Doctor Web’s Q1 2025 virus activity review
March 27, 2025
In email traffic, trojan droppers and downloaders, adware software, malicious scripts, and trojans designed to run various threats on attacked computers were most frequently detected.
Users whose files were affected by encoder trojans had mostly encountered Trojan.Encoder.35534, Trojan.Encoder.35209, and Trojan.Encoder.35067.
In January, Doctor Web’s virus laboratory uncovered an active Monero cryptocurrency mining campaign using many different trojans. To conceal some of them, threat actors utilized steganography, a technique that allows some data to be hidden within other data—for example, inside images.
At the same time, over the course of the first quarter, our Internet analysts detected an increase in the number of fraudulent websites aimed at stealing Telegram messenger user accounts.
In the mobile threats department, Doctor Web’s specialists observed increased activity on the part of adware trojans and some banking trojans used to target the Android OS. In addition, they uncovered dozens of new malicious apps on Google Play.
Principal trends in Q1 2025
- Threats were detected on protected devices in increasing numbers.
- The quantity of unique threats used in attacks decreased.
- Phishing sites designed to steal Telegram accounts became more prevalent.
- Several widespread ad-displaying and banking trojan families, used to target the Android operating system, heightened their activity.
- New malware emerged on Google Play.
According to Doctor Web’s statistics service
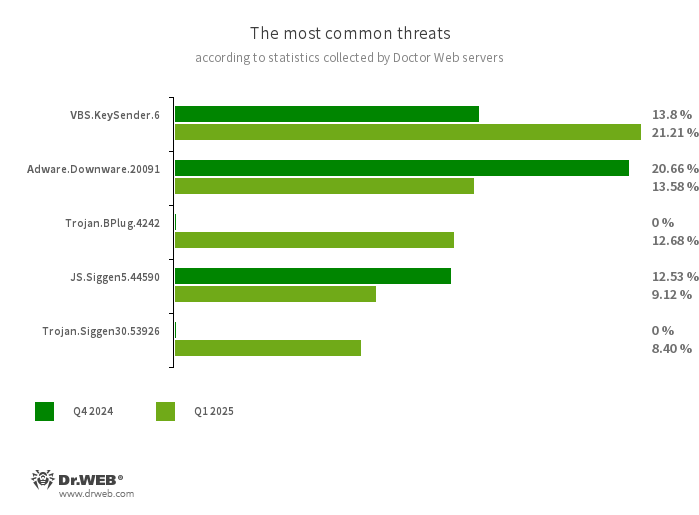
The most common threats in Q1 2025:
- VBS.KeySender.6
- A malicious script that, in an infinite loop, searches for windows containing the text mode extensions, разработчика, and розробника and sends them an Escape key press event, forcibly closing them.
- Adware.Downware.20091
- Adware that often serves as an intermediary installer of pirated software.
- Trojan.BPlug.4242
- The detection name for malicious components of the WinSafe browser extension. These components are JavaScript files that display intrusive ads in browsers.
- JS.Siggen5.44590
- Malicious code added to the es5-ext-main public JavaScript library. It shows a specific message if the package is installed on a server with the time zone of a Russian city.
- Trojan.Siggen30.53926
- The detection name of an Electron framework host process modified by threat actors. It mimics a Steam application component (Steam Client WebHelper) and loads a JavaScript backdoor.
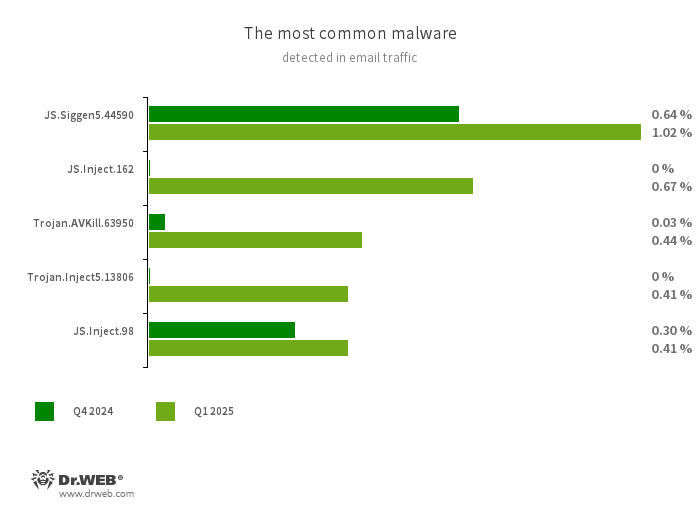
Statistics for malware discovered in email traffic
- JS.Siggen5.44590
- Malicious code added to the es5-ext-main public JavaScript library. It shows a specific message if the package is installed on a server with the time zone of a Russian city.
- JS.Inject
- A family of malicious JavaScripts that inject a malicious script into the HTML code of webpages.
- Trojan.AVKill.63950
- This is a dropper that installs the JS.BackDoor.42 backdoor on computers running the Windows operating system.
- Trojan.Inject5.13806
- A malicious program for Windows-based computers that was created using the AutoIt scripting language. It launches several system processes and injects the Trojan.Fbng spyware trojan into them. The attackers can use the latter as banking malware and for other purposes.
Encryption ransomware
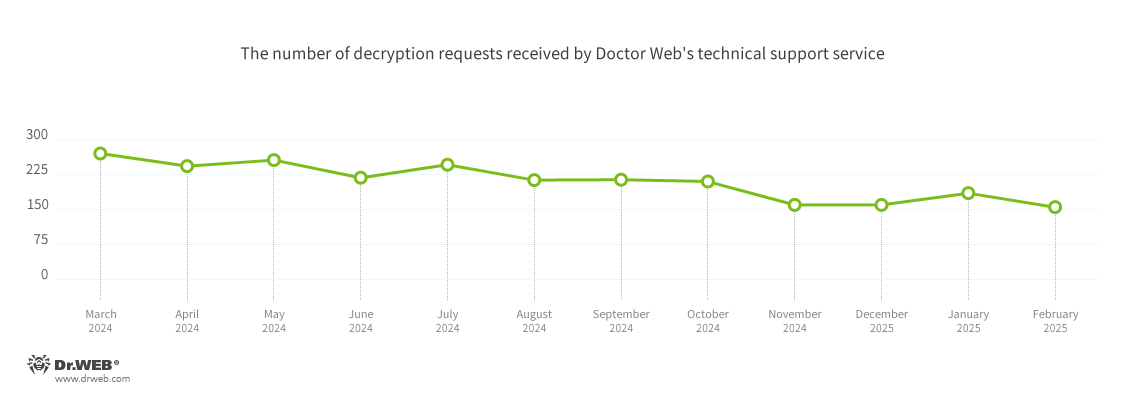
In Q1 2025, the number of requests made to decrypt files affected by encoder trojans decreased by 9.34%, compared to Q4 2024.
