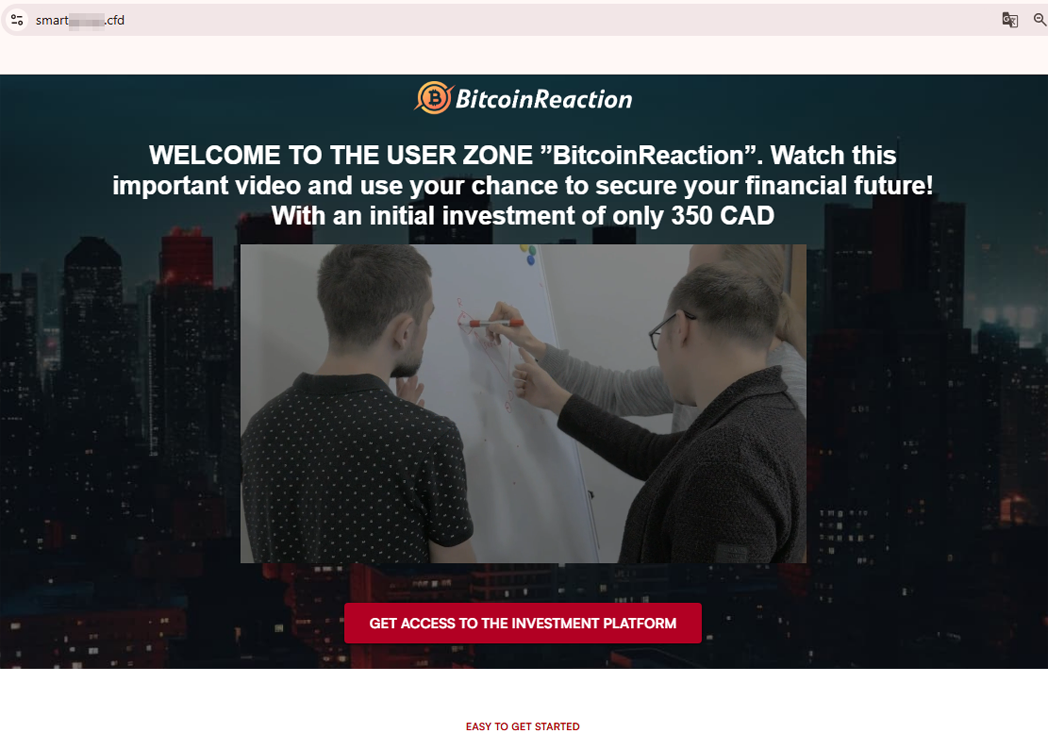
Cybercriminals also offered Canadian users the opportunity to use “unique” services that allegedly provide high income through investments and cryptocurrency trading. Among the uncovered fraudulent websites, for example, were those advertising “platforms” like BitcoinFusionPro and BitcoinReaction. These supposedly allowed clients to make at least 1,000 Canadian dollars per day by investing “only” 350 dollars:
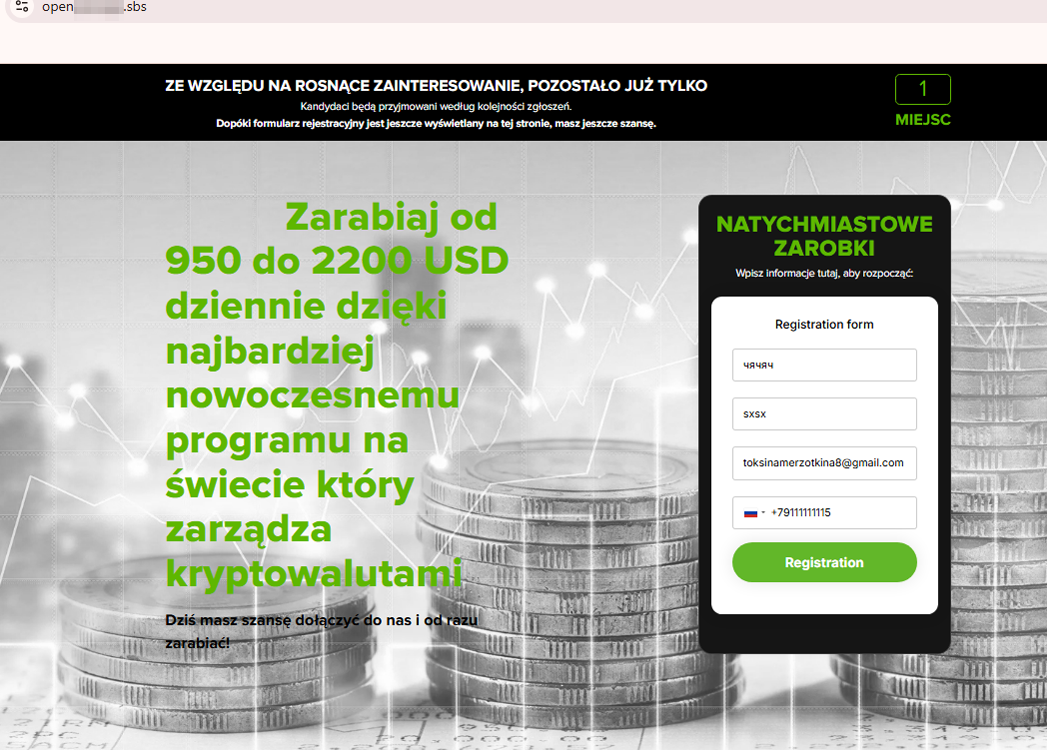
Users from Poland also encountered similar websites. On one of them, scammers promised their potential victims earnings from $950 to $2,200 a day with “the most advanced cryptocurrency management software in the world”:
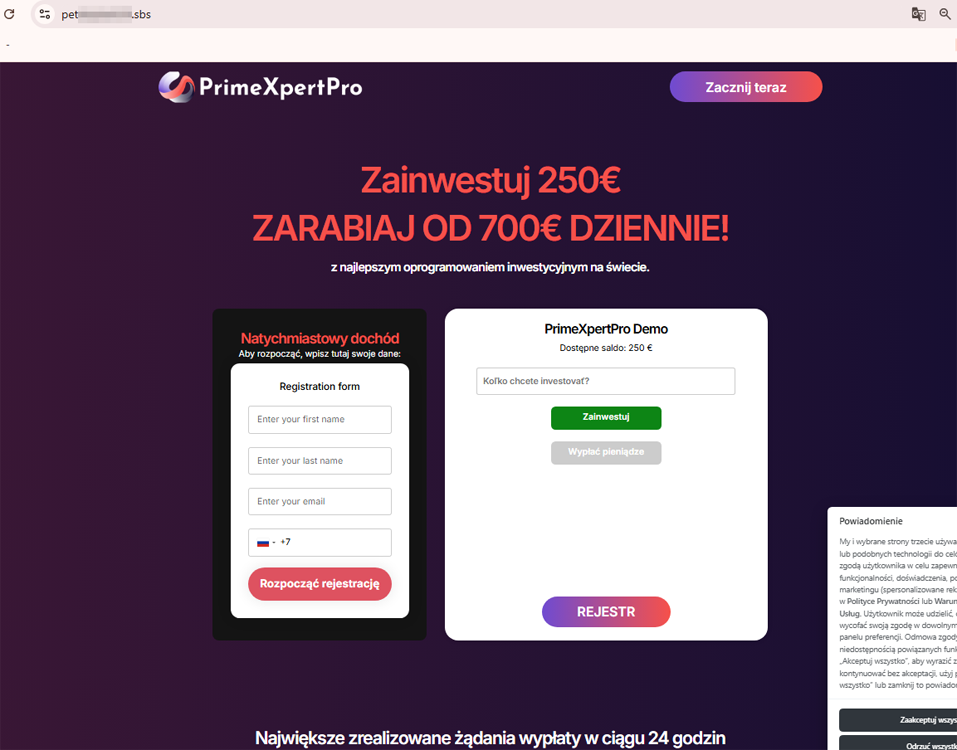
Another website offered them €250 to invest and then earn €700 daily:
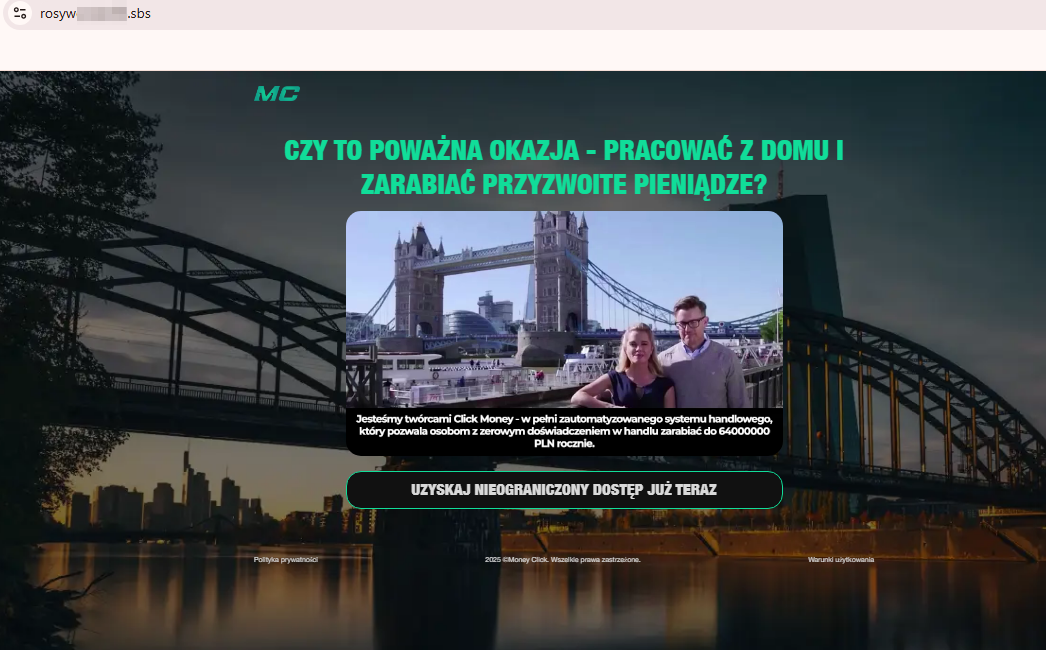
One fraudulent website promised Polish users “the opportunity to work from home and make decent money” thanks to the automated system Click Money. With its help, people without trading experience could allegedly earn up to 64,000,000 Polish zlotys annually:
Malicious and unwanted programs for mobile devices
According to detection statistics collected by Dr.Web Security Space for mobile devices, in Q2 2025, Android.HiddenAds ad-displaying trojans were most commonly detected on protected devices. Compared to the previous quarter, users encountered them somewhat less frequently. Next came adware trojans from the Android.MobiDash family and Android.FakeApp malicious fake programs; the activity of the former increased, while that of the latter decreased.
Mixed dynamics were also observed with banking trojans. For example, more attacks by representatives of the Android.Banker family were recorded. At the same time, trojans from the Android.BankBot and Android.SpyMax families were detected less often on protected devices.
In the second quarter, Doctor Web’s specialists discovered the Android.Clipper.31 trojan in the firmware of a number of Android smartphone models. This malicious app was hidden in one of the WhatsApp messenger versions modified by attackers and was used to steal cryptocurrency from the owners of infected devices. Moreover, our virus analysts uncovered the Android.Spy.1292.origin malicious program. Cybercriminals embedded it into one version of Alpine Quest mapping software and used it to spy on Russian military personnel.
Over the course of the last 3 months, dozens of threats have been detected on Google Play. Among them were malicious fake apps from the Android.FakeApp family and new unwanted ad-displaying software Adware.Adpush.21912.
The following Q2 2025 events involving mobile malware are the most noteworthy:
- Android.HiddenAds ad-displaying trojans were less active.
- Android.MobiDash adware trojan activity increased.
- Android.Banker banking trojans were detected more often on protected devices, compared to the first quarter.
- The number of Android.BankBot and Android.SpyMax banking trojan attacks decreased.
- A trojan designed to steal cryptocurrency was found in the firmware of several Android smartphone models.
- A spyware trojan targeting Russian military personnel was discovered.
- New threats emerged on Google Play.
To find out more about the security-threat landscape for mobile devices in Q2 2025, read our special overview.