The dynamics of the decryption requests received by Doctor Web’s technical support service:
The most common encoders of Q1 2025:
- Trojan.Encoder.35534 — 11.89% of user requests
- Trojan.Encoder.35209 — 5.95% of user requests
- Trojan.Encoder. 35067 — 3.57% of user requests
- Trojan.Encoder.38200 — 2.38% of user requests
- Trojan.Encoder.37369 — 1.98% of user requests
Network fraud
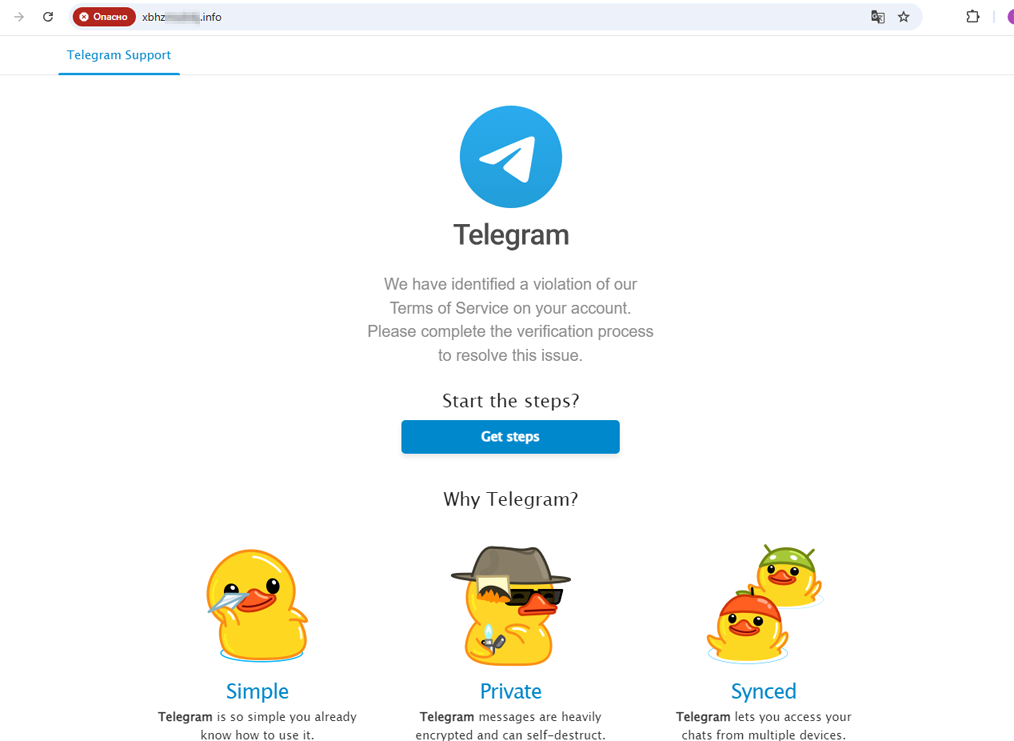
In Q1 2025, Doctor Web’s Internet analysts observed the emergence of many new phishing websites designed to steal Telegram messenger user accounts. Among the most common variants were fake login pages and support pages that informed users about alleged problems due to some violation of the terms of service.
Fake sites of online stores were widespread once again. On these, cybercriminals asked potential victims to log in to their accounts.
A phishing authorization form on a fake website of one Russian online store
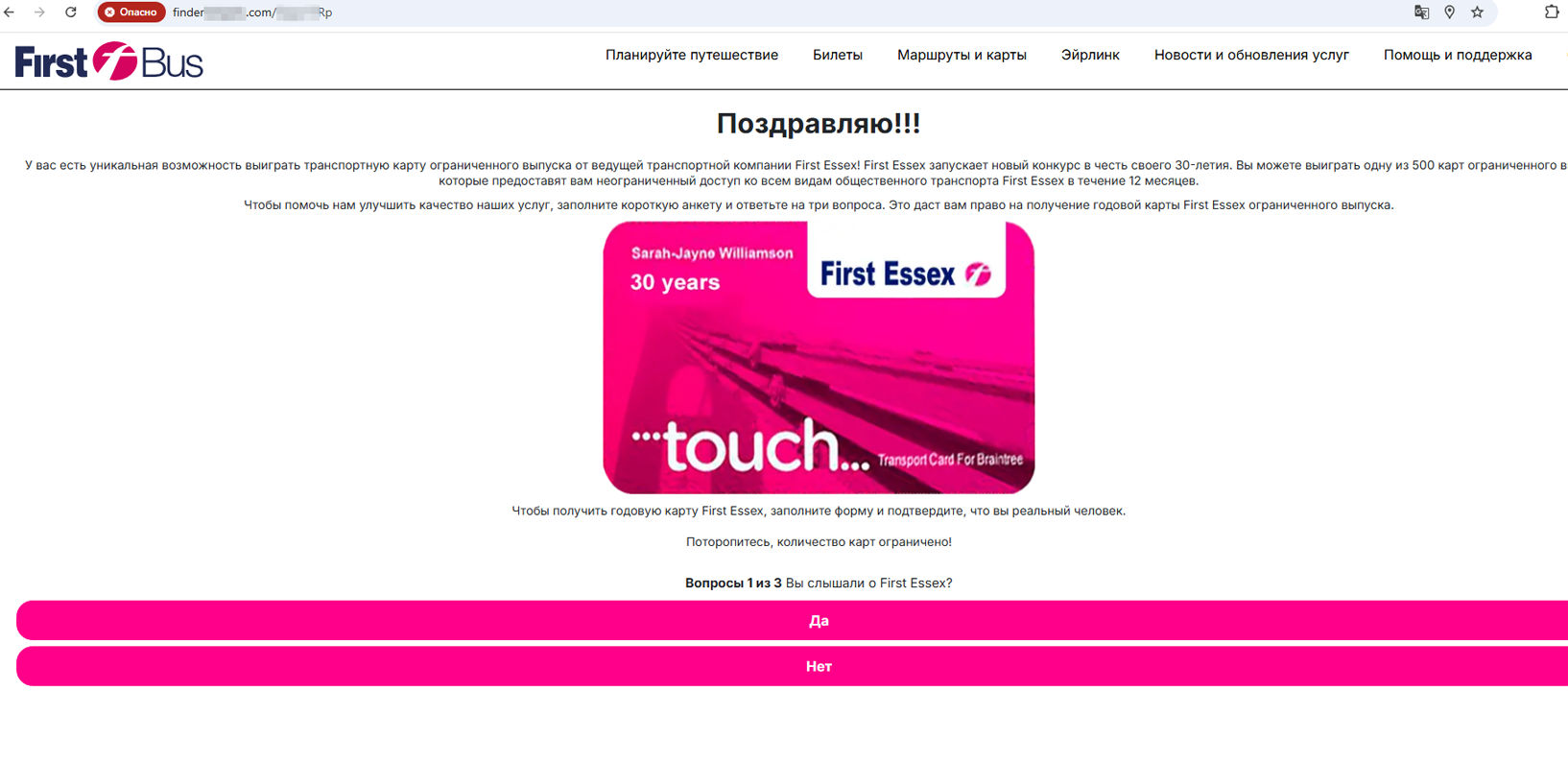
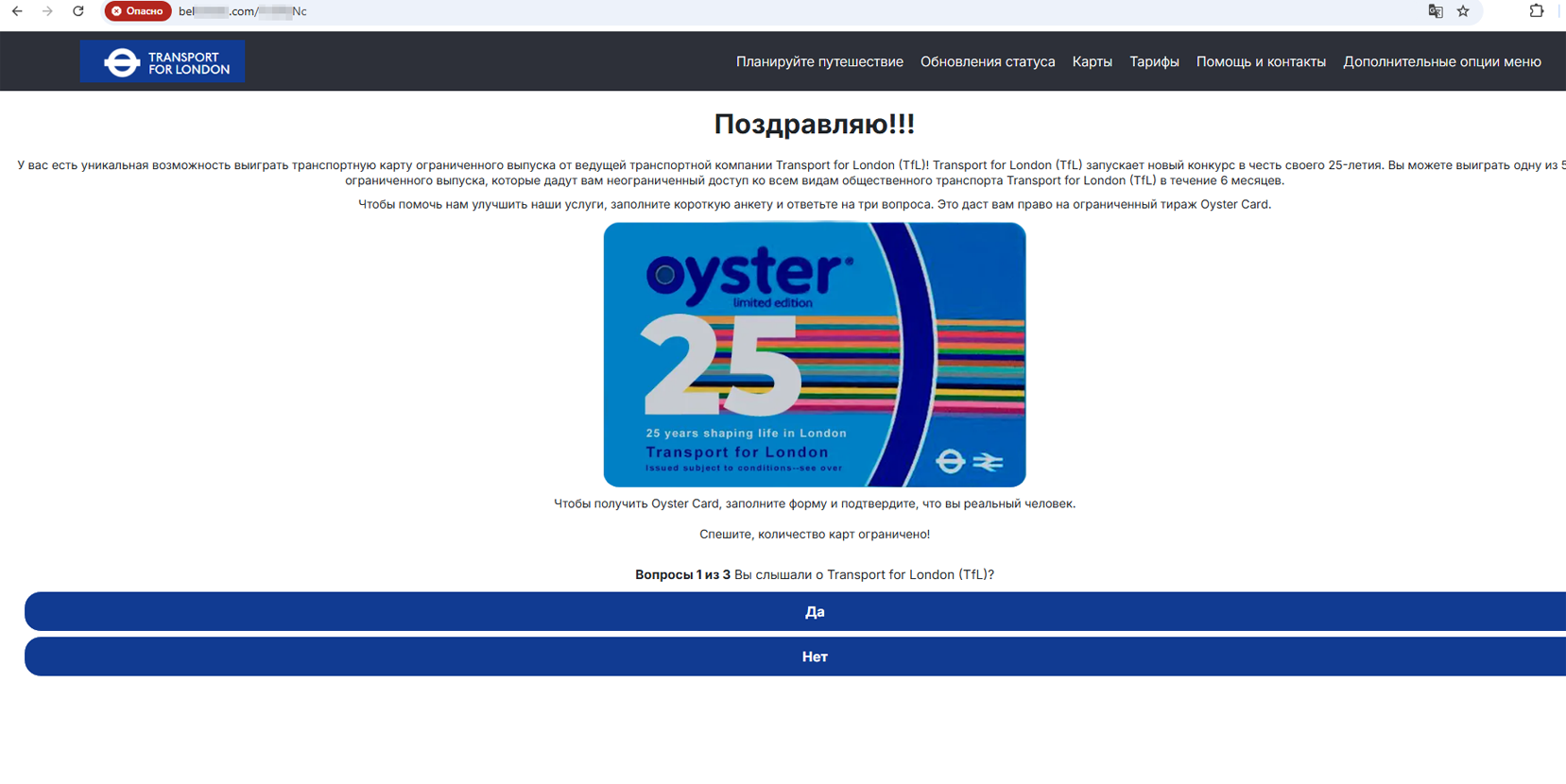
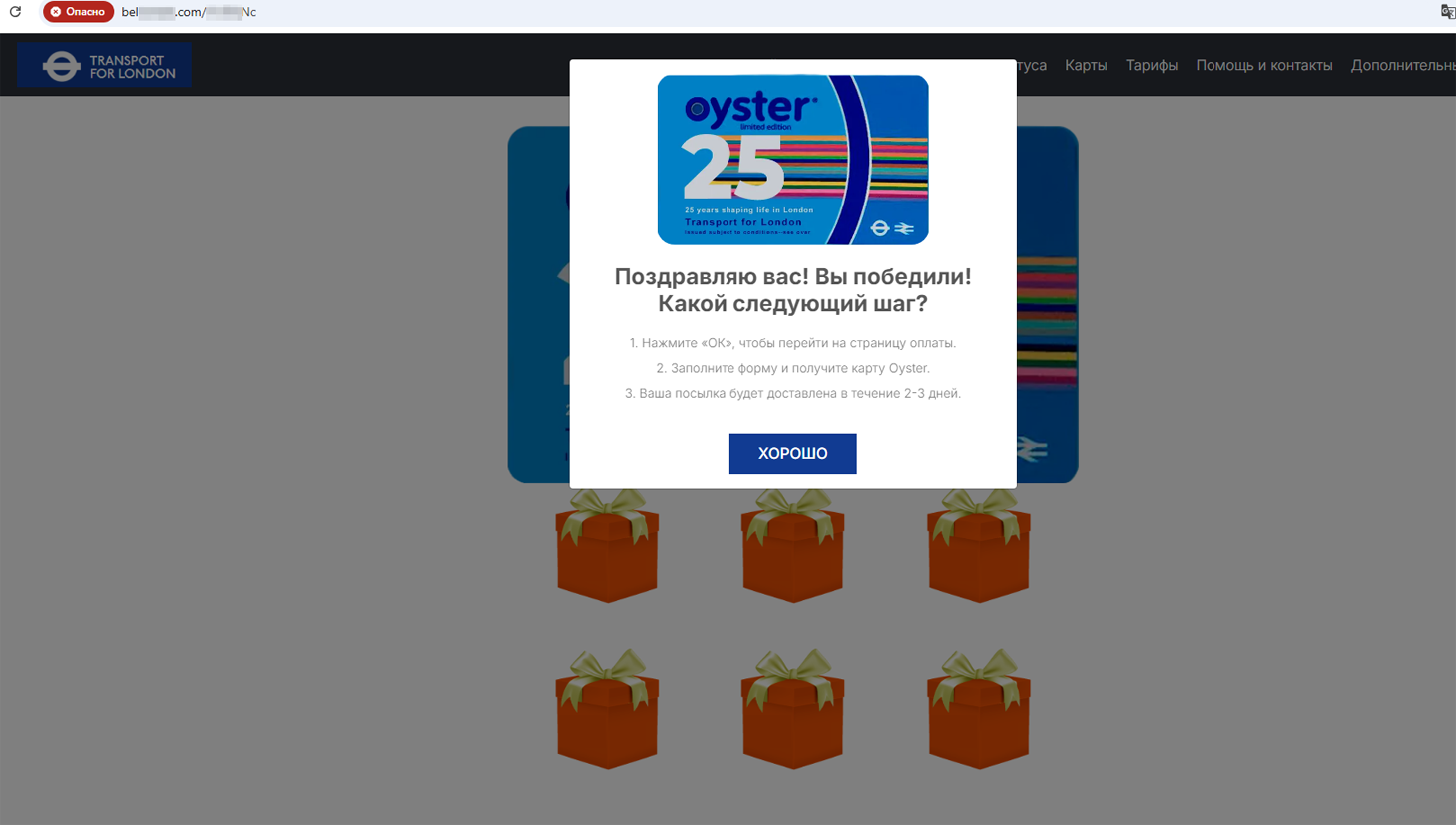
Our specialists continued detecting fraudulent sites with all sorts of “great offers”, such as quick or easy ways to make money; others were about receiving certain gifts, participating in promotions, etc. One of the schemes, for instance, targeted residents of Great Britain, offering them the chance to obtain “limited edition” transportation cards, which were supposedly dedicated to the anniversaries of various carriers and would allow them to use public transport services free of charge for a long period of time.
Fraudulent sites offering the chance to obtain “special” First Essex and Oyster transportation cards that allow public transport services to be used for free
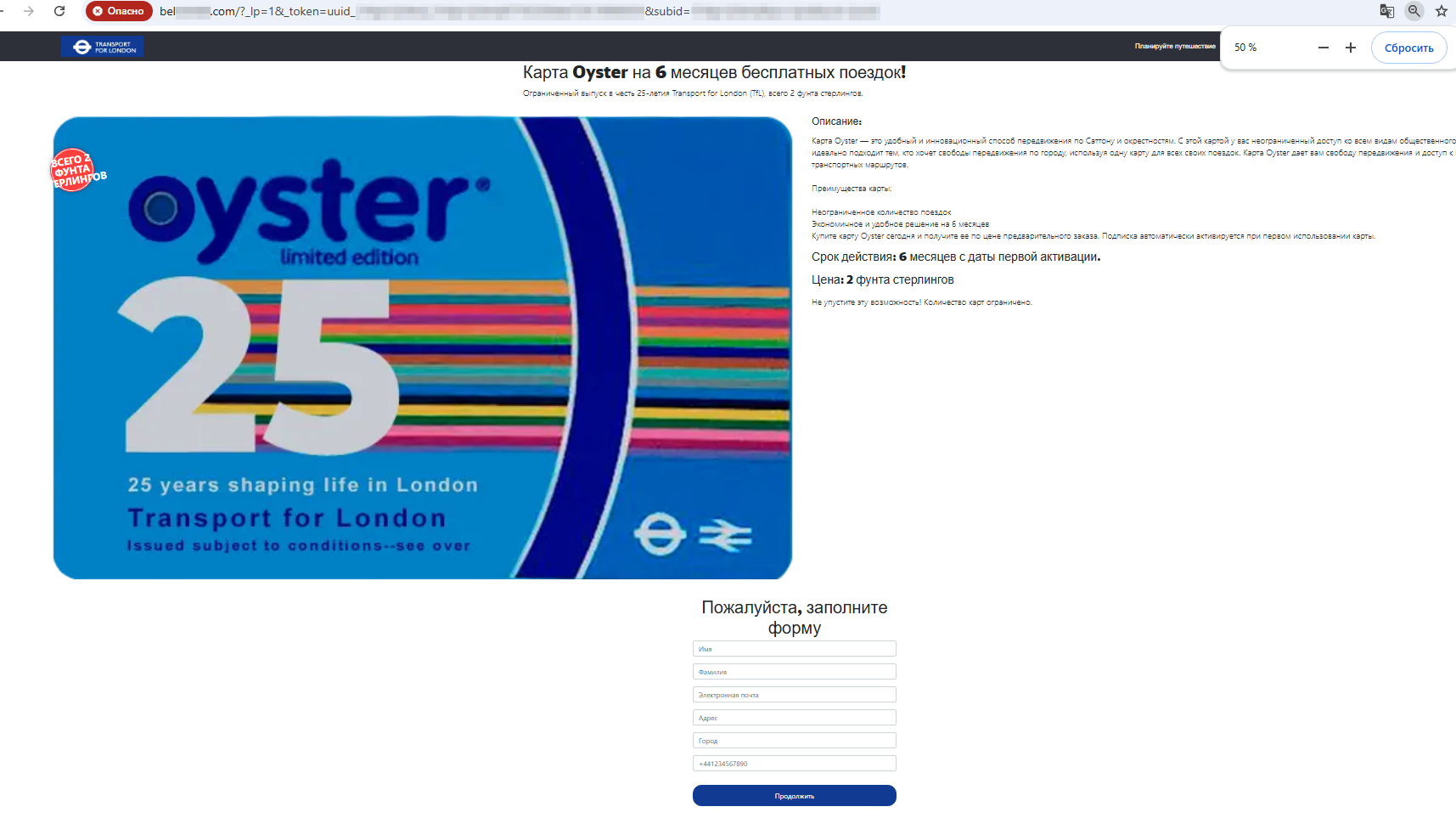
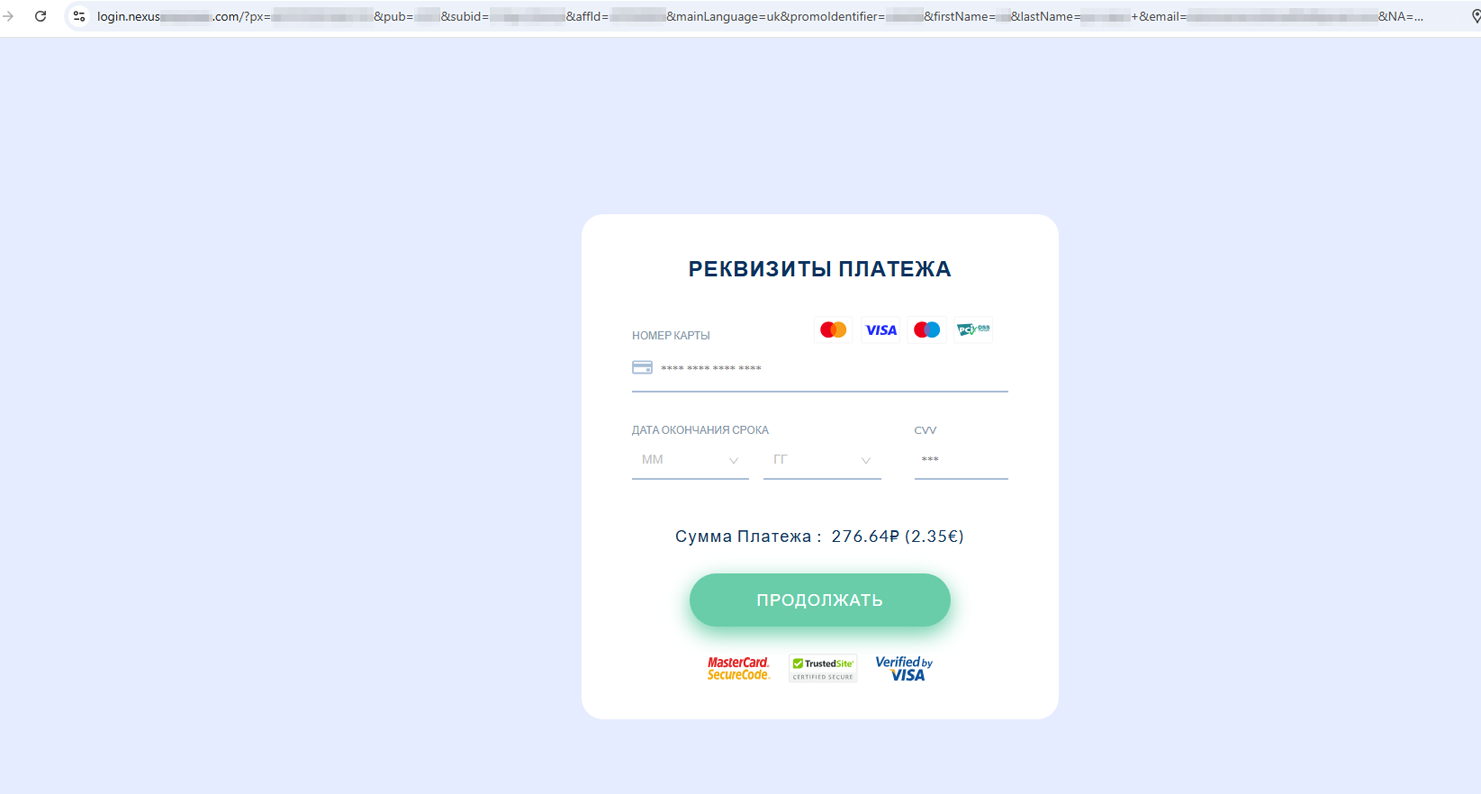
Users had to answer several questions and then play a game by opening virtual gift boxes (the “winning” box in such scenarios is hardcoded). After “winning”, users had to provide personal information and pay £2 to “receive” the promised card. As a result, the victims’ personal information and money ended up in the hands of threat actors.
A potential victim has allegedly obtained a card successfully from one of the game boxes, and in order to receive it, they must provide personal data and also pay £2
A form for entering bank card details to pay for a non-existent promotional transportation card
Fraudsters continue luring potential victims with all sorts of trading platforms that have “unique” algorithms, including ones that are supposedly based on artificial intelligence (AI) technologies. At the same time, cybercriminals exploit the names of famous people and hide behind real companies and services, attributing to themselves a connection with them. One popular scenario is based on claims that users can make money with the help of certain specialized services from Telegram, WhatsApp, and other companies.
Some of these fraudulent sites were advertising various AI platforms, such as Telegram AI and WHATSAPP AI, which allegedly could help users make at least €14,000 per month, thanks to an “automated trading system”:
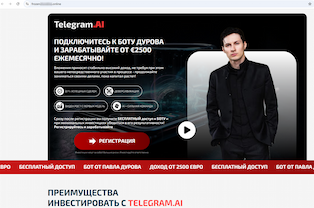
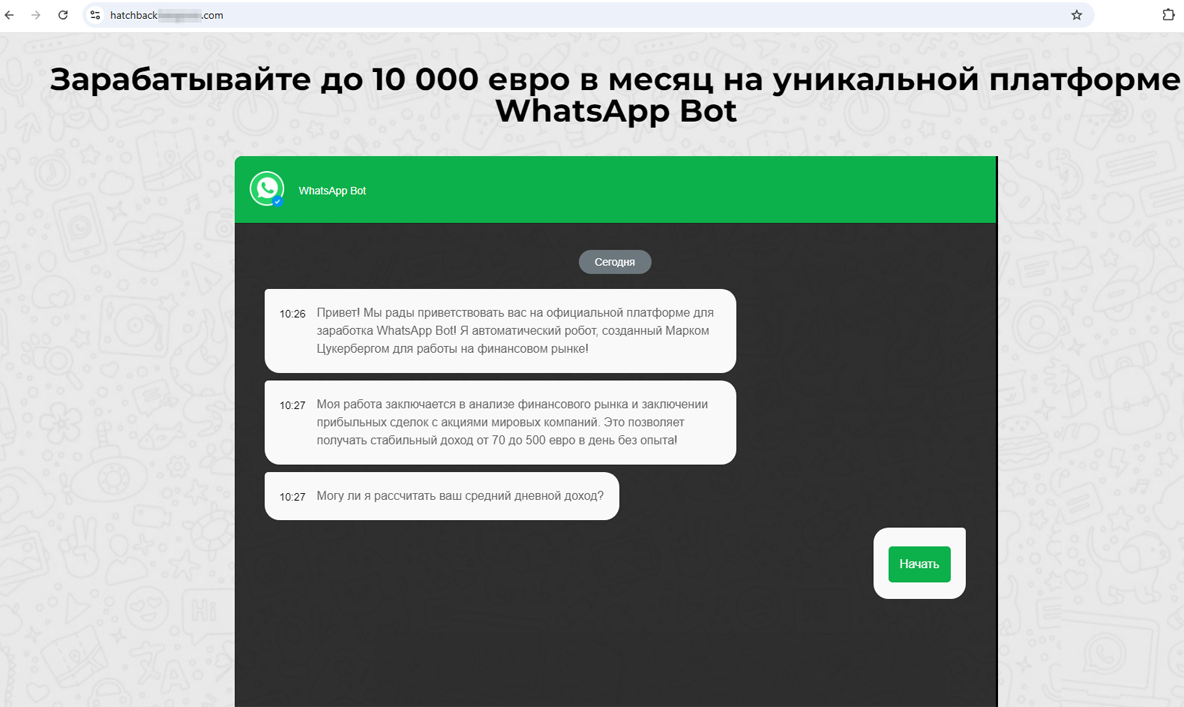
Other variants exploited the theme of trading bots, which are commonly passed off as instruments created by the messengers’ owners themselves. One website, for instance, promised that “Pavel Durov’s bot” Telegram.AI would allow users to earn €2,500+ monthly; and another one offered the option to use the WhatsApp Bot, supposedly created by Mark Zuckerberg, to make up to €500 per day.
Another scam website offered users the option to register on a “Telegram platform” that allegedly runs directly from a smartphone browser, automatically trades shares of global companies, and earns €10,000 per month:
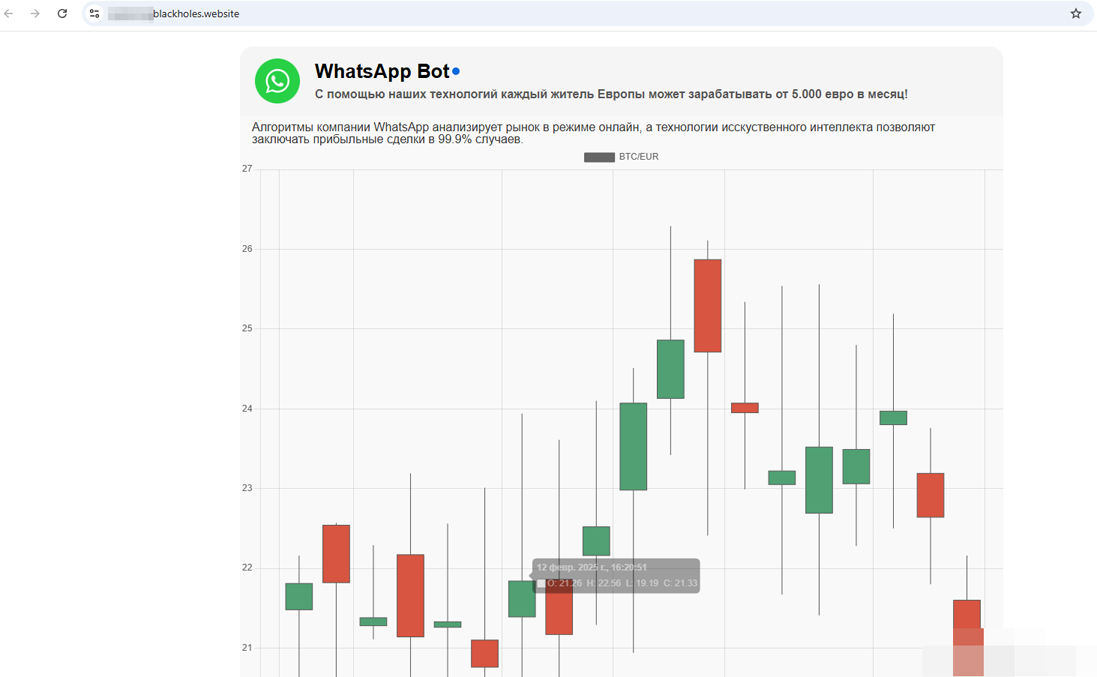
One website promised “every Europe resident” an income starting at €5,000 per month with the help of certain AI-based algorithms from the WhatsApp Company:
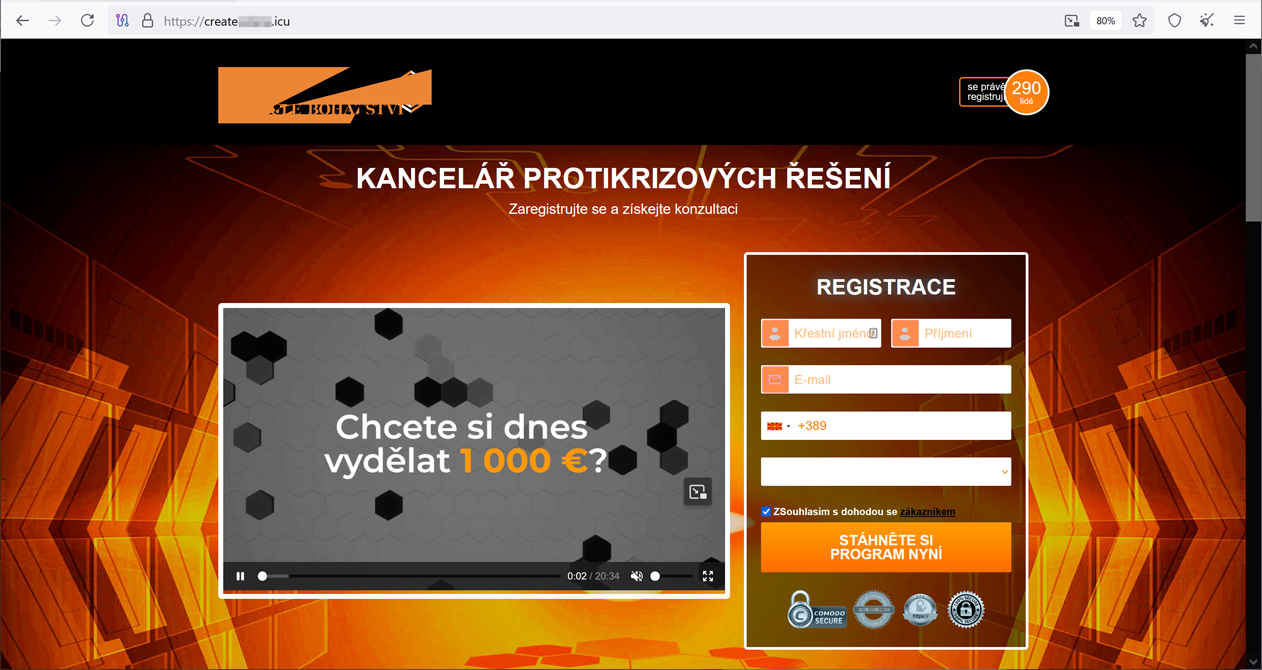
Scam platform “The wealth formula” (“Formule Bohatstvi” in Czech), with its fake AI-based trading system, is a popular variation of this fraudulent scheme. It supposedly makes trades in a split second by analyzing huge amounts of data. Different sites of this non-existent system invite visitors to watch an informational video and register an account for consultations in the “anti-crisis solutions office”. The fraudsters are mainly targeting Europeans—Czech users in particular— who are promised an income of €1,000 per day “for life”. To access the system, potential victims are required to make a minimum deposit of €250.
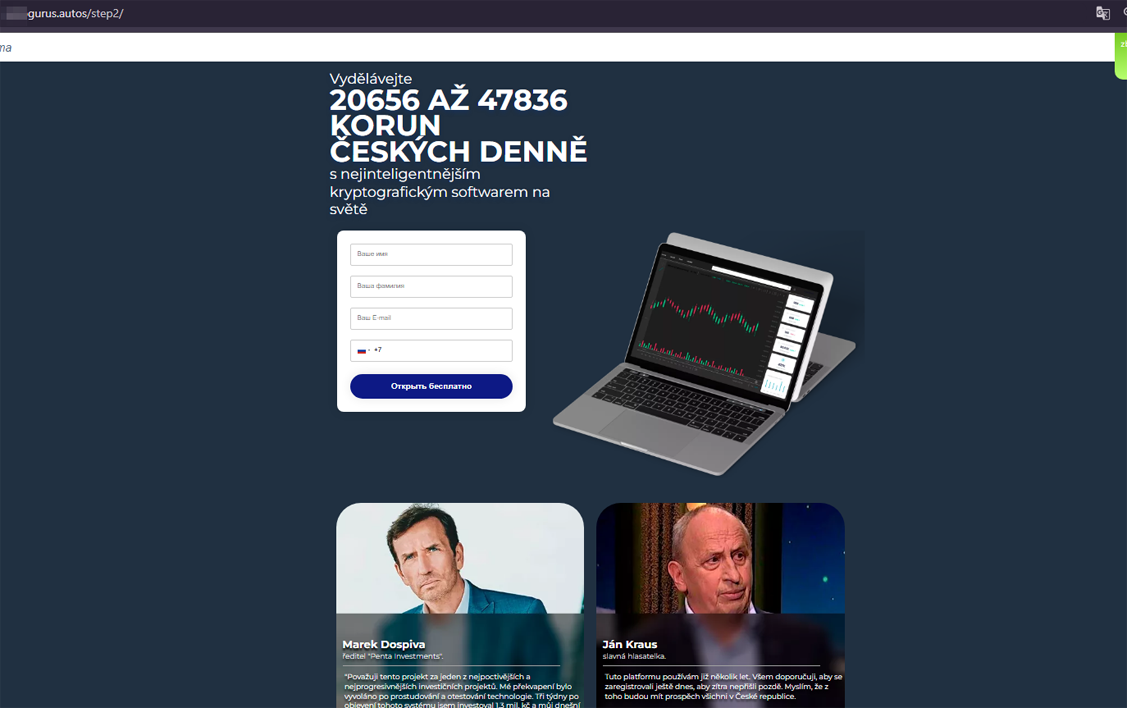
Other similar scenarios, such as generating income using various specialized software, also remain popular. One such website invited Czech users to make thousands of crowns per day with “the world’s most intelligent cryptographic software”:
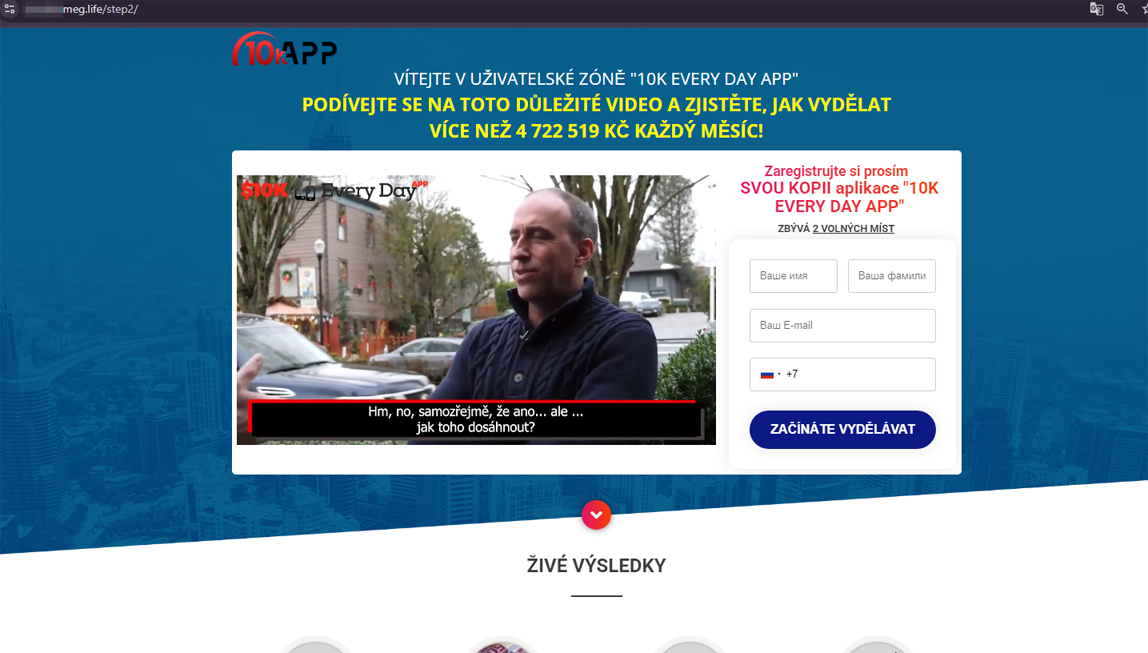
Another scam Internet portal promised earnings of over 4.7 million crowns monthly using certain trading software known as «10K EVERY DAY APP»:
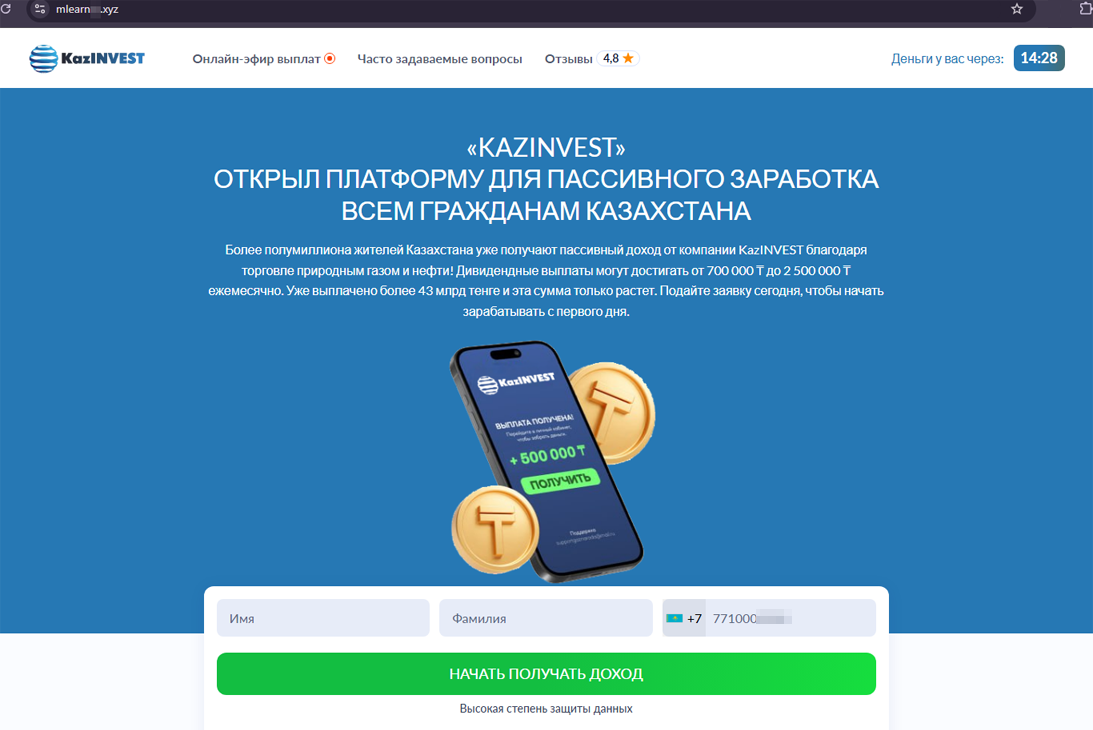
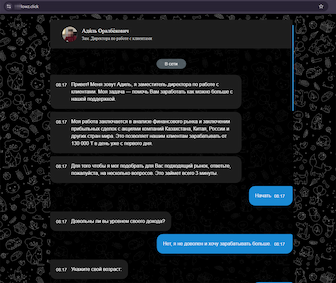
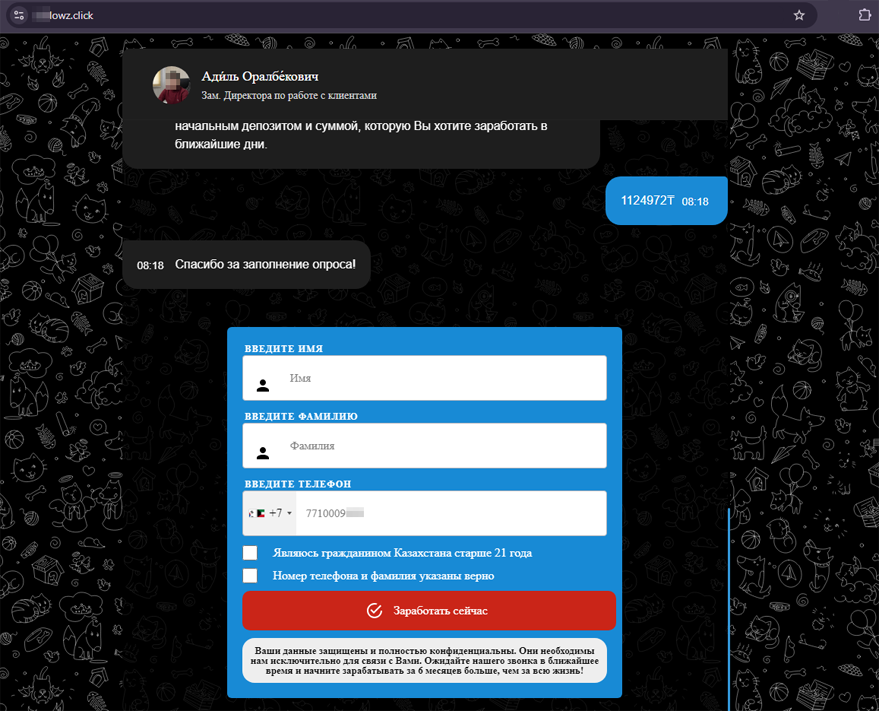
At the same time, users continued encountering fake investment-themed websites targeting residents of different countries. For example, for an audience from Kazakhstan, fraudsters prepared yet another platform for earning passive income through oil and gas trading:
Many other sites offered the opportunity to “earn as much as possible” by trading shares of companies in Kazakhstan, Russia, China, and other countries:
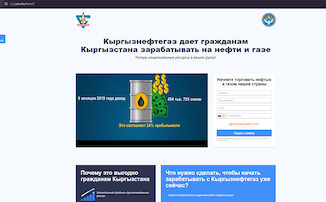
Russian and Kyrgyz residents also encountered similar websites; on these, users allegedly could make money by trading oil and gas:
And one scam Internet resource offered Romanian users the chance to join the BRUA pipeline project, promising 3,000 lei per week as passive income:
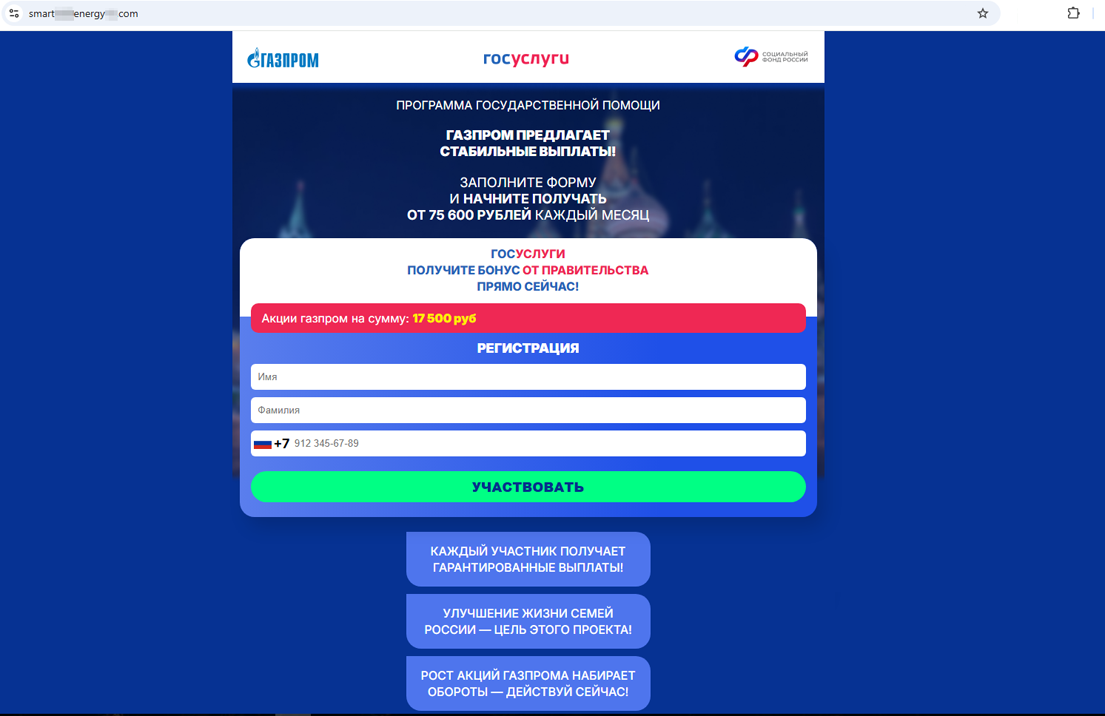
Sites that promise government support to the population in the form of benefits, social payments, etc., remain a lure for potential victims. Threat actors, for instance, tried to bait Russian users with more fake Gosuslugi web portals. One asked them to provide personal data—supposedly to participate in an oil and gas company payment program and also to receive bonuses from the government:
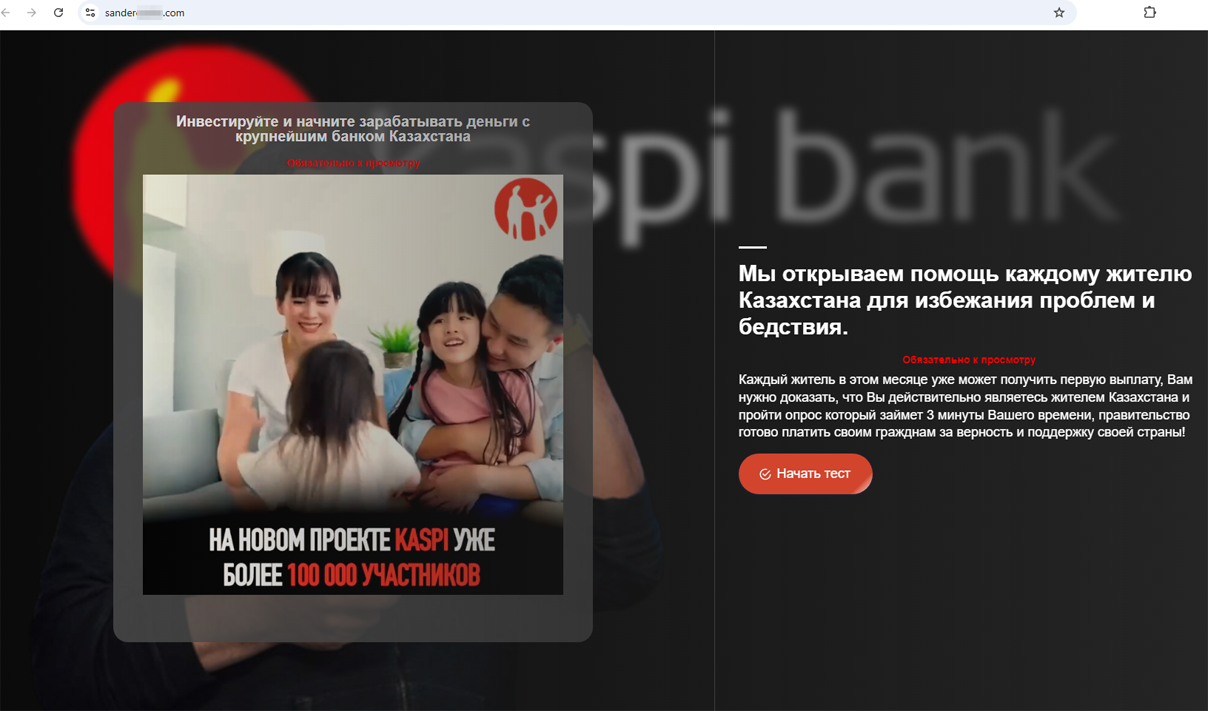
Another scam site promised every Kazakhstan resident assistance in the form of money payments. It was allegedly organized on behalf of a large bank to “avoid problems and disasters”:
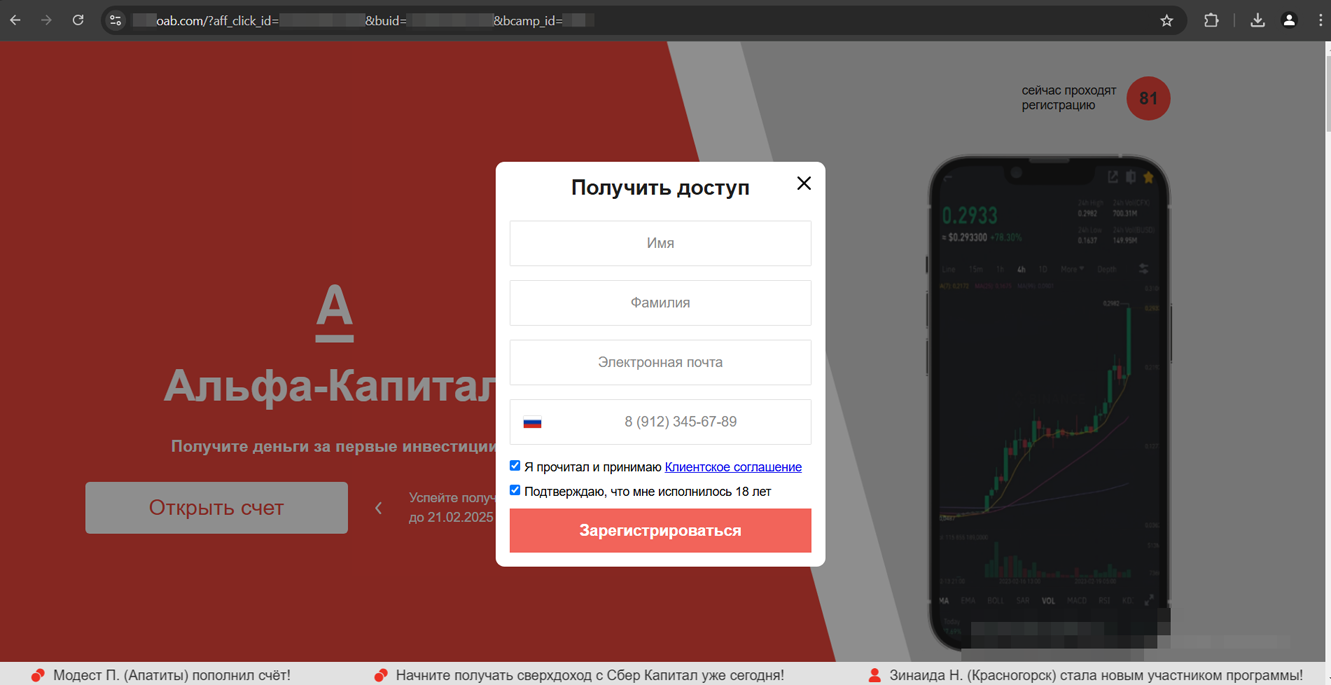
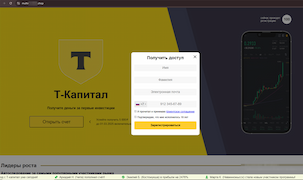
Fake investing service websites, including those supposedly belonging to Russian credit organizations, are still a problem. Many of them mimic real bank websites in order to confuse potential victims as much as possible.
Examples of fake Russian bank websites offering access to “investing services”
Malicious and unwanted programs for mobile devices
According to detection statistics collected by Dr.Web Security Space for mobile devices, in Q1 2025, Android.HiddenAds and Android.MobiDash ad-displaying trojans, along with Android.FakeApp malicious fake programs, were the Android threats most commonly encountered; their activity increased, compared to the last quarter of 2024. In addition, users progressively encountered Android.BankBot and Android.Banker banking trojans. In contrast, Android.SpyMax spyware trojans, whose attacks increased in number almost every month in 2024, were detected less frequently.
Our specialists once again discovered many threats on Google Play. Among them were trojans used in various fraudulent schemes, cryptocurrency-stealing malware, and adware trojans.
The following Q1 2025 events involving mobile malware are the most noteworthy:
- Android.HiddenAds and Android.MobiDash adware trojan activity increased.
- Android.BankBot and Android.Banker banking trojans were more active.
- The number of Android.SpyMax spyware trojans attacks declined.
- New threats were discovered on Google Play.
To find out more about the security-threat landscape for mobile devices in Q1 2025, read our special overview